nexpose
Features
What makes our vulnerability scanner better?
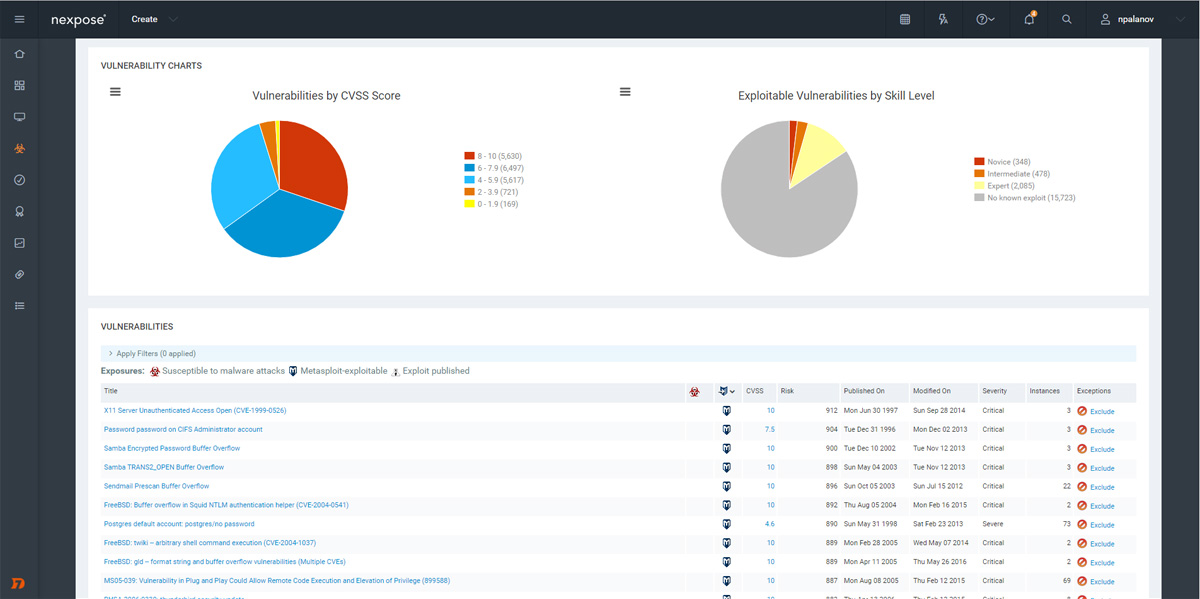
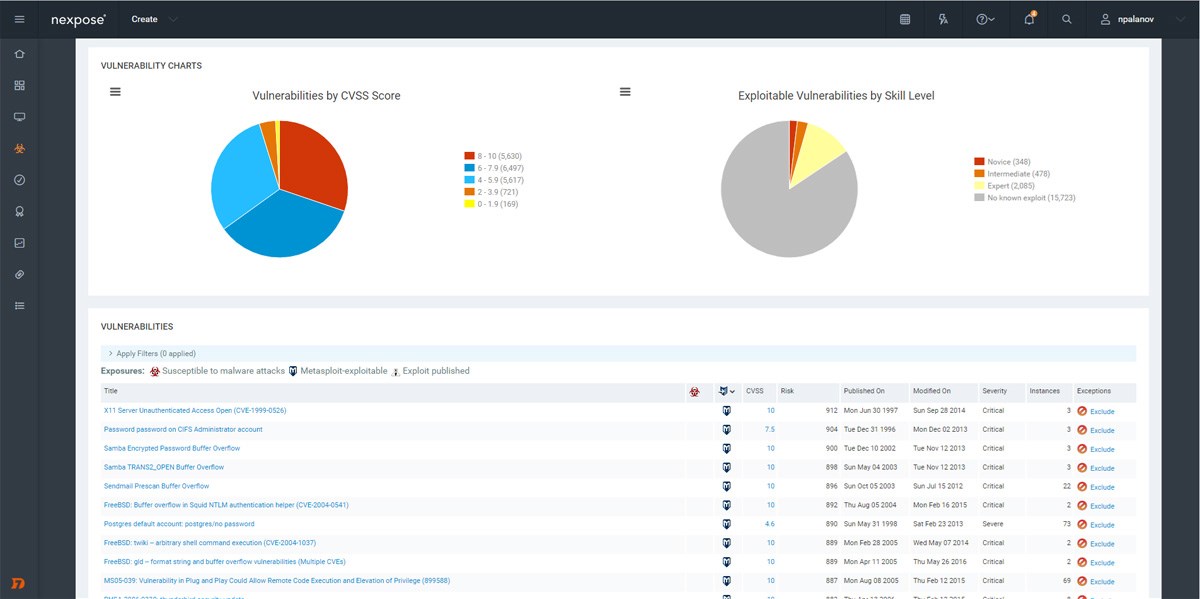
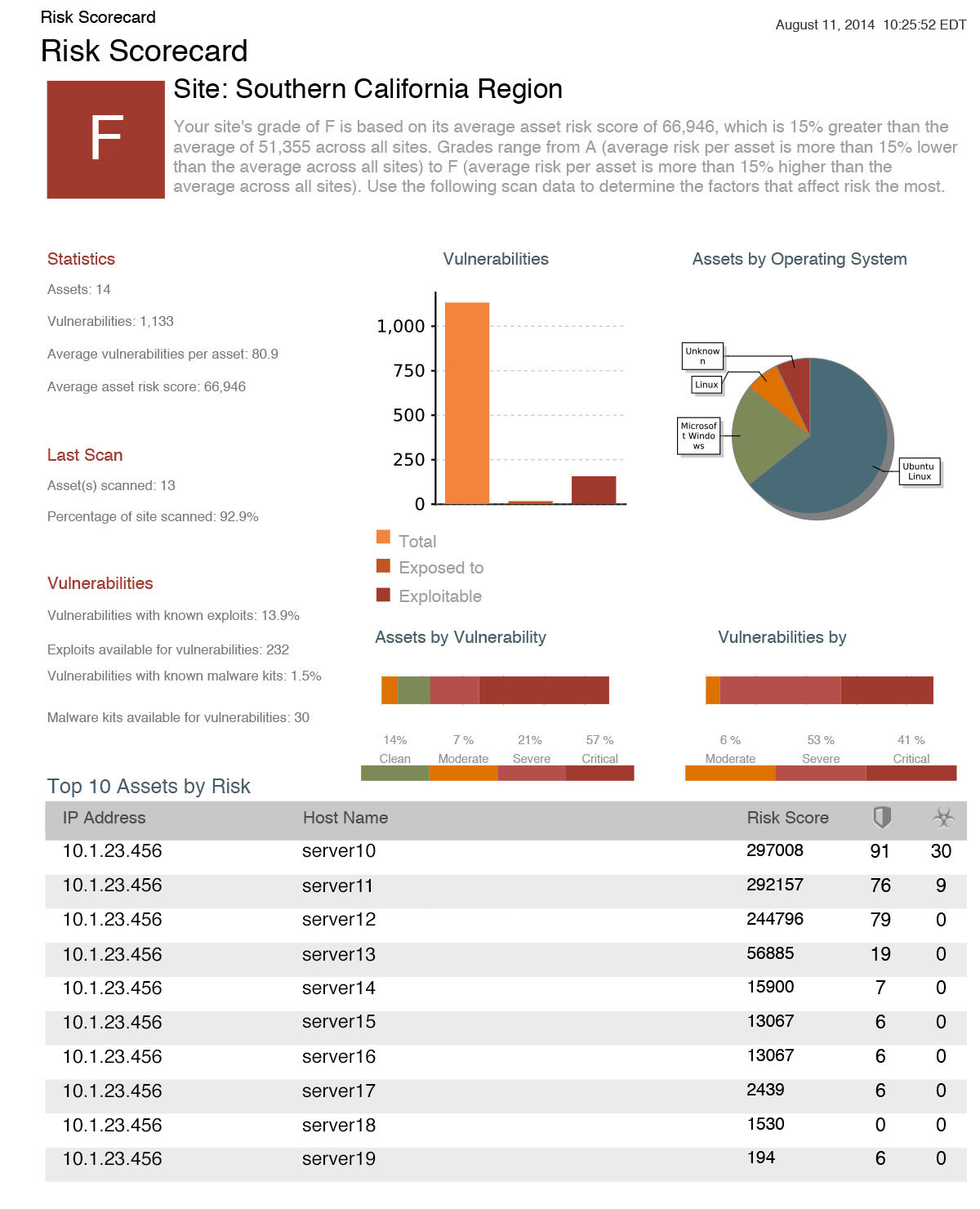
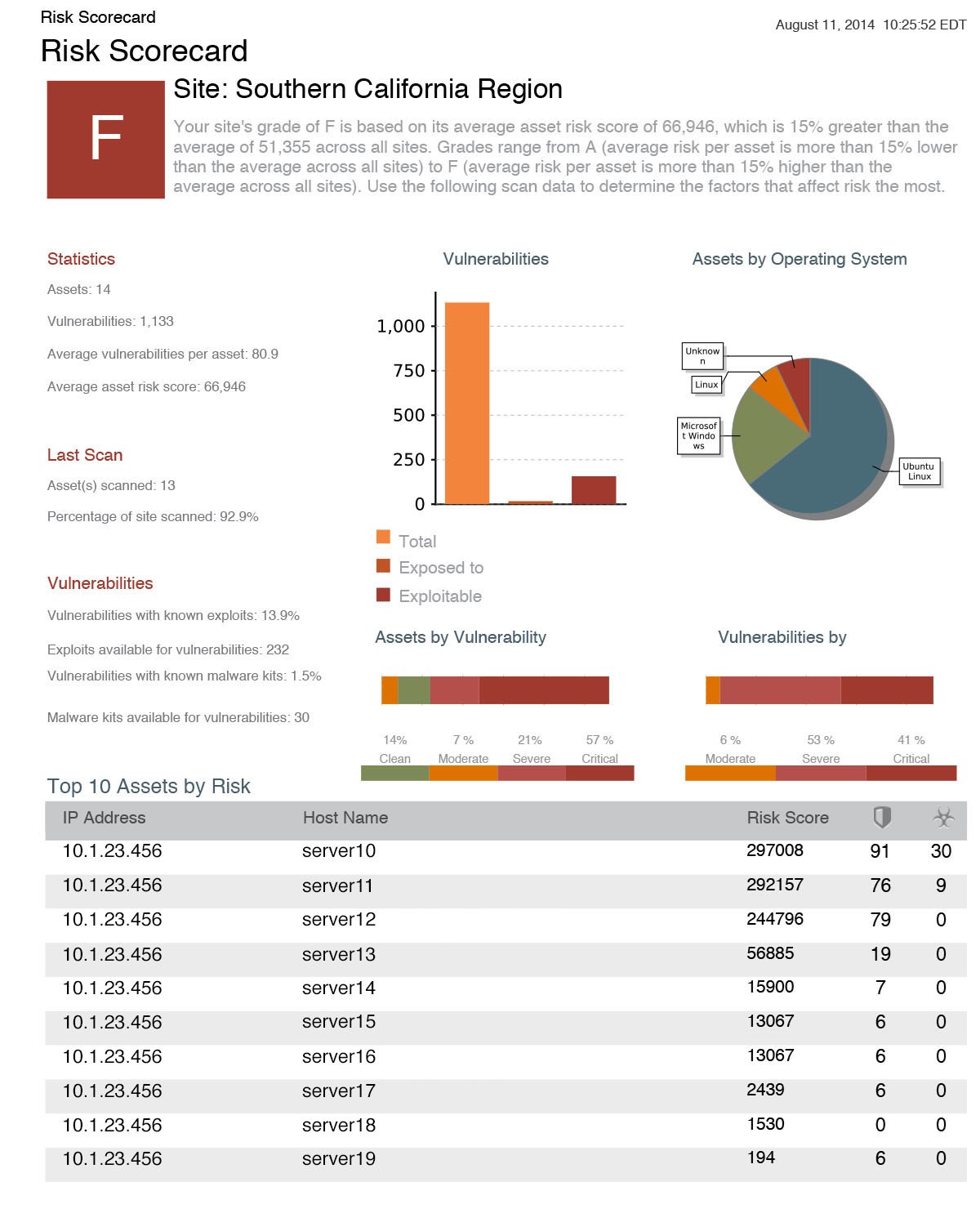
Real Risk Score
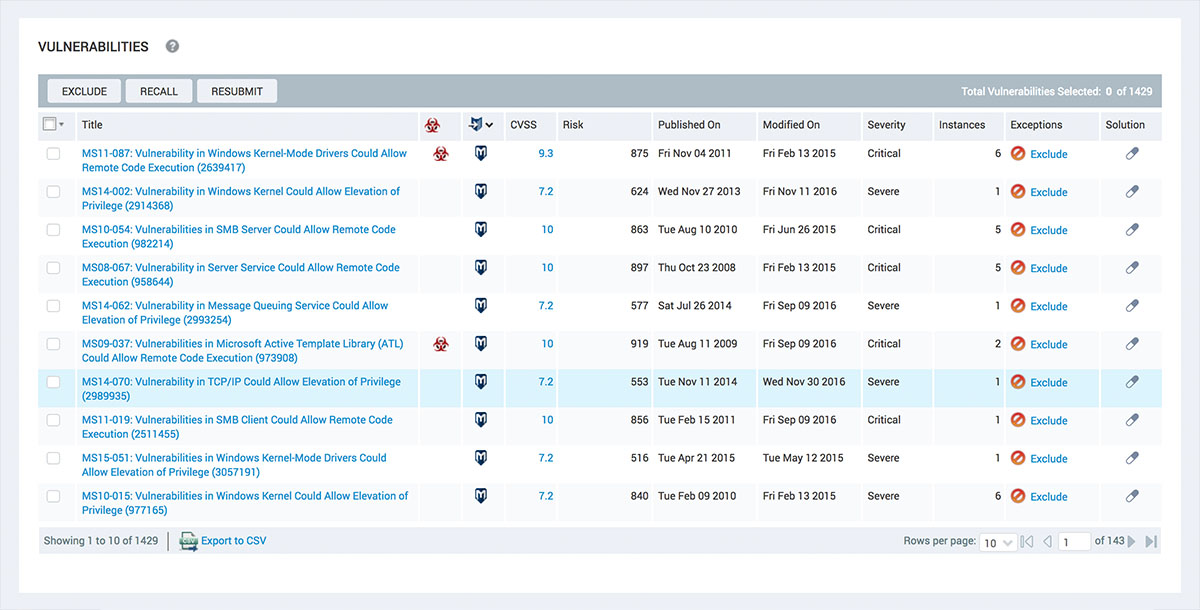
The standard 1-10 CVSS score results in thousands of “critical” vulnerabilities. Our vulnerability scanner's Real Risk Score provides more actionable insight. Taking into account vulnerability age, as well as public exploits/malware kits, our 1-1000 scale highlights the vulnerabilities most likely to be used in an attack, helping you prioritize truly critical issues. When used with our robust tagging system, you can even prioritize the systems most critical to your business, automatically.
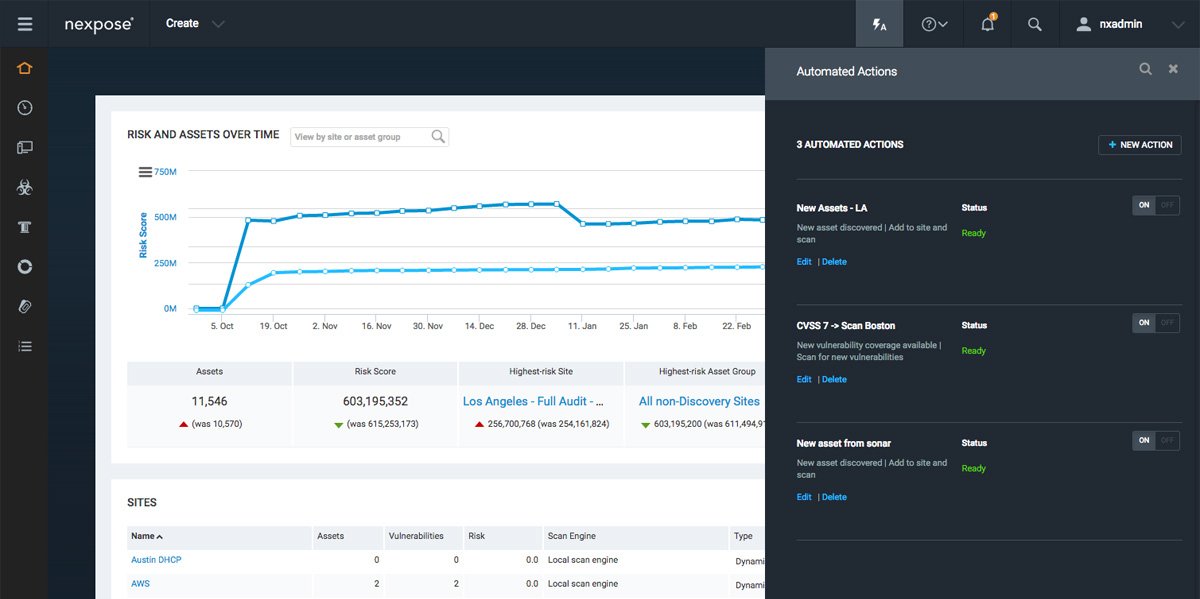
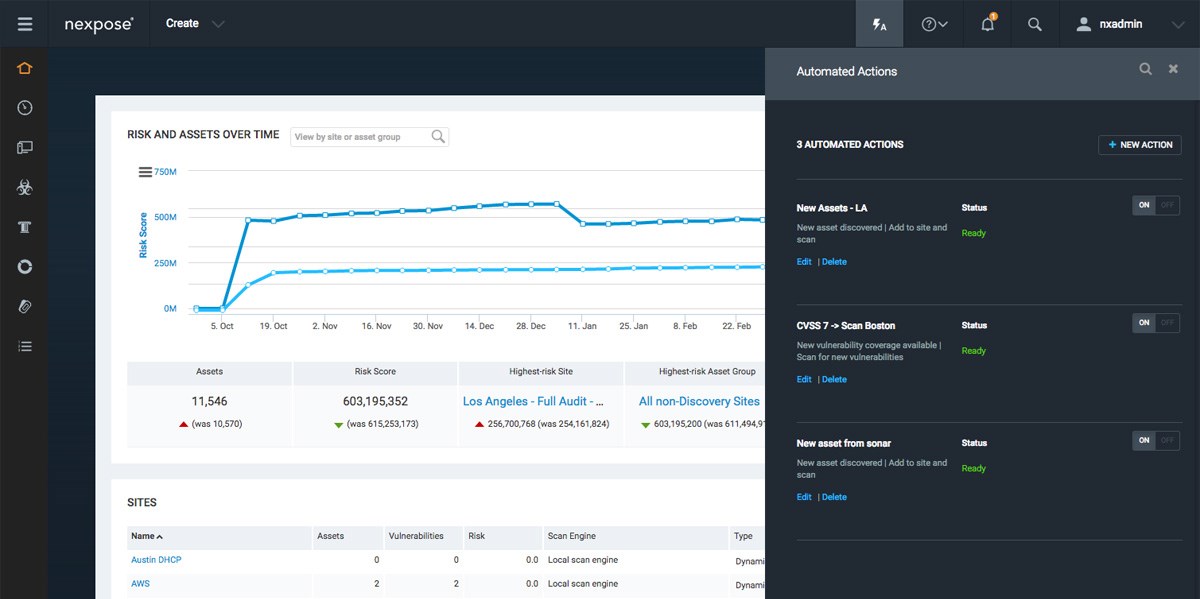
Adaptive Security
“Passive scanning” is loaded with false positives and stale data from infrequent data dumps. With Nexpose Adaptive Security, you can automatically detect and assess new devices and new vulnerabilities the moment they access your network. Combined with dynamic connections to VMware and AWS, and integration with the Sonar research project, Nexpose provides true live monitoring for your changing environment.
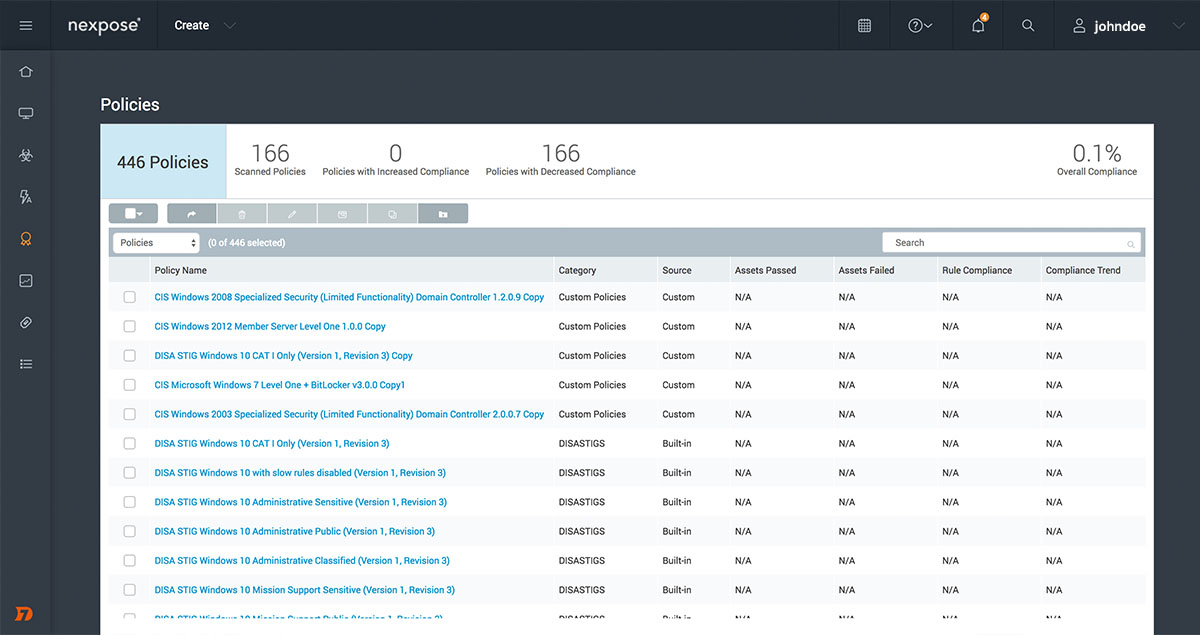
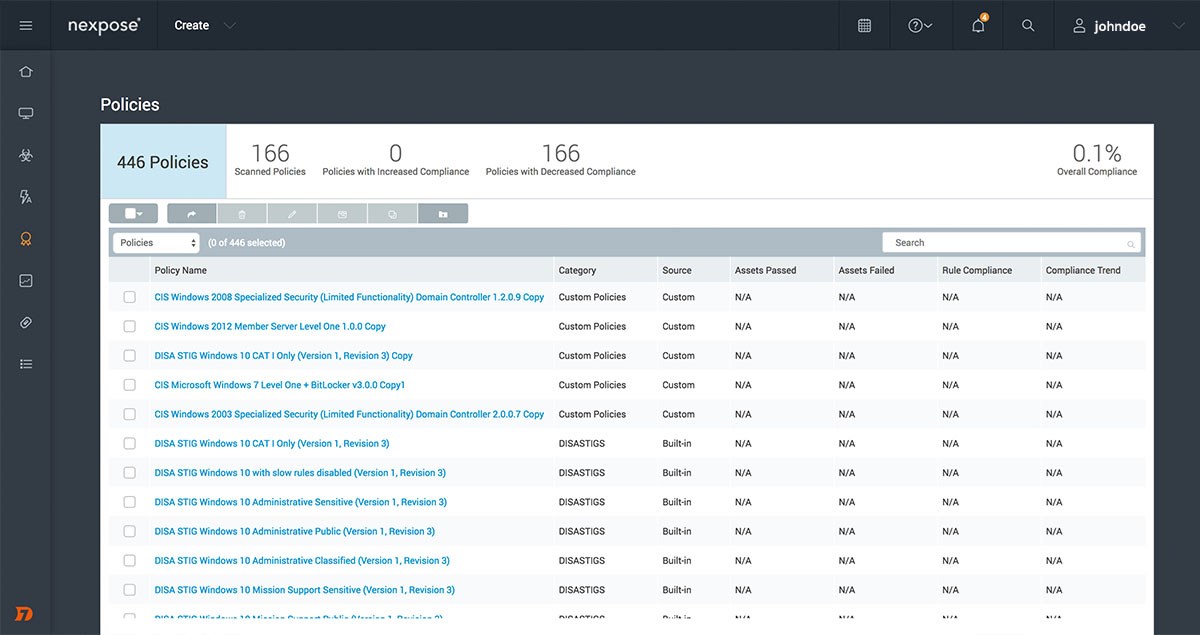
Policy Assessment
Hardening your systems is just as important as finding and fixing vulnerabilities. Nexpose provides integrated policy scanning to help you benchmark your systems against popular standards like CIS and NIST. Intuitive remediation reports give you step-by-step instructions on which actions you should take to make the biggest impact on improving compliance.
Remediation Reporting
Help IT help you. With Nexpose remediation reports, show IT the 25 actions they can take right now to reduce the most risk. Your data can be easily sliced and diced to give the right people the exact information they need to get their jobs done, without wading through 10,000 page reports or manual spreadsheets.
Integration with Metasploit
The goal of any security product is to shore up your defenses in the event of an actual attack—what better way to test them than by simulating one? With Metasploit Pro, you can validate your vulnerability scanner results using an automated, closed loop process, ensuring you automatically prioritize the most important assets first: the ones that are easiest to breach.