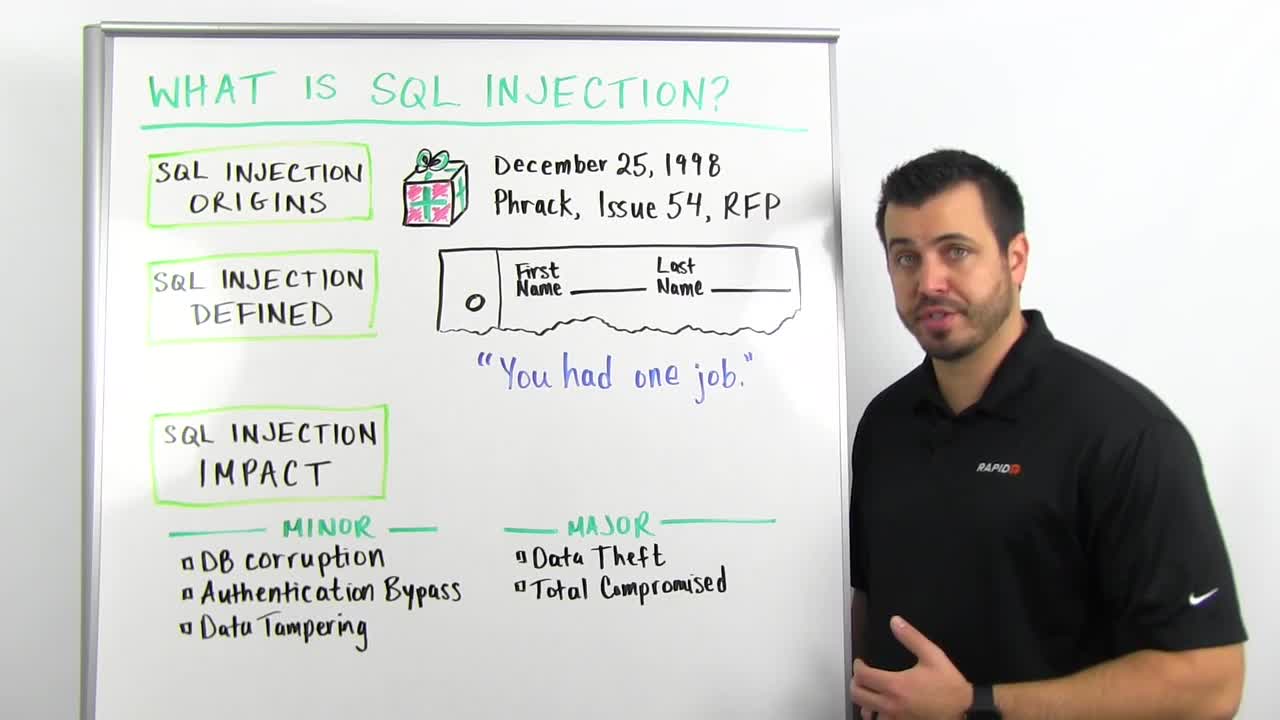
So, SQL injection, we're going to break this down into very non-technical terms. Where it came from? This was a Christmas present from Rain Forest Puppy, Jeff Forristal, back on December 25, 1998. Old, too old, still happening, no excuse. So Phrack is basically a hacker magazine, old school, this was how they distributed findings. What Jeff had found was a list of vulnerabilities in NT Web technology. He documented what was later known as SQL injection. So what is SQL injection? Let's define this.
SQL injection is when you interact with a website or a Web service of some type. You're passing information, like when you type in a search field, or you type into a username field, or something to this effect, user-provided input. You're typing in, you press Enter, you send it to the Web server. The Web server's interacting on the back end, most of the time, with a database. This is the same as walking into the lobby of a building. There's going to be a sign-in sheet, first name, last name, time and date. You let anyone from the general public, anyone from the Internet, interact and provide this information. What happens is, computers do what they're told to do. Computers have to be told what instructions are and what data is. This is the simplest example of computers taking what's given to them as instructions.
So let's say I've walked into the county courthouse. I'm there because, for whatever reason, I get to talk to the judge today, and so on the sign-in form, I write "Trey", my last name, "is free to go". The county clerk walks this up, hands it to the judge, "First up, Trey is free to go." "Thanks, see you later. I'm out." Is that okay? Does that really work? It turns out, that's exactly what SQL injection does. You've given instructions to the website or the Web service, it's sent it back to the database, and the database has performed my instructions because that's what computers do, they do what they're told to do. We need to handle this information in a very clear way. Tell the computer, tell the database server, "This is information, this is not instructions, you do not execute this. You perform a function and then you respond, very, very simple. This is so embarrassing. This is the ultimate. You had one job to do."
So SQL injection impact. We know where it came from, we have an idea of what this means. The impact: It could be as minor as bypassing the login field. The login exercise is basically checking the database, saying, "Hey, Trey said his password is this. Is that true?" There's a bypass function, really simple. Fun play with numbers and special characters, you can bypass login fields. Database corruption will have a link to Little Bobby Tables, the XKCD comic, pretty funny. Bottom line is, people are passing commands. So you can corrupt the database, you can bypass an authentication step, or you can tamper with data in the database.
On the worse end of the spectrum, this is where you're hearing about SQL injection in the news still, people are stealing data. You're giving a command saying, "Hey, give me all of your usernames, give me all of your passwords, give me all the mailing addresses, give me all the credit card information in your database." Database says, "You got it, here you go," and starts downloading it to the attacker. So data theft is one of the scarier ones. The other is total compromise. So you can configure a database to allow you to pass commands to the database, like operating system commands. This is basically giving an attacker or a malicious party full command and control of your server, so it isn't just data theft, they're now inside your environment. They've got a foothold. They're going to move around and do other things.
So this is SQL injection. How to fix it? Not going to get into that here. We've got a list of links on the page you're looking at that's going to take you to some of the best resources on the Internet. My name's Trey Ford, Global Security Strategist at Rapid7. Thanks for tuning in.