Executive Summary
Spring is here! The sun is shining, the birds are chirping, and attackers are coming up with more convincing ways to steal user credentials. While fairer weather does not lull attackers into slowing their pace, it does mean that you can at least sit in the sunshine and read our findings from the past quarter before continuing the mission of defending your network against an often persistent, sometimes creative, and always-on-the-job adversary. This quarter's report covers three main areas of concern for the modern IT defender:
User Identity:
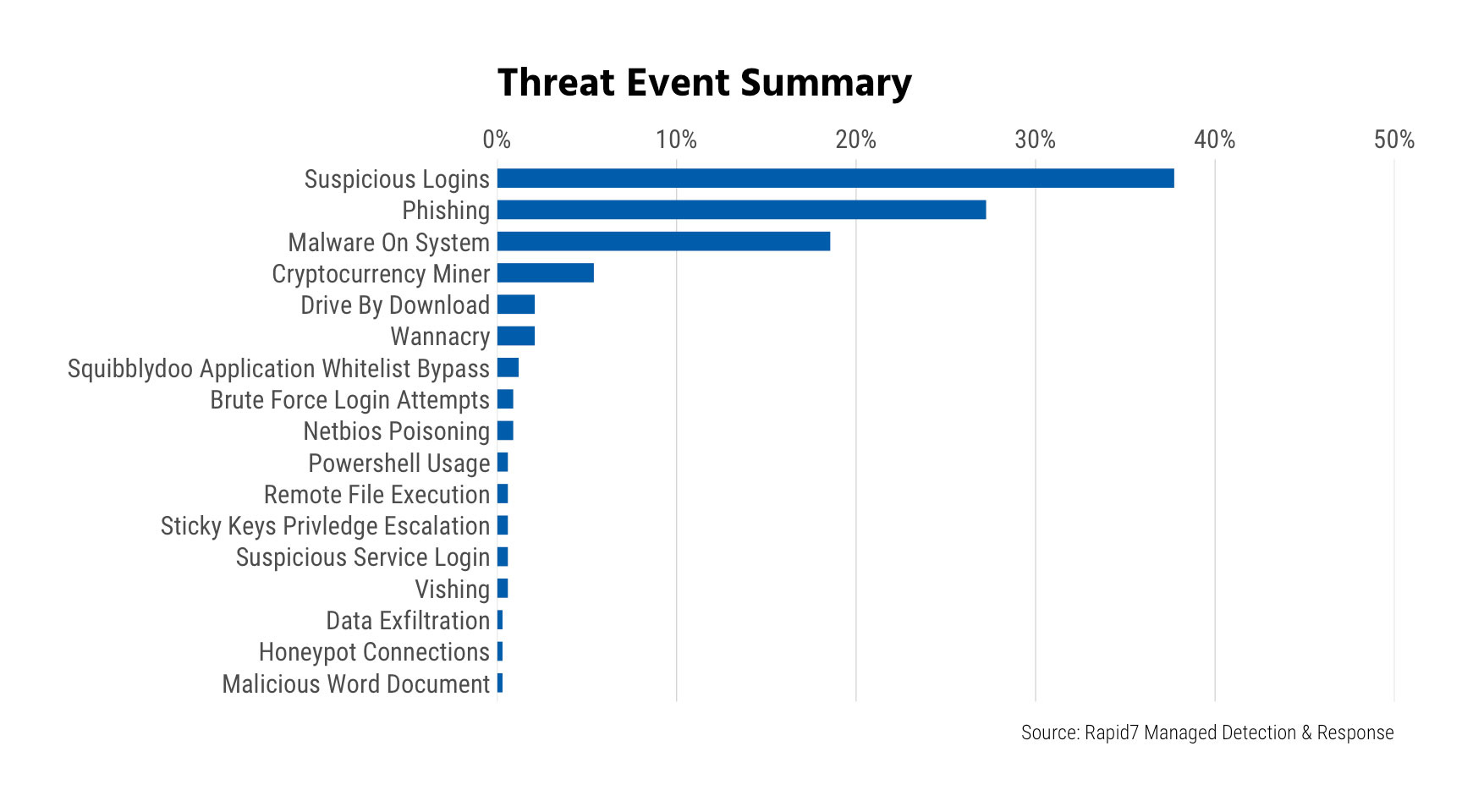
Credential theft, reuse, and subsequent suspicious logins are—today—the most commonly reported significant incident we’re seeing across both small (<1,000 endpoints) and large organizations (≥1,000 endpoints).
DDoS:
The DDoS landscape just got a lot more interesting with the debut of a new technique using misconfigured—and plentiful—memcached servers. The memcached attack on GitHub was a harbinger of things to come for DDoS mitigation practices.
SMB and SMI:
Finally, we take a look at the increasing levels of SMB and Cisco SMI attacker probes and attacks, where the former continues to define the “new normal” level of background malicious behavior around Windows networking, and the latter begins to bring shape to this relatively new attack vector targeting core router infrastructure.
Register for the webcast (May 17, 2 p.m. ET/11 a.m. PT): Hear directly from the researchers on what these trends mean for the rest of 2018.