A lot of people ask me "How do I take my first steps with Metasploit? And you know, what do I try to exploit? How do I go about it?" And I just want to talk about that a little bit today.
So, when you're a new driver, a student driver, you don't really want to go on the highway straight away. And in the same vein, you don't want to use Metasploit and test it out on your production network, because if you get something wrong, you know, it could have an impact on your production network. So, what we recommend is that you set up a little lab environment.
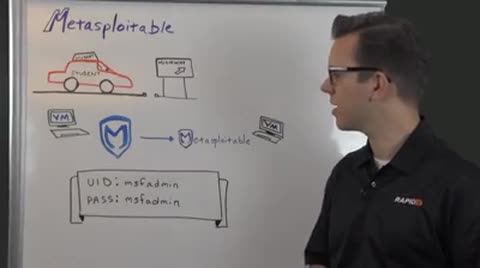
And it's really quite easy to do that. What I would recommend is that you set up a Metasploit in a virtual machine. Typically what I like to do is to take an Ubuntu operating system, install it on top of that because you don't have any licensing costs for that, get it up and running, and then create a second virtual machine that you can actually download from Rapid7 in the free tool section, called Metasploitable.
Metasploitable is essentially an intentionally vulnerable virtual machine that we created here to help you with your first steps with Metasploit.
So, there are a few different vulnerabilities on it that are easy to exploit. There are weak passwords on the platform, so you can try out the boot forcing feature. And even if you've tried those out and if you're familiar with those, maybe you want to take some more advanced steps and work with post-modules, which help you, you know, grab passwords from a system and do anything post the exploitation.
When you have downloaded Metasploitable and have it up and running, you can exploit from Metasploitable, sorry from Metasploit to Metasploitable over here. You'll need to know the IP address of this machine here. And to do that, you type in M-S-F admin for the user ID and M-S-F admin also for the password. As you see, it's intentionally vulnerable, and when you log on, just type I if, sorry, I-F config, and it will give you the IP address that it's currently running on. Plug that into Metasploit, start exploiting and you're good to go.
So if you're interested in this, please download Metasploitable from the free tools section at Rapid7.com, and have fun. So, see you at the next Whiteboard Wednesday.