Cloud computing has proven revolutionary for organizations hoping to leverage technology, innovation and digital strategies to stay ahead of the competition. Business units can quickly provision up compute, storage and network resources as they need without IT bottlenecks. But easy access to cloud resources has a dark side—one that’s become a growing problem: Shadow IT. Engineers, developers and even business stakeholders are launching resources that IT is unaware of. And what IT doesn’t know can come back to haunt organizations, preventing the IT department from performing critical functions such as controlling security, compliance and costs.
Securing the content supply chain for media and entertainment companies in the cloud
The creation and delivery of media using cloud infrastructure is a paradigm shift, and one of the most significant technological changes the media and entertainment (M&E) sector has seen in the last 2 decades. The ease of delivering content to all consumer screens combined with the increased rate of innovation are the main reasons many M&E companies are increasingly adopting cloud technologies. Increasingly demanding global consumers are another driver.
M&E specific cloud solutions include ingest, storage, transcoding, animation tools, and media asset management, as well as other related services such as metadata, closed captioning, and subtitling services. The cloud enables remote content storage in a connected environment, addressing storage demands such as high throughput and capacity as well as increasing the availability and reach of the content. With transcoding, the cloud helps in repurposing content on a variety of devices, thereby improving content delivery across all channels. Advertising is another related critical component which is benefiting from cloud adoption.
Accenture names the following as benefits of cloud adoption for the M&E industry:
- Faster speed to market, which closes the gap on the faster service delivery cycle of the OTT entrants
- Scalability to handle spikes in workload, including live events, and surges in the popularity of new services
- The ability to collect, store and conduct analytics on vast amounts of data, generating insights to drive personalization, service development, customer experience, and one-to-one relationships
- Driving ongoing service innovation through agile development, constant iterative experimentation, and a culture of “fail fast and fail cheap—then move on”
However, cloud adoption doesn’t come without its challenges. In 2017, an IDG survey identified the top 3 challenges that M&E companies face when adopting public cloud technologies:
- Data storage (43%)
- Cloud security (41%)
- Vendor lock-in (21%)
Why is cloud security a challenge?
Security in the cloud requires the complete rethinking of how to approach security. Cloud security in the context of content supply chain is vital for M&E companies to consider. With the enormous amount of content that can now be produced, stored, processed, or distributed in the cloud, and the immense value of this content, it becomes critical to understand how to have the proper controls in place from day one of your cloud journey.
Companies often need to upskill their team or bring new team members on board with specific cloud architecture and deployment expertise, develop new processes, and support these processes with new tools that allow scale through automation.
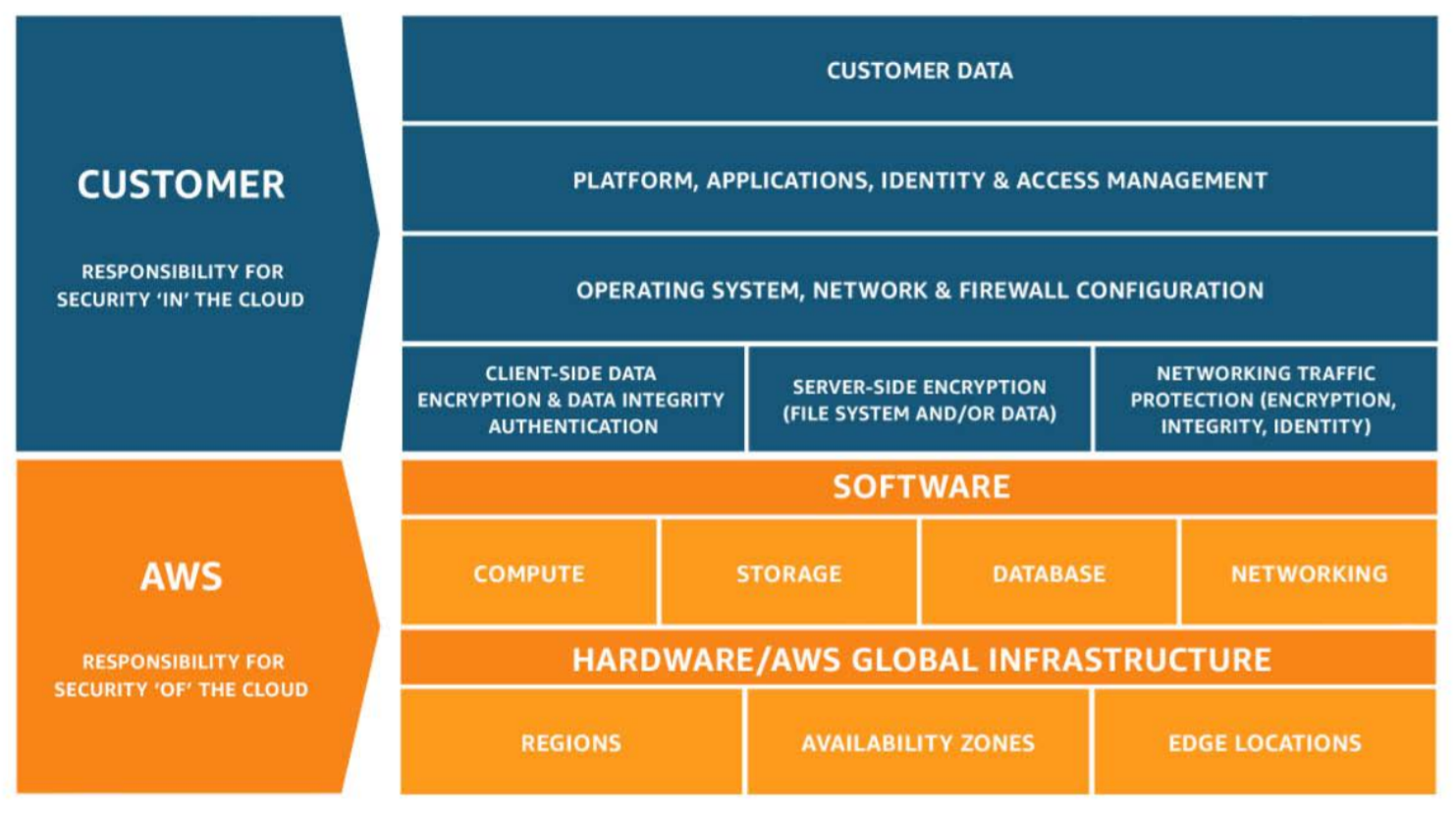
Cloud providers like Amazon Web Services, Microsoft, and Google operate their clouds in a shared responsibility model. The cloud provider is responsible for managing the security of their infrastructure, but they provide the customer with the flexibility to configure their cloud services as they see fit. It is also the responsibility of the customer to configure Identity and Access Management (IAM) for their users. The customer has the responsibility to configure and manage these services in a way that meets their security and compliance standards. This split is commonly referred to as security “of” the cloud (provider responsibility) versus security “in” the cloud (customer responsibility.) The following diagram from AWS illustrates the shared responsibility model and identifies the customer’s responsibility to manage their data.
One of the most significant challenges in managing data security is the desire to embrace the self-service nature of software-defined infrastructure that the public cloud provides. Media and entertainment companies like Turner and Discovery have driven corporate innovation by taking full advantage of the public cloud. These digital leaders have embraced self-service, giving dozens if not hundreds of developers and engineers access to their public cloud infrastructure. This access has created the opportunity for rapid and low-cost experimentation, and the ability to scale rapidly when innovation strikes success. Increasingly, these digital leaders are also embracing multi-cloud infrastructure to provide access to best-of-class services, avoid vendor lock-in, and improve the resiliency of applications.
Providing a large population of developers and engineers with the ability to provision and configure cloud resources and services can seem like a scary proposition. After all, this general population is unlikely to be well-versed in the security, compliance, and governance standards of your company, and even less likely to know how to implement these standards consistently across one or more cloud providers.
This gap in knowledge and skills results in misconfigurations that open companies to leakage of data that can range from content to customer data. Take one small example of the Amazon S3 cloud storage service and how often it is misconfigured. According to a recent reporting, 7% of all Amazon S3 containers are fully publicly accessible without any authentication, and 35% of these are unencrypted. This type of misconfiguration has real and substantial consequences. In the last few years, there have been numerous high-profile breaches that were the direct result of misconfigured Amazon S3 buckets.
Cloud computing architecture trends are driving up the level of complexity and therefore the risk of operating in the cloud. As more companies embrace serverless and containers as their standard approach, this begins to increase the complexity of the configuration footprint. When you move to a collection of microservices that make up an application, a misconfiguration of any one of those microservices may open the application and the data to exploitation.
Data security issues can plague even the largest and most sophisticated organizations. Twenty-eight percent of media organizations report having experienced some form of cyber attack, and that self-reported number is likely on the low end.
M&E companies are particularly attractive targets, not only by those who want to steal the content for financial gain, but even by state actors who have an axe to grind (see Sony “The Interview” hack). The content they produce is worth millions if not billions, and there are lots of people trying to get access to it. Breach incidents in the M&E sectors are growing year over year.
According to the 2017 Breach Level Index Report, the entertainment industry’s compromised accounts slid 91.8% from 419,864,632—the highest of any sector in 2016—to 34,484,948 in 2017. However, incidents grew during that same period by 48.4% percent, from 31 to 46.
So what can M&E companies do to take advantage of the cloud and maintain the security of their intellectual property?
Get to know your data. Identify what data your company is processing. Document your data flows, including inside of third- or fourth-party vendors. Don’t let your third-party or fourth-party vendors and services be black boxes. Dig in and don’t take no for an answer until you fully understand the ins and outs of your data flow. Find out if you need all the data you are collecting and classify all your data, so you know the associated risk level.
Make security and governance the foundation of all your decisions. With the massive risk associated with data leakage and possible fines levied for non-compliance, security and governance can’t be an afterthought. These ideas must be foundational when designing applications and the underlying infrastructure. Your strategy needs to be holistically included in all elements of the application design, development, and testing, and can’t be relegated to an occasional review by one team. Everyone on the team—developers, UX, marketing, legal, product management, etc.—needs to be thinking about security and governance. Require third parties to comply with standards if they use the cloud, such as the Studio Security Controls for VFX Rendering published by Amazon Web Services.
Don’t reinvent the wheel. In the cloud, the shared responsibility model means that there are lots of ways to poorly configure your cloud applications and underlying infrastructure. Don’t reinvent the wheel and try to figure out baseline security from scratch. Standards like National Institute of Standards and Technology Cybersecurity Framework (NIST CSF), Center for Internet Security Benchmark (CIS), NIST 800-53, and Studio Security Controls for VFX Rendering offer excellent starting points. For example, “out of the box,” these standards will highlight items like misconfigured S3 buckets (e.g., ID.RA-1: Asset vulnerabilities are identified and documented). Often companies choose to create their standards, borrowing from one or more existing standard.
It is also essential to stay on top of updates to these standards. For example, NIST CSF 1.1 was just released in April 2018. Updated standards are critical because they often represent significant advances in addressing emerging cybersecurity challenges. For example, NIST CSF version 1.1 included updates to authentication and identity, self-assessing cybersecurity risk, managing cybersecurity within the supply chain, and vulnerability disclosure. Another compliance standard, SOC 2 (Service Organization Control), developed by the AICPA, is specifically designed for service providers storing customer data in the cloud.
NIST 800-53, SOC-2, ISO 27001, ISO 27002, and PCI v3.1 help form the basis of the Motion Picture Association of America (MPAA) best practices guidance and control frameworks which assist major studio partners and vendors in designing infrastructure and solutions to ensure the security of digital film assets.
Implement automation. In the software-defined microservice world of the cloud, the rate of change and scale has outstripped the ability of a person, team, or even a company to keep up manually. This is especially true as it applies to security and governance. Studies have repeatedly demonstrated that companies that rely on manual enforcement and remediation get caught in a vicious cycle, oscillating between compliance and non-compliance. It is vitally important to define processes based on standards and then deploy systems that allow you to automate enforcement of these standards. In this way, you can maintain a consistent security and governance posture.
InsightCloudSec is an excellent example of a solution that companies like Discovery, Turner, Mediacorp, and Sky TV New Zealand use to govern their cloud infrastructure securely. Watch the demo to learn more.