While unpatched systems are often the first stepping stone of a breach, it's often weak or shared credentials that help attackers intrude deeper into the network and breach sensitive data. Common problems are:
- Weak passwords that lack length or complexity
- Passwords contained in dictionaries
- Passwords that are easily guessed based on information about the infrastructure
- Vendor default passwords
- Replaying cached credentials
- Re-use of passwords across trust zones
- Development test credentials in a production environment
- Active accounts of previous employees
Services You Can Audit With Metasploit
These are all issues you can scan for with Metasploit. Unlike other password auditors that only test Windows login credentials, Metasploit Pro can brute force passwords to audit passwords across a wide range of operating systems and services, including:
-
SMB/Windows/CIFS server
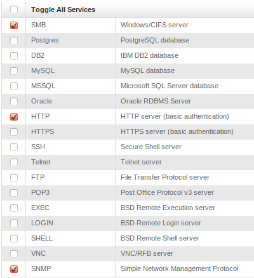
- PostgreSQL database
- IBM DB2 database
- MySQL database
- Microsoft SQL Server database Oracle
- Oracle RDBMS Server
- HTTP server (basic authentication)
- HTTPS server (basic authentication)
- Secure Shell server
- Telnet server
- File Transfer Protocol server
- Post Office Protocol v3 server
- BSD Remote Execution server
- BSD Remote Login server
- BSD Remote Shell server
- VNC/RFB server
- Simple Network Management Protocol
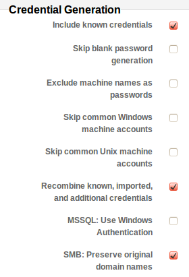
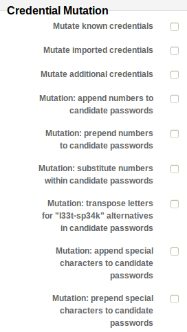
Metasploit Pro uses an advanced password cracking mechanism that takes into account wordlists (including built-in dictionaries and custom wordlists) as well as information gathered from the infrastructure, such as machine names. To brute force the passwords, Metasploit Pro creates numerous permutations of passwords, for example exchanging letters for numbers (password becomes “passw0rd”). Metasploit Pro also tries known vendor default passwords.
Recycle Collected Evidence And Keep Iterating
After gaining access to a system through brute forcing or exploitation, Metasploit collects passwords and password hashes from compromised systems. Using its integrated John the Ripper algorithms, Metasploit Pro automatically brute forces encrypted passwords for replay attacks. When you launch a second and third brute forcing pass on your network, Metasploit Pro will use collected passwords and replay password hashes (pass-the-hash attack) to get access to more systems. You can also specify known credentials, such as development accounts and accounts of employees or consultants that are no longer with the company, to verify that these cannot be used to gain access to any systems on the network.
Iterating the process gives you access to additional machines, harvesting more and more credentials and hashes. You should definitely try this process across trust zones, e.g. DMZ and internal network, to uncover credentials in an untrusted zone that also give you access to a trusted zone.
Report On Your Findings
Once you have completed your password audit, you can generate an Authentication Tokens Audit Report that includes passwords, SSH keys, and SMB hashes, summarizing:
- Guessed password frequency
- A list of all guessed passwords
- Authentication token frequencies
- A list of all authentication tokens
You can configure the reports to either show or mask found passwords, depending on the report's audience. Password audit results are also reflected in other reports, such as PCI and FISMA compliance reports.
Where You Can Learn More
HD Moore, the Metasploit Chief Architect, is showing some of the tips and tricks of how to audit passwords with Metasploit in next week's webinar. Register now and save the date on your calendar!