What are you but the sum of your critical data and personal information? Okay, we’re exaggerating a bit here, but the point is that protecting yourself from phishing attacks ensures the well-being of your business operations and of your people. Unfortunately, you’re up against some persistent attackers; the Anti-Phishing Working Group found that over 87,000 unique phishing campaigns are launched every month. What’s the damage? The FBI estimates that business email compromise (BEC) scams alone have caused $5.3 billion in losses to businesses worldwide over three years. That’s a lot of zeroes.
That doesn't mean anti-phishing programs are futile: Susceptibility to phishing is a solvable problem, and it starts with your employees. By building a phishing awareness training program and equipping your users to detect Indicators of Phishing (more on those later) from the start, you reduce their likeliness to divulge critical information.
Detect Unwanted Behavior on Your Network
Phishing is the most prevalent cybersecurity attack. Detect suspicious behavior before things escalate.
Try InsightIDRDetecting phishing attacks against your users
Phishing attacks can take many forms, but they tend to employ similar tactics to capture your critical data. Think of the presence of these tactics as clues that there may be malicious intent behind an email.
Common Indicators of Phishing (IOPs):
- Too many phish in the sea? Different Reply To and From addresses
- Who wants to know? A contact name or email address you don’t recognize, or a company you don’t do business with
- Is it urgent? Deadlines, exclamation marks, and text in all caps
- Do they type good? Awkward wording and spelling errors
- Download for the down low? Suspicious or unexpected attachments
- What’s your sign? Requests for personal or confidential information (e.g. passwords)
- Is it a trap? A disguised link, or a link that does not match the URL displayed when you hover your mouse over it
Ready to proactively spot these IOPs? Detect suspicious activity with a 30-day free trial of InsightIDR. New dog (or rather, phish), old tricks.
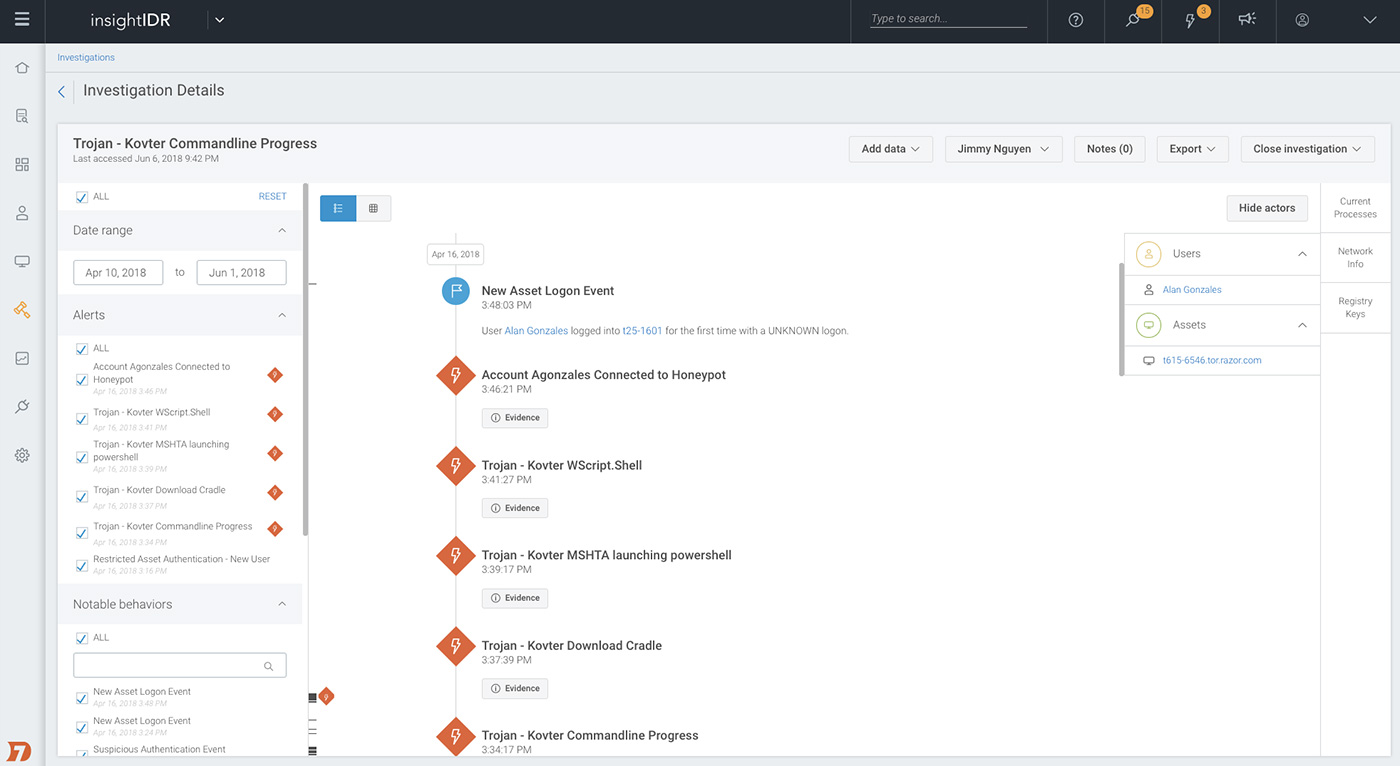
Formulating a phishing incident response plan
So you’ve been phished. (You’re far from alone.) Part of a comprehensive security plan (that includes anti-phishing) is your strategy for response—an incident response plan.
When dealing with a phishing incident, there are five major items to check off your list:
- Identification: How will you determine the scope of the incident and understand its context? What processes and technology do you have in place to identify that a user in your organization has been phished? Do you have visibility into risky or privileged users where you should prioritize follow-up?
- Containment: How will you contain the infection or compromised credentials that are being leveraged against your environment?
- Remediation: How will you repair any damage caused by infection or compromised credentials?
- Root cause analysis: How will you determine what broke down in your people, processes, or technology that allowed this phishing incident to occur?
- Compensating controls/awareness training: What steps will you take to update the configuration or implement new compensating controls to ensure this does not happen again? For the compensating control of user awareness training, which users will you target, and what content will you deliver?
Want to go from compromise to containment faster? InsightIDR arms you to also adapt and investigate before things get out of control.