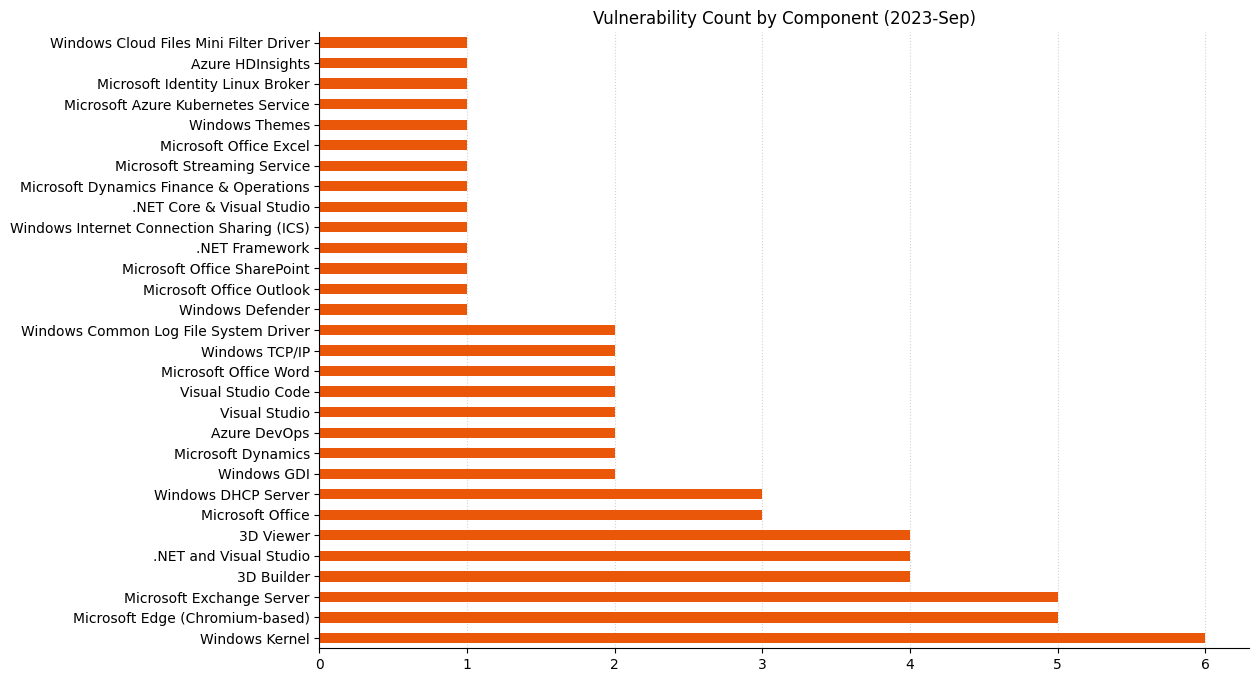
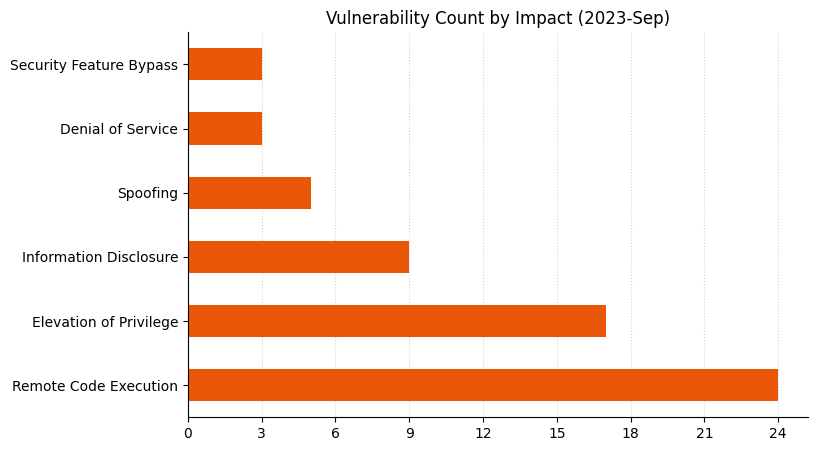
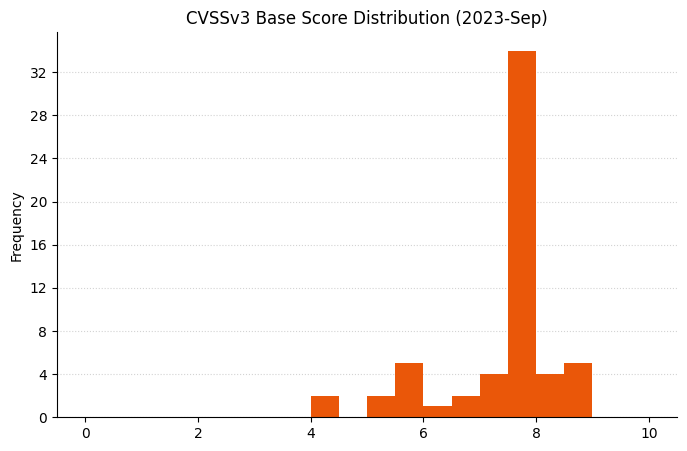
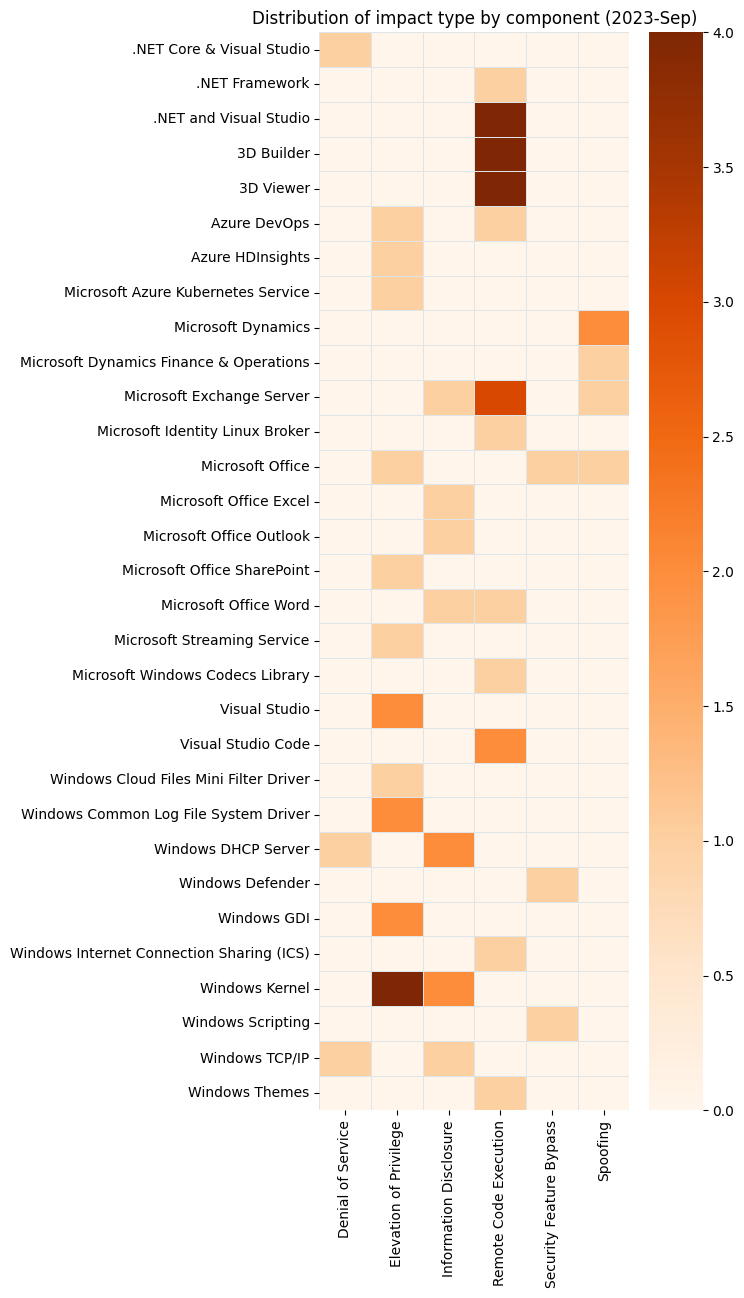
Microsoft is addressing 65 vulnerabilities this September Patch Tuesday, including two zero-day vulnerabilities, as well as four critical remote code execution (RCE) vulnerabilities, and six republished third-party vulnerabilities.
Word: zero-day NTLM hash disclosure
Microsoft Word receives a patch for CVE-2023-36761, which is marked as exploited in the wild as well as publicly disclosed; successful exploitation results in disclosure of NTLM hashes from a malicious opened document via the Preview Pane. This could provide an attacker with the means to “Pass the Hash” and authenticate remotely without resorting to brute force.
Microsoft is clearly concerned about the potential impact of CVE-2023-36761, since they are providing patches not only for current versions of Word, but also for Word 2013, which reached its Extended End Date back in April 2023. In March, Microsoft patched CVE-2023-23397, a vulnerability in Outlook which also led to NTLM hash leaks, and which received significant attention at the time.
Streaming Service Proxy: zero-day elevation to SYSTEM
The second zero-day vulnerability patched this month is CVE-2023-36802, an elevation of privilege vulnerability in Microsoft Streaming Service Proxy, which could grant SYSTEM privileges via exploitation of a kernel driver. Microsoft has detected in-the-wild exploitation, but is not aware of publicly available exploit code. This is a debut Patch Tuesday appearance for Microsoft Streaming Service, but with several researchers from across the globe acknowledged on the advisory, it’s unlikely to be the last. Today’s confirmation of in-the-wild exploitation prior to publication all but guarantees that this will remain an area of interest.
Internet Connection Sharing: same-network critical RCE
CVE-2023-38148 describes a critical remote code execution (RCE) in the Windows Internet Connection Sharing (ICS) functionality. Although the advisory is light on detail, it’s likely that successful exploitation would lead to arbitrary code execution on the ICS host at SYSTEM level. The silver lining is that the attack cannot be carried out from another network, so attackers must first establish an adjacent foothold.
Visual Studio & .NET: critical RCE via malicious package file
This month’s three other critical RCE vulnerabilities have quite a lot in common: CVE-2023-36792, CVE-2023-36793, and CVE-2023-36796 all rely on the user opening a malicious package file, and are thus classed as arbitrary code execution rather than no-interaction RCE. In each case, patches are available for a long list of Visual Studio and .NET installations. Organizations with large developer headcount are likely to be disproportionately at risk.
Exchange (as usual): RCE
Microsoft is patching five vulnerabilities in Exchange this month. Although Microsoft doesn’t rate any of these higher than “Important” under their proprietary severity rating system, three of the five are RCE vulnerabilities with CVSSv3 base score of 8.0. CVE-2023-36744 CVE-2023-36745, and CVE-2023-36756 would surely receive higher severity if not for several mitigating factors. Successful exploitation requires that the attacker must be present on the same LAN as the Exchange server, and must already possess valid credentials for an Exchange user. Additionally, Microsoft notes that the August 2023 patches already protect against these newly published vulnerabilities, further underscoring the value of timely patching.
SharePoint: elevation to admin
SharePoint receives a patch for CVE-2023-36764, which allows an attacker to achieve administrator privileges via a specially-crafted ASP.NET page. As is often the case with SharePoint vulnerabilities, a level of access is already required, but Site Member privileges are typically widely granted.
Azure DevOps Server: elevation of privilege & RCE
Azure DevOps Server receives two fixes this month. While CVE-2023-38155 requires that an attacker carry out significant recon and preparation of the environment, successful exploitation would lead to administrator privileges. Potentially of greater concern is CVE-2023-33136, which allows an attacker with Queue Build permissions to abuse an overridable input variable to achieve RCE. While most DevOps Server installations are hopefully managed by people both willing and able to apply prompt upgrades, CI/CD environments are prime targets for supply chain attacks.
They do it with Mira
A vulnerability in the Windows implementation of wireless display standard Miracast allows for an unauthenticated user to project to a vulnerable system. Although CVE-2023-38147 requires that an attacker be in close physical proximity to the target, consider that wireless display technology is often used in high-traffic environments such as conventions, which could allow an opportunistic attacker to inflict reputational damage. While exploitation requires that the target asset is configured to allow "Projecting to this PC" and marked as "Available Everywhere" – and Microsoft points out that this is not the default configuration – most administrators will know from long experience that many users will simply select whichever options cause them the least friction.
Summary Charts
Summary Table
Apps vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-36760 | 3D Viewer Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36740 | 3D Viewer Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36739 | 3D Viewer Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36773 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36772 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36771 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36770 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41303 | AutoDesk: CVE-2022-41303 use-after-free vulnerability in Autodesk® FBX® SDK 2020 or prior | No | No | N/A |
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-29332 | Microsoft Azure Kubernetes Service Elevation of Privilege Vulnerability | No | No | 7.5 |
| CVE-2023-38156 | Azure HDInsight Apache Ambari Elevation of Privilege Vulnerability | No | No | 7.2 |
| CVE-2023-36736 | Microsoft Identity Linux Broker Remote Code Execution Vulnerability | No | No | 4.4 |
Azure Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-33136 | Azure DevOps Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-38155 | Azure DevOps Server Remote Code Execution Vulnerability | No | No | 7 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-4863 | Chromium: CVE-2023-4863 Heap buffer overflow in WebP | No | No | N/A |
| CVE-2023-4764 | Chromium: CVE-2023-4764 Incorrect security UI in BFCache | No | No | N/A |
| CVE-2023-4763 | Chromium: CVE-2023-4763 Use after free in Networks | No | No | N/A |
| CVE-2023-4762 | Chromium: CVE-2023-4762 Type Confusion in V8 | No | No | N/A |
| CVE-2023-4761 | Chromium: CVE-2023-4761 Out of bounds memory access in FedCM | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-36796 | Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36793 | Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36792 | Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36794 | Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36758 | Visual Studio Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36742 | Visual Studio Code Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36788 | .NET Framework Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36759 | Visual Studio Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2023-36799 | .NET Core and Visual Studio Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-39956 | Electron: CVE-2023-39956 -Visual Studio Code Remote Code Execution Vulnerability | No | No | N/A |
Exchange Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-36757 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2023-36756 | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2023-36745 | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2023-36744 | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2023-36777 | Microsoft Exchange Server Information Disclosure Vulnerability | No | No | 5.7 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-36886 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 7.6 |
| CVE-2023-38164 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 7.6 |
| CVE-2023-36800 | Dynamics Finance and Operations Cross-site Scripting Vulnerability | No | No | 7.6 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-36764 | Microsoft SharePoint Server Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-36765 | Microsoft Office Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36766 | Microsoft Excel Information Disclosure Vulnerability | No | No | 7.8 |
| CVE-2023-36763 | Microsoft Outlook Information Disclosure Vulnerability | No | No | 7.5 |
| CVE-2023-36762 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36761 | Microsoft Word Information Disclosure Vulnerability | Yes | Yes | 6.2 |
| CVE-2023-41764 | Microsoft Office Spoofing Vulnerability | No | No | 5.5 |
| CVE-2023-36767 | Microsoft Office Security Feature Bypass Vulnerability | No | No | 4.3 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-38163 | Windows Defender Attack Surface Reduction Security Feature Bypass | No | No | 7.8 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-38146 | Windows Themes Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-38147 | Windows Miracast Wireless Display Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-38148 | Internet Connection Sharing (ICS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-38150 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35355 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36802 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability | Yes | No | 7.8 |
| CVE-2023-38162 | DHCP Server Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36805 | Windows MSHTML Platform Security Feature Bypass Vulnerability | No | No | 7 |
| CVE-2023-38140 | Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-36803 | Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 |
Windows ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2023-38142 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-38141 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-38139 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-38161 | Windows GDI Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36804 | Windows GDI Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-38144 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-38143 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-38149 | Windows TCP/IP Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-38160 | Windows TCP/IP Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-38152 | DHCP Server Service Information Disclosure Vulnerability | No | No | 5.3 |
| CVE-2023-36801 | DHCP Server Service Information Disclosure Vulnerability | No | No | 5.3 |
Download Rapid7's 2023 Mid-Year Threat Report ▶︎