Defaultinator: An Open Source Search Tool for Default Credentials
Curt Barnard, Principal Security Researcher, Rapid7
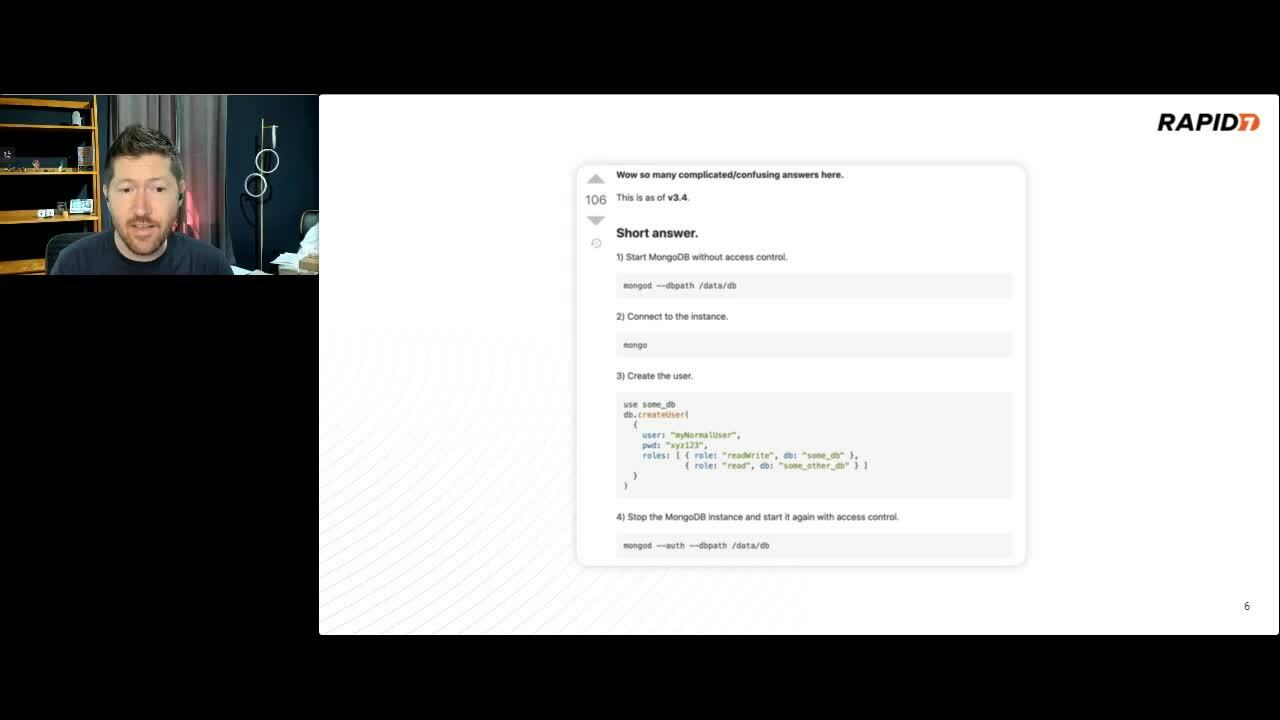
Have you ever had to Google around trying to find a default password for a router? Are you sick of combing through user manuals just to find admin:admin buried on page 37. Then it's time you tried Defaultinator. This newly released tool is a repository for default credentials made searchable via API or the intuitive web interface. Why would someone make such a tool? Why, I'm so glad you asked!
The Metasploit Framework
Spencer McIntyre, Lead Security Researcher, Rapid7
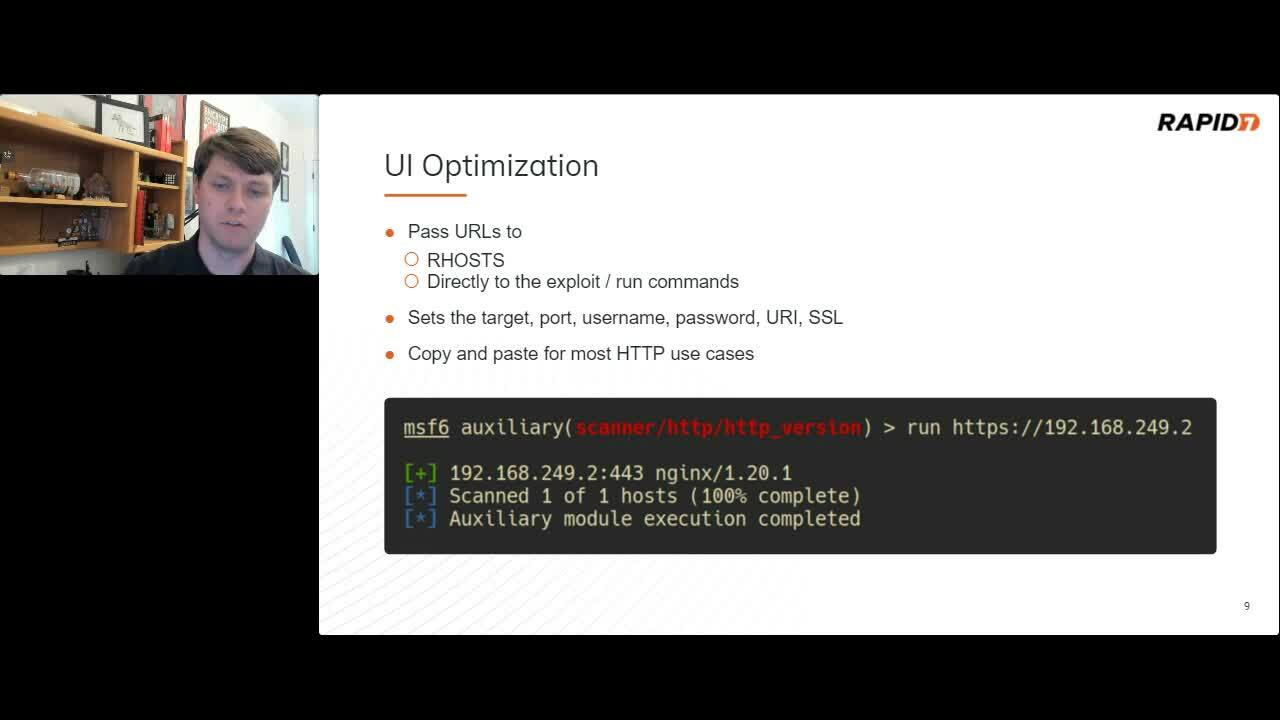
Modern attack emulation is a multi-step process involving different tools and techniques as testers execute custom workflows to achieve their objectives. One primary advantage of the Metasploit Framework is a unified approach to solving this problem.This Arsenal demonstration will cover some of the latest improvements to the Metasploit Framework and showcase how these improvements maximize effectiveness while performing common tasks.
Brick a Car Instead of a Phone
Patrick Kiley, Principal Security Consultant and Research Lead
Patrick Kiley will show us how he bricked both a BMW E90 Chassis and a Tesla P85D.
The Ransomware Task Force and Government Responses to Cyber Extortion
Jen Ellis, Vice President, Community and Public Affairs
Watch this session to learn more about the ransomware task force, the RTF framework, and how the US government is responding to the threat of ransomware, including regulation for cryptocurrency.