Attacks—and attackers—are constantly evolving. To outpace them, you need a plan and you need to review it regularly. Our experts at Rapid7 will evaluate your environment—from technology to assets to people, process, and policy—to rate your capabilities and preparedness while offering relevant, business-based recommendations to help you meet your IR program goals. Need to build your program from the ground up? We can help with that too. Our IR Program Development offering can be customized to help build or improve your capability in any area of the Security Program Lifecycle.
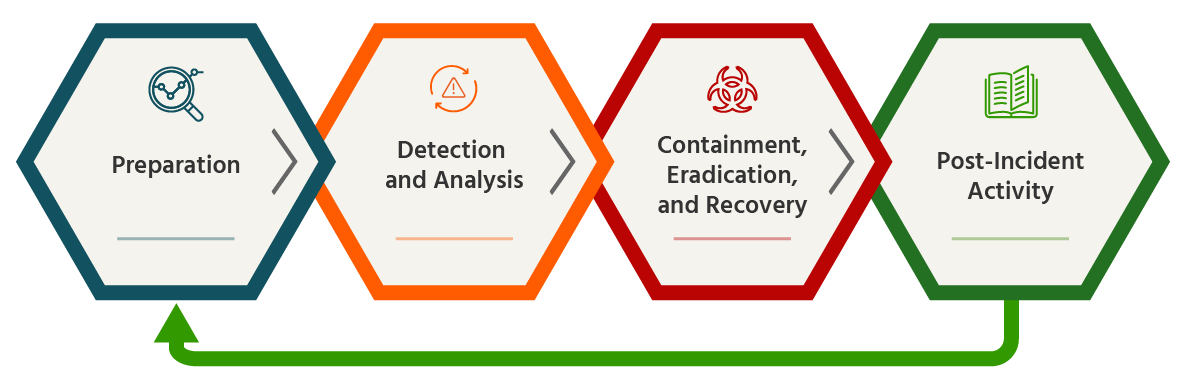
The Security Program Lifecycle
How Can We Help?
Our experts are ready to help you transform your incident response plan.
Contact UsIR Plan Development
Do you have an existing incident response plan, or need your plan reviewed or updated? Let the experts at Rapid7 help develop an IR plan that works for your security program. Some items we cover when building a new plan include:
- Security team interviews: These allow our experts to better understand your existing team dynamics, tools, and processes to ensure we build a relevant documentation plan for your environment.
- RASCI charts: Understanding who is responsible for a given set of actions in the event of an incident is critical. The RASCI charts will document both the tasks to be completed and their owners during the IR lifecycle.
- IR phases: The IR plan will outline the key phases in any investigation, and which steps must be taken during each phase.
- Criticality matrix: Understanding the scope and severity of an incident will ensure that proper escalation points and processes are followed.
- Incident and event response workflows: Based on the given criticality levels (low, medium, or high), we will help draft a plan that visualizes the various steps to be taken for each criticality level.
- Third parties: Identifying and documenting the third parties you work with is necessary with any MSP or cloud services. Key areas such as points of contact, service types, data retention strategy, and investigation engagement are within scope.
- Technology analysis: Defining what tools can be used during an engagement and how they are currently being used now helps to develop the IR plan.
- Industry standards and best practices
SOC Optimization
Let Rapid7’s incident response team take your SOC to the next level. Our team of experts sits with your SOC operators and analyzes how they currently react to incidents, the tools they use, how they use these tools, and how incident tracking and communication is currently executed. Additionally, we review your current tool deployment, configuration, and capabilities, such as EDR visibility, SOC capabilities around tools, and intel management.
The goal? To ensure your SOC is investigating the alerts that matter, documenting its findings, and communicating these findings in an organized, repeatable fashion.
Team Training
Rapid7’s incident response team has developed a variety of content tailored to educating security staff and IR personnel:
- Incident response: Experience on-site, hands-on lab time with real world incidents. Teams that complete this training will better understand how modern day incident response is performed, the most pervasive tools of the trade, and best practices for communication and reporting.
- Malware analysis: During an incident, knowing how to perform basic sample triage is foundational knowledge. As part of the malware training, we cover samples from a variety of formats, give a deep dive into the standard malware toolkit, and review how report/IOC development is performed.
- Threat intelligence: Being on the front lines, our team handles new intelligence daily. As part of the intel training class, we’ll show you the ropes; this includes how intel is tracked from case to case, and how intel is applied and collected based on an organization’s needs.
- Threat hunting: Proactive analysis can be game-changing for any organization. While a reactive approach is effective at the time you’re alerted, these alerts are, in many cases, too old or non-actionable by the time they’re received. We’ll show your team how to quickly and effectively perform threat hunting for attackers on various operating systems to mature your hunting program.
Prevention and Detection
- Log source review: Our team will review your current logging strategy and make recommendations based on industry and incident response best practices. This can include the prioritization of alerts, tuning of queries, or log ingestion tips.
- Capability review: Additionally, our team will identify potential gaps in your team’s prevention, detection, and response functions, and provide recommendations for filling those gaps through best practices, process improvements, and/or technological investments.
Response
- Run books: The IR Plan tells you what to do at a high level; the run books tell you which steps you will need to take based on the type of incident you have and exactly how to perform the steps. Since all attacks are not created equal, you need to tailor your response: This is where detailed run books become invaluable.
Remediation
- Validation and verification: With your team, we will validate that the remediation activities were appropriate for the incident and that the scoping and investigation steps taken were the most effective approach given the scenario.
Post-IR Analysis
- Report and data review: Have an investigation that was previously performed by another firm (or record of a prior incident) and want a second opinion? Maybe you’ve completed an investigation internally, but want peace of mind that you and your team covered every base. We can help pinpoint areas for improvement or give second opinions post-IR. We’ll collect the data you’ve already gathered, review the reports, and provide input where needed.