The Challenge
A customer of DivvyCloud by Rapid7 in the financial technology sector wanted to embrace AWS so they could launch their regulated financial service more quickly. Doing this required that they adhere to SOC 2. They didn’t know how to incorporate this framework, but understood that approaching it manually would be expensive and difficult.
As a result, the customer’s CIO and CISO decided to architect their AWS strategy in a way that would allow them to achieve and maintain SOC 2 compliance, Types I and II, continuously. This customer is a highly regulated fintech solution provider, and SOC 2 compliance would allow their customers to adopt their solutions more rapidly. Their primary objective for maintaining compliance was to automate tasks and remediation to keep their teams small and lean.
The Solution
As a starting point, the customer focused on DivvyCloud by Rapid7’s out-of-the-box AWS CIS Compliance Pack, with the additional layer of SOC 2 applied to relevant workloads in their cloud environment. Through the existing Insight Packs for SOC 2 and CIS, the customer was able to create their own custom pack and validate their cloud account setup and security posture.
The fintech customer confirmed that their AWS cloud accounts achieved SOC 2 compliance. The Compliance Scorecard below showcases the measurement of how they ran their cloud accounts in production through SOC 2 and CIS Insights.
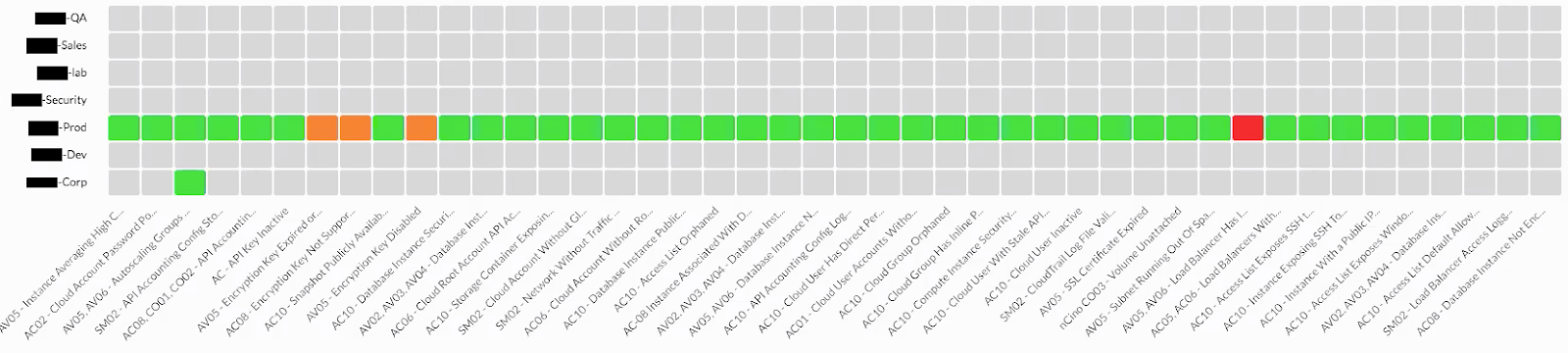
The customer configured DivvyCloud to send notifications for any red cells (areas of noncompliance) to the appropriate account or cloud resource owners for action. The Compliance Scorecard’s value and audience goes beyond security and compliance professionals. The customer's C-level executives use the Scorecard to get a high-level view of how well the company is running its clouds in production. In addition, the customer often uses the Compliance Scorecard to showcase this view to their own customers.
The customer also created custom Compliance Packs using CIS and SOC 2 requirements. Some of the key criteria that they incorporated into their custom Compliance Packs were to only encrypt storage that has sensitive data and application data isn’t stored on an instance (i.e., either it’s attached to a volume/instance and flagged for encryption, or it’s stored at the data layer, such as RDS).
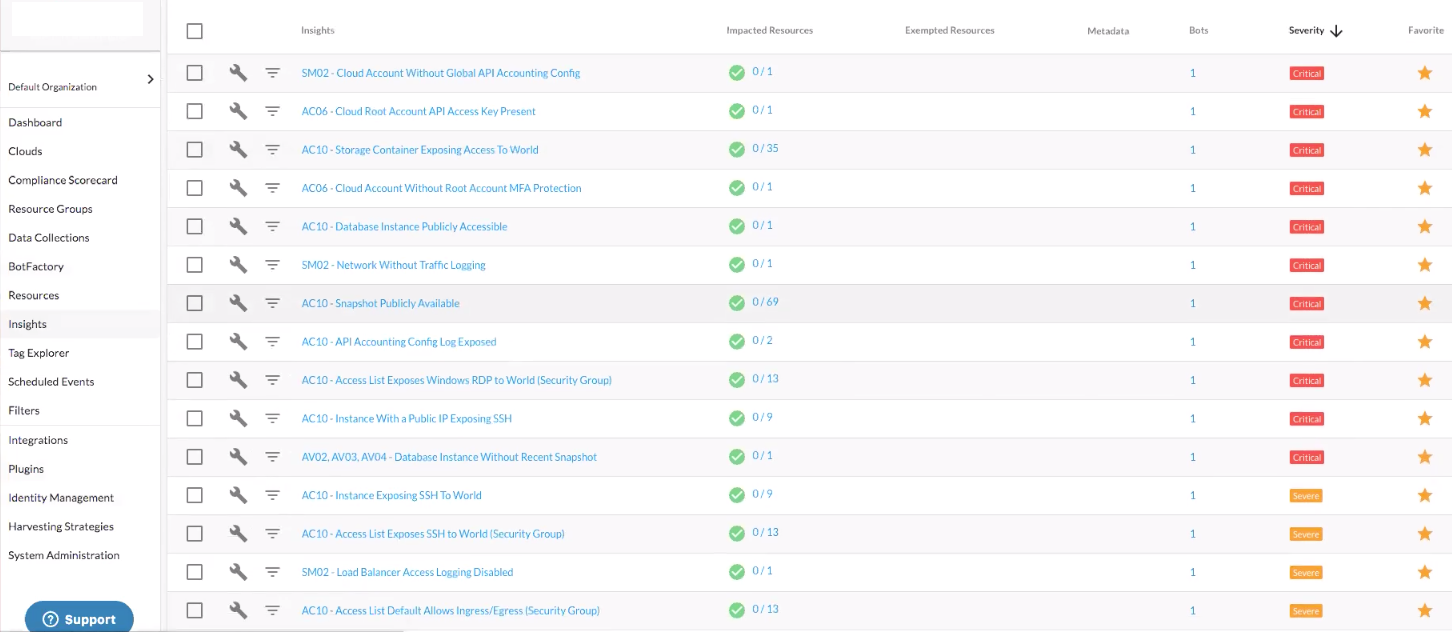
The SOC 2 Insights below translate to enabling dynamic remediation actions, such as retiring and automatically rotating encryption keys.
With the Insight setup, the customer deployed 136 Bots, which allowed them to generate a daily compliance report and send it automatically to the CISO and CIO. Many of the Bots also deploy automated remediation actions.
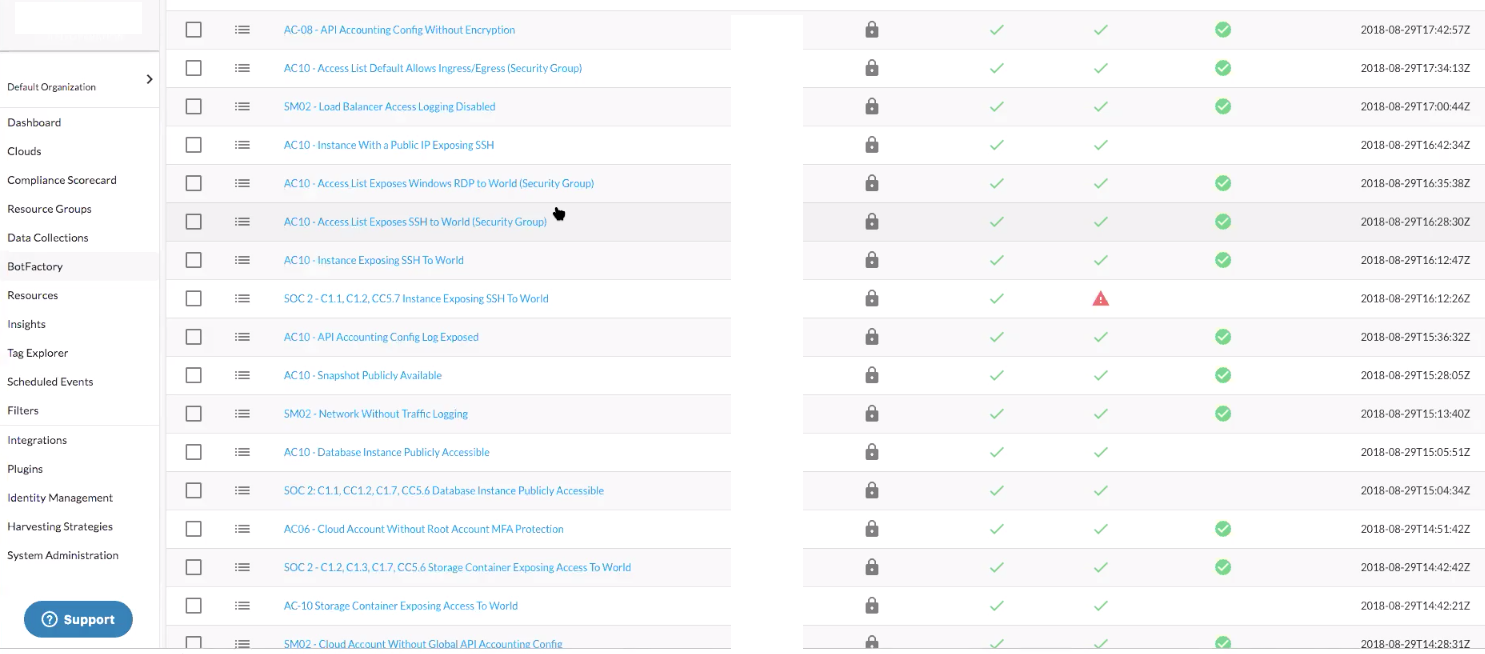
Accounts that are subject to SOC 2 have their own set of Bots that take different actions, as they contain live production applications. Because of this, different actions are defined for these cloud accounts compared to other accounts. For relevant accounts, the organization won’t tolerate a database with an external IP address. The automated action is to delete, notify the owner (customer), and identify whether tagging is enabled.
The fintech customer has a strict tagging policy for production accounts, especially those subject to SOC 2, and tags are deployed through automation. The customer leverages CloudFormation and CircleCI to deploy templates for:
- Any resources that have access to production accounts
- The logging and reviewing of all manual changes
- Accounts being managed by respective account owners
Remediation plans are in place whenever an Insight identifies a violation.
Some of the key use cases that the customer automated to support SOC 2 compliance are:
- Notifications through Slack to the owners of exposed public AWS S3 buckets, and identification of actions to fix the issue through auto-correction
- Rotating encryption keys to reduces the potential impact of a compromised key
- Bot notifications via Slack for development and/or production environment designated team members on the following:
- Running out of storage
- CloudFormation stack cleanup
- IAM policies around direct permissions, API credentials, MFA, password management, orphaned cloud groups, etc.
- Database backups, with a retention policy to enable backup and automate manual snapshots
- Cleanup of resources that are provisioned in regions that are not allowed or supported
- Alerting of unencrypted databases, and mitigation efforts focused on why they were created without encryption
- Enabled automation for deployer keys across all accounts
- Bots in different development environments that run from 7 AM to 7 PM (not enabled 24/7 because it’s an external deployer, and keys are enabled during business hours only)
- For production accounts, keys are deleted after deployment is complete
- Enabled AWS Step function where Bots will monitor any step function failures and notify developers in dev environments, and the operations team in production environments
- Enabled sleeper Bots for SageMaker notebooks—at the end of every day, checks all running instances that aren’t tagged and turns them off by 7 PM
SOC 2 is based on audits against the Trust Services Criteria standards for company maturity around processes and security. The fintech customer automated many of their security compliance checks using DivvyCloud Bots. These Bots enabled the customer to remediate any violations and maintain SOC 2 compliance through DivvyCloud's Compliance Packs.
Terms Appendix
The DivvyCloud by Rapid7 features the fintech customer leverages extensively are: Insights, Bots, Compliance Packs, and Compliance Scorecard.
- An Insight is a pre-determined characteristic, condition, or behavior that is flagged for a cloud resource. Insights provide an in-depth understanding of cloud infrastructure around security and compliance.
- Bots are programs that convert manual workflows to automated programs that allow remediation. Insights are the primary data points for enabling and configuring Bots. Bots come with a set of constructs called filters and actions, which can not only be applied to identify non-secure, non-compliant cloud resources, but applies and identifies remediation plans as well.
- Compliance Packs are a collection of related Insights that are focused on industry requirements and standards for all cloud resources. Their primary focus is around security, cost, governance, or a combination across frameworks such as CIS, GDPR, HIPAA, SOC 2, FedRAMP, PCI DSS, NIST, CSA, and ISO.
- A Compliance Scorecard is a heat map that can assist teams of all types, including auditors, operations, security teams, managers, and executives, to identify areas with compliances issues and provide guidance for acting appropriately on the right resources to mitigate issues.