Executive Summary
Summer is in full swing, and while many people spend these months taking time off to travel, relax, or head to Hacker Summer Camp in the sweltering Las Vegas sun, networks are still at risk and need to be defended. In the second quarter of 2018, we continued to see high levels of activities aimed at identifying and compromising systems of interest, whether the attackers’ plan was to steal financial information or, as we see more and more, steal other sensitive information such as credentials that can be used for a variety of information based operations.
Credential theft continued:
We saw a continued emphasis on credential theft and account leaks across all industries, along with an increase in remote access attempts.
Make way for RDP:
In addition to Microsoft’s Server Message Block (SMB) protocol, adversaries demonstrated interest in Microsoft’s Remote Desktop Protocol (RDP), with many of the access attempts utilizing brute force methods for gaining access.
Burgeoning botnets:
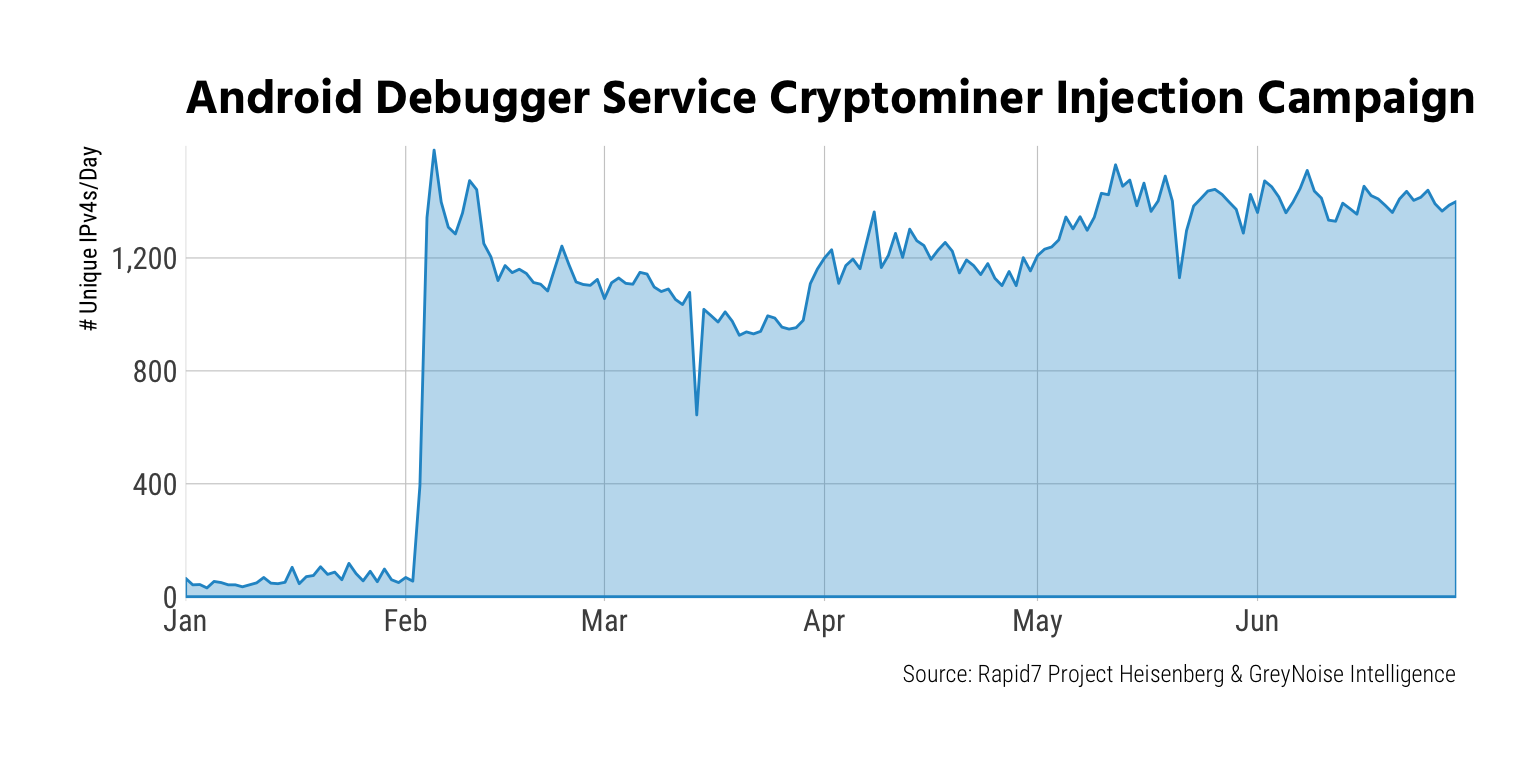
Botnet wranglers definitely did not take any vacation time in Q2. Our Heisenberg honeypot nodes caught numerous attempts to inventory and usurp various devices and services this quarter, including campaigns against a cadre of routers, Android debugger-enabled systems, Drupal, and WebLogic.
Register for the webcast (August 23, 2 p.m. ET/11 a.m. PT): Hear directly from the researchers on what these trends mean for the rest of 2018.