- Home
- Products
- InsightIDR
- Use Cases
- Detect Compromised Users and Lateral Movement
insightIDR
Detect Compromised Users and Lateral Movement
Get a Free Trial
No credit card necessary
Watch Demo
See how it all works
Stop the top technique behind confirmed breaches
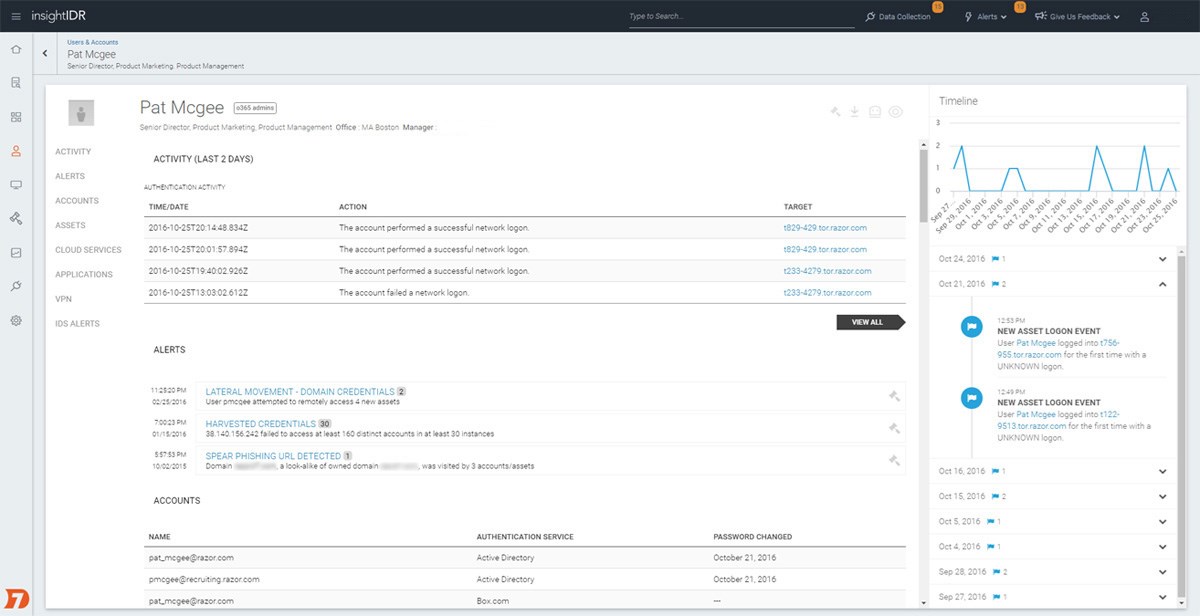
In 2017, 80% of hacking-related breaches used either stolen passwords and/or weak or guessable passwords. Users are both your greatest asset and your greatest risk. InsightIDR uses machine learning to baseline your users' behavior, automatically alerting you on the use of stolen credentials or anomalous lateral movement.

Get prioritized alerts
With InsightIDR, any notable behavior exhibited by your users is saved and powers a Risky User Ranking, helping you proactively prioritize areas to invest your time. Receive just 10-15 alerts per day, all highlighting the key things you need to know about your network.Detect the use of stolen credentials
InsightIDR automatically correlates activity on your network to the users and entities behind them, making it easy to spot risky behavior. By continuously baselining healthy user activity in your organization, InsightIDR extends beyond defined indicators of compromise to reliably detect attackers masking as company employees.Trick attackers with deception technology
Not all signs of the attacker are present in your log data. That's why InsightIDR comes with its own suite of intruder traps, which include Honeypots, Honey Users, Honey Credentials, and Honey Files. These surface earlier signs of compromise that other tools miss.