- Home
- Products
- InsightIDR
- Use Cases
- InsightIDR for Azure Cloud Environments
insightIDR
InsightIDR for Azure Cloud Environments
Detect suspicious behavior before the breach occurs
Better Decisions for Incident Detection and Response
Microsoft Azure is a powerful, flexible, scalable infrastructure platform for hosting applications in the cloud. But Azure security challenges don’t disappear; enterprises still need to protect themselves against phishing and social engineering attacks, misconfigurations in cloud assets, lateral movement by attackers, and other causes of data breaches and service interruptions.
InsightIDR–Rapid7’s cloud SIEM for modern detection and response–offers an ideal solution. It collects data from the major management and security tools native to Azure, combines that with information from across the organization’s IT footprint, and uses advanced analytics to detect malicious behaviors. It also provides context for rapid incident response and supports cloud reporting and compliance.
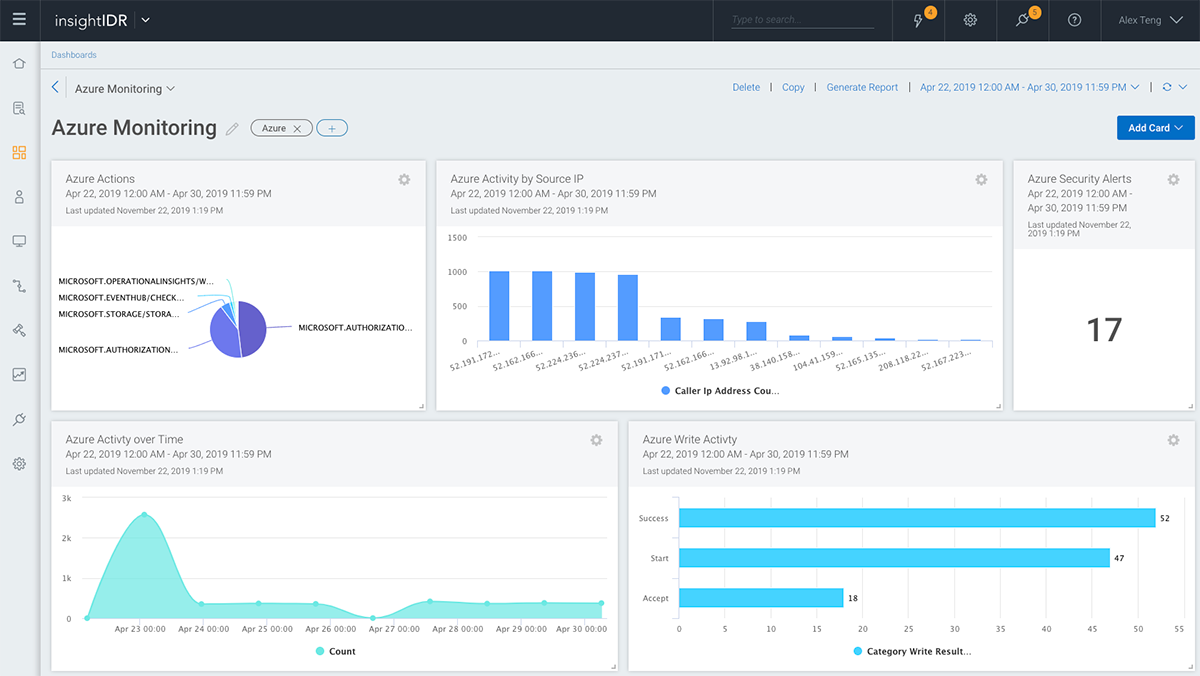

Aggregating Cloud Logs
Azure Event Hubs collect data and logs from Azure services. InsightIDR connects to Event Hubs to access and ingest data, including log data from:
- Azure Active Directory, which manages the identities and permissions of users in the enterprise’s Azure environment and tracks user sign-in activities
- Azure Monitor, which provides insight into Azure Resource Manager (ARM) activities, including administrative actions such as provisioning objects, standing up new virtual machines (VMs), and changing Azure permissions
- Azure Security Center, which monitors security events and creates alerts
- Office365, Exchange, and SQL databases, including administrator and user activity
- Microsoft DNS, which services domain name requests and logs connections to domains on the internet
InsightIDR combines log data acquired from Event Hubs and the Azure Activity Log API with information from endpoints, networks, on-premises data centers, and other cloud platforms such as Amazon AWS. Data from across the enterprise’s entire digital footprint is available for searching, reporting, and analysis.
Uncovering Anomalous Behaviors and Attacks
InsightIDR’s User Behavior Analytics (UBA) measure baseline activities by users identified in Azure Active Directory, then flag unusual behaviors. This would include behaviors that indicate compromised user credentials, such as atypical authentication requests and unusual single sign-on (SSO) activities.
Besides generating its own alerts, InsightIDR provides flexible dissemination of alerts generated by the Azure Security Center.
Reporting and Regulatory Compliance
InsightIDR supports cloud reporting and compliance requirements for monitoring, audit logging, and data retention. It offers a source of log data during compliance audits and provides proof of log retention. It can show auditors where logs are stored, confirm the appropriate log history, and demonstrate that the right log sources are represented.
InsightIDR’s intuitive dashboard can provide executives and board members with high-level information about the enterprise’s threat landscape, such as trending attacks, applications and areas of the network most subject to attack, and threats that have been remediated.
Keep Pace with Cloud Growth
Go ahead and ramp up your applications. As a native cloud-based tool, InsightIDR can scale up immediately to support increased activity and new applications while maintaining continuous security coverage.
InsightIDR is also designed to integrate quickly and seamlessly with new data sources, wherever they are. Through integrations with Azure, AWS and on-premises environments, InsightIDR is prepared to serve enterprises with hybrid environments as they move applications and services onto additional platforms.