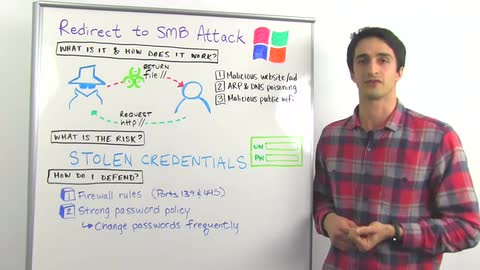
Cylance's SPEAR research team found some new attack methods that are based on what's actually quite an old weakness in Windows within SMB and the way SMB handles file URLs which are similarly formatted to HTTP URLs. That means way back in 1997. This vulnerability's been around for thousands of days. Basically, the attack flow here is the same for a variety of attacks that Cylance discussed. An attacker has a system that they control, and they trick a user into accessing it maybe over HTTP. When the user's system goes to connect to it over HTTP, the attacker's system redirects it with a file URL. When that happens, the victim system will automatically try to authenticate to the attacker system and pass along their hash credentials.
These different attacks arise in a few different ways. It can happen with malicious websites or ads. There are some chat clients that try to preview images, and if that image uses a file URL that sort of attack will happen. Also, with malicious public WiFi access points that an attacker controls.
What's the risk here? As I alluded to before, we're really worried about stolen credentials. While Windows, the latest versions of Windows especially, use hash credentials to perform that automatic authentication via SMB, those default settings that people overlook on their networks for that hash security often don't get changed. Those hash credentials, the hashing itself might not be secure, but also that hashing is only as good as more or less the strength of your passwords. If you have a six character long password and it's using common words, it's a lot easier for an attacker to crack that using dictionary attacks, for example. Even if you do have a complex password, though, it's not too costly these days for an attacker to rent out GPU farms in the Cloud for a few days and perform billions of guesses against your password per second.
Microsoft and some of the third party software that's affected by these attacks, they haven't released patches yet. But, there are some ways you can defend against it. One of those ways is by adding firewall rules to your perimeter firewalls and your endpoints to block SMB traffic on port 139 and 445 outbound to public IP addresses. Also, you want to make sure you have a strong password policy in place, so at least 10 or 12 characters, lower case and upper case letters, numbers, and symbols. Also, make sure that those passwords are being rotated somewhat frequently every 60 or 90 days. That way, if an attacker does manage to get ahold of some of your passwords, it may have already been changed by your users and they won't be able to do anything with it.
That's the gist of it for this attack. Thanks for joining us, and we'll see you next week.