Building an Application Vulnerability Management Program, found in the SANS Institute Reading Room (https://www.sans.org/reading-room/whitepapers/application/building-application-v ulnerability-management-program-35297), identifies vulnerability program management as a cyclical process involving the following steps:
- Policy
- Discovery and Baseline
- Prioritization
- Shielding and Mitigation
- Eliminating the Root Cause
- Monitoring
While the use of Nexpose applies to several of these steps, the scope of this article is how Adaptive Security fits into your vulnerability management program. To that end we will cover monitoring.
Monitoring
Monitoring is the part of the vulnerability management cycle where changes and refinements are considered and adjustments are made before proceeding to the next iteration. Two critical areas of change to consider are as follows:
- Covering gaps in your vulnerability assessments
- Discovery of new vulnerabilities
Covering Your Blindspots
Your run regular scans to discover and assess the assets connected to your network. You carefully schedule the vulnerability scans on nights and weekends to reduce the impact on your network during business hours. How will you ensure that of those laptops that people take home and on the road are also scanned for vulnerabilities? Adaptive Security allows you to automatically detect and scan assets that were previously connected to your network and have missed recent vulnerability scans.
There is a prerequisite for an automated action to employ the discovery trigger:
-
A dynamic discovery connection to source the discovered assets.
- Dynamic discovery was covered in a recent blog (Use DHCP Discovery to Implement Critical Security Control #1 ).
To create or manage automated actions, click the automated actions icon on the top navigation bar.
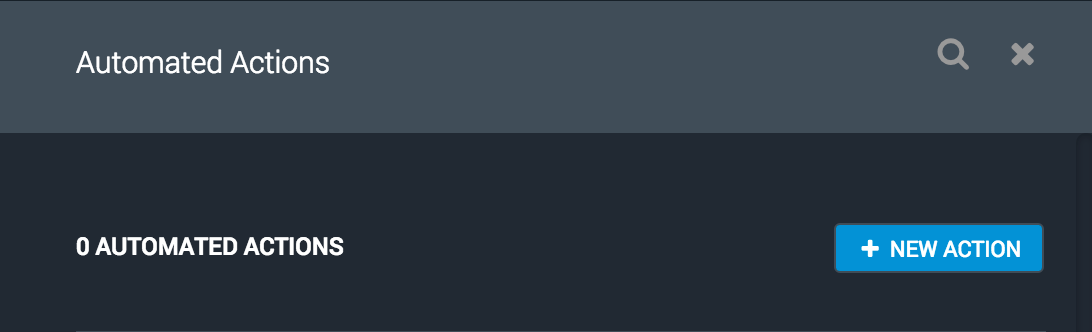
Click the NEW ACTION button to create a new action.
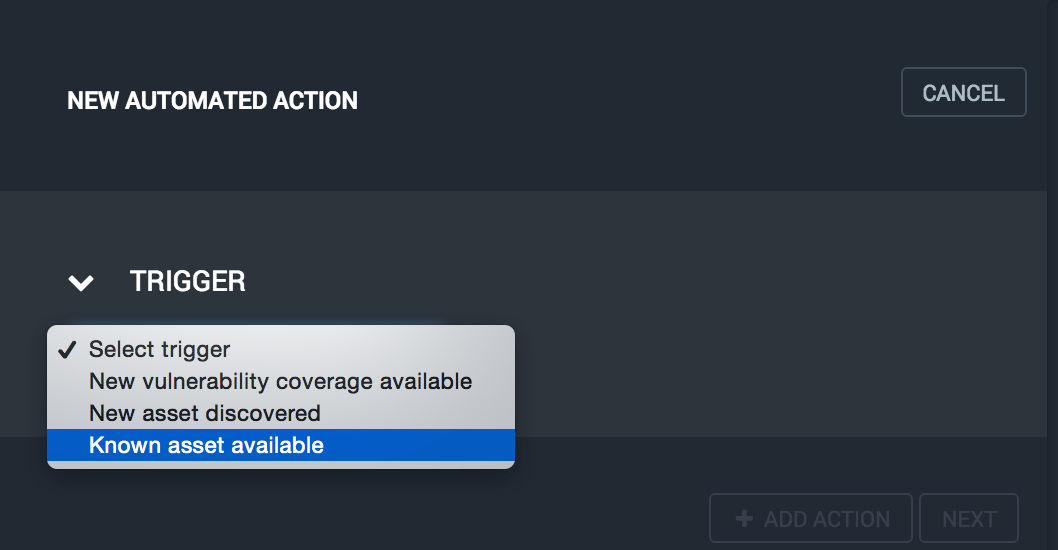
Select the type of trigger for your action. For this use case, we'll choose "Known asset available" to detect when assets are reconnected to the network.
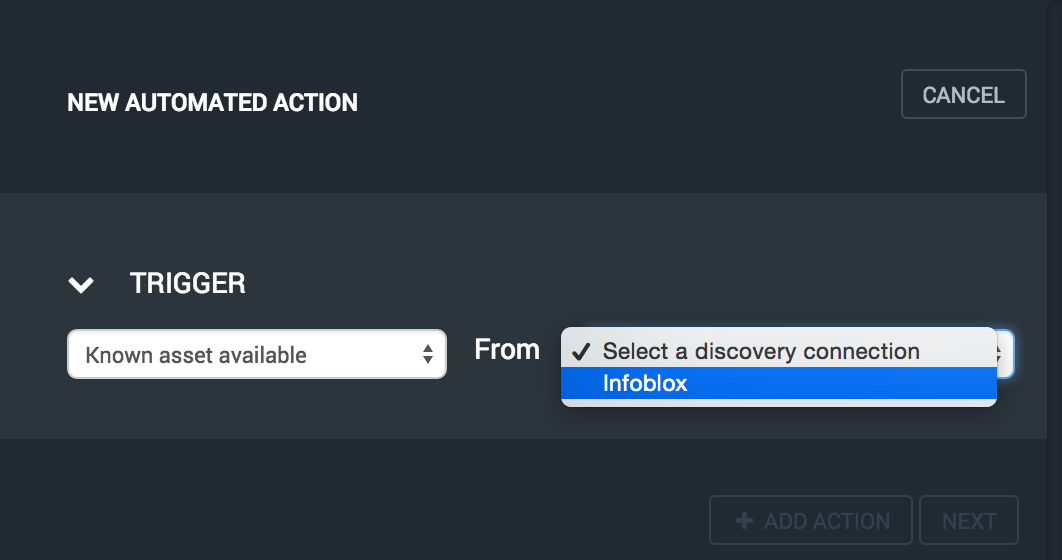
Next, select the discovery connection you wish to use as the source for this trigger. We're using a DHCP dynamic discovery connection that accepts Infoblox Triznic log entries via syslog.
Optionally specify one or more filter criteria to refine the assets to be processed. Since we want to scan returning assets that have missed recent scans, we'll select Hours Since Last Scan and enter 84 to include only assets that have not been scanned in a week. Click on the Next button to continue.
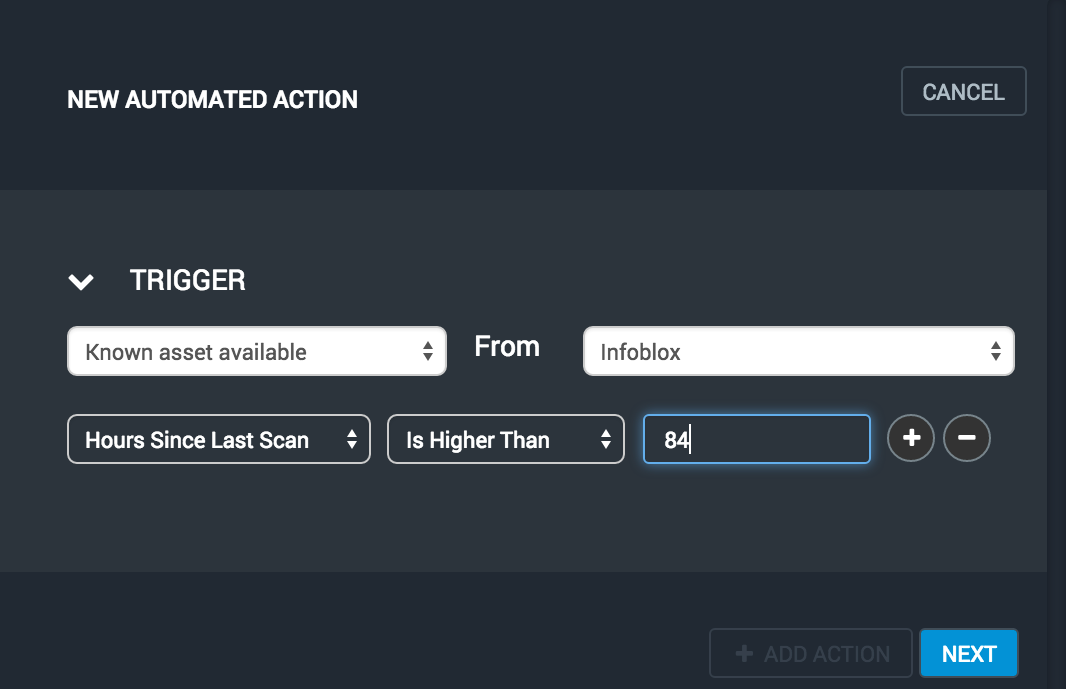
Select the action to take when the trigger is invoked. We'll use "Scan." Since this action uses the site from each asset's most recent scan, there is no need to provide any further information.
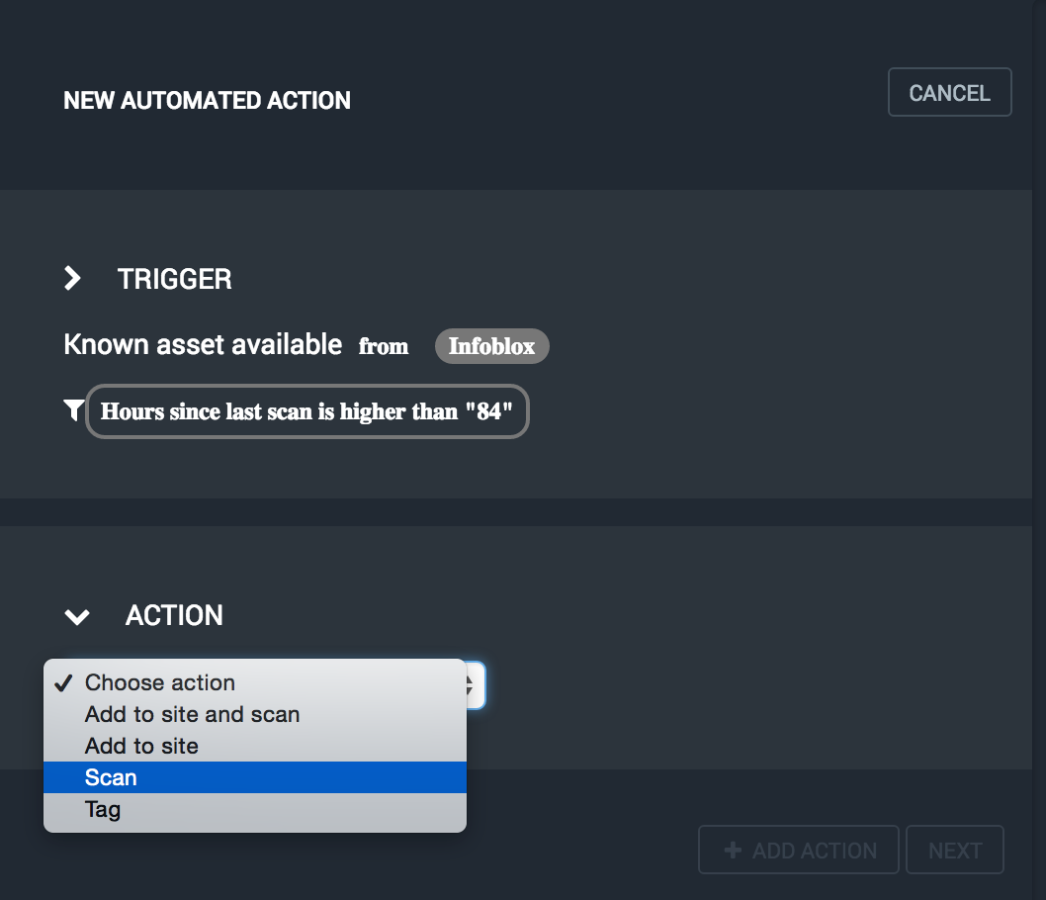
Enter a descriptive and unique name for this action and then click the Save button.
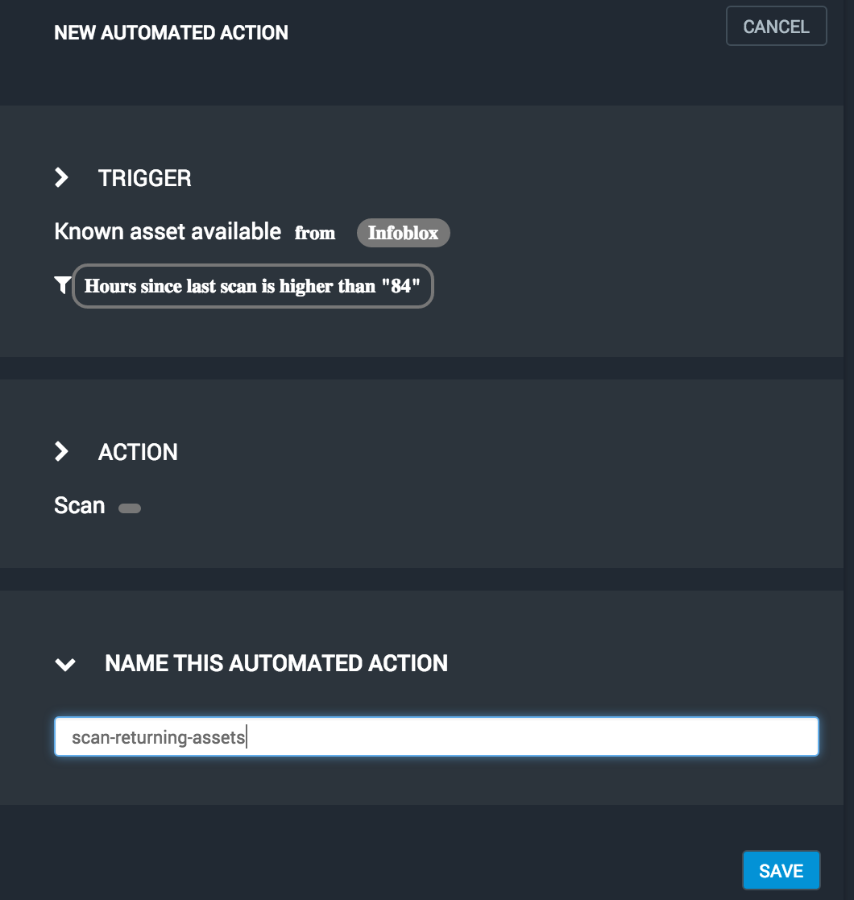
You should see you new automated action in the list. Here you may view the current state of the action and turn it on and off.
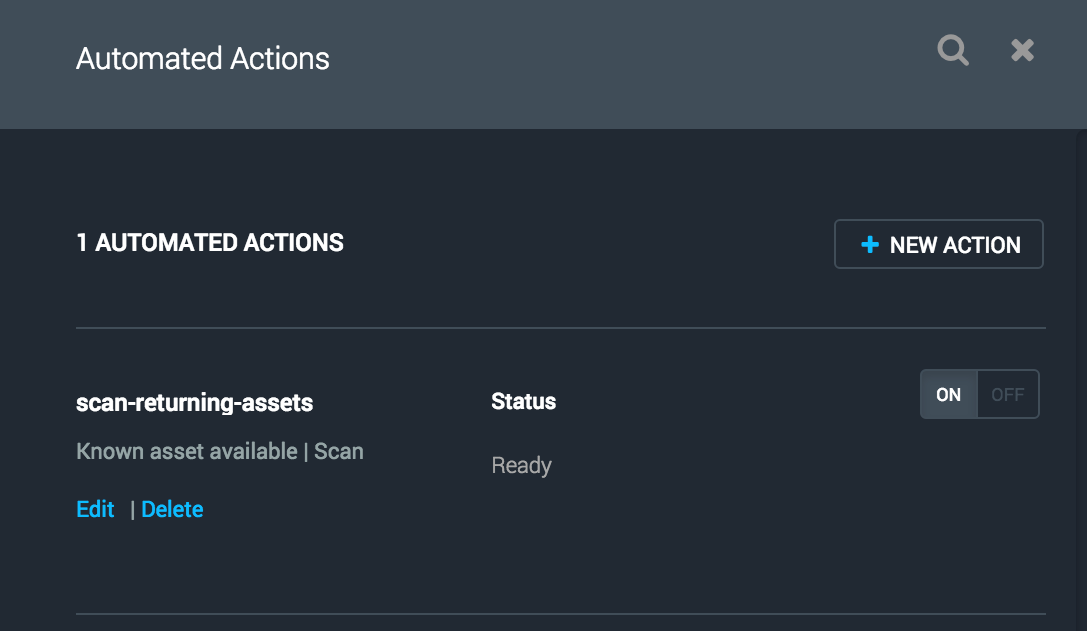
From this point forward, the automated action will scan all returning assets that have not been scanned in the last week.
Reacting to New Vulnerability Discoveries
Researchers continuously discover and publish new vulnerabilities. Quickly assessing your network's exposure to the more critical new vulnerabilities is essential. Also, with the seemingly increasing number of high-profile breaches in the media, you need to be able to report your assessed risk to executives as soon as possible. In any case, you can reduce your risk by scanning for new, critical vulnerabilities as soon as they're published rather than waiting for the next scan window. With Adaptive Security, you can create an automated action that triggers scans for only the new vulnerabilities that meet your criteria as they are published.
Click the automated actions icon from the top navigation bar and press the NEW ACTION button. Next, select the "New vulnerability coverage available" trigger. Finally, specify a filter for refining the vulnerabilities that will be automatically scanned.
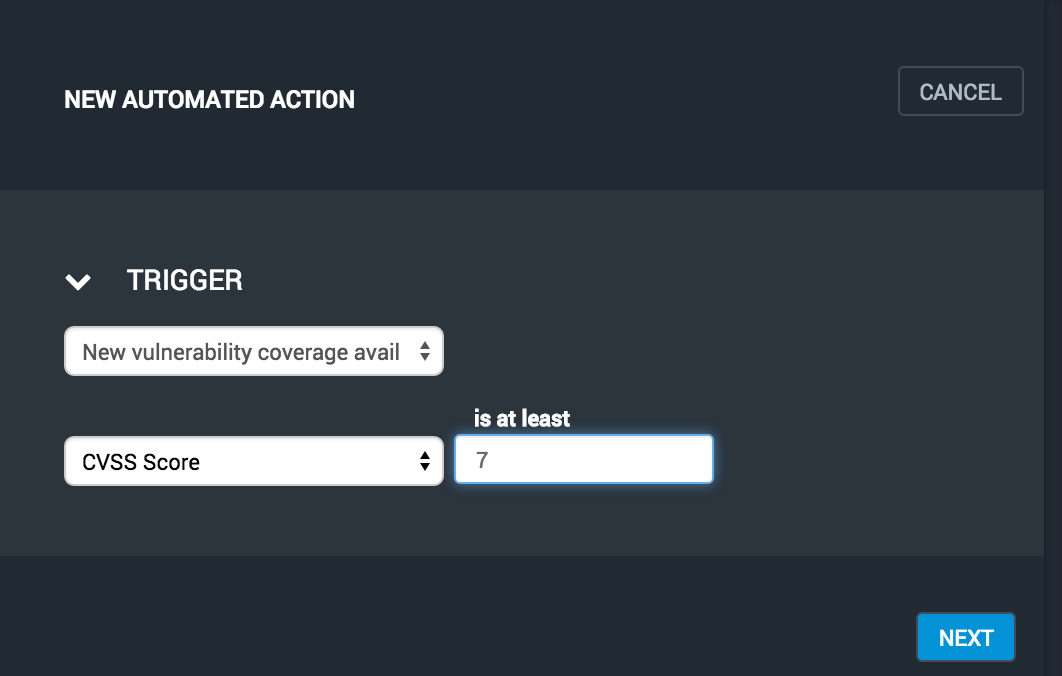
Select the "Scan for new vulnerabilities" action and then select the site to be scanned when new vulnerabilities are published.
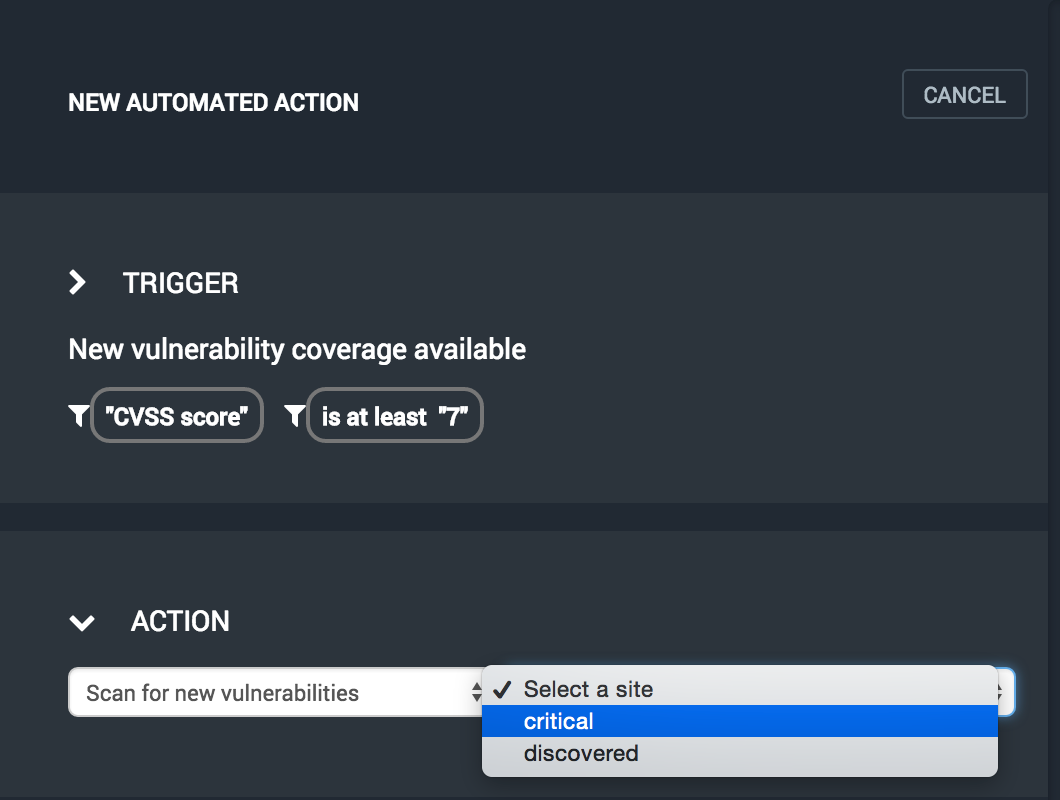
Enter a unique, descriptive name for the action and press the SAVE button.
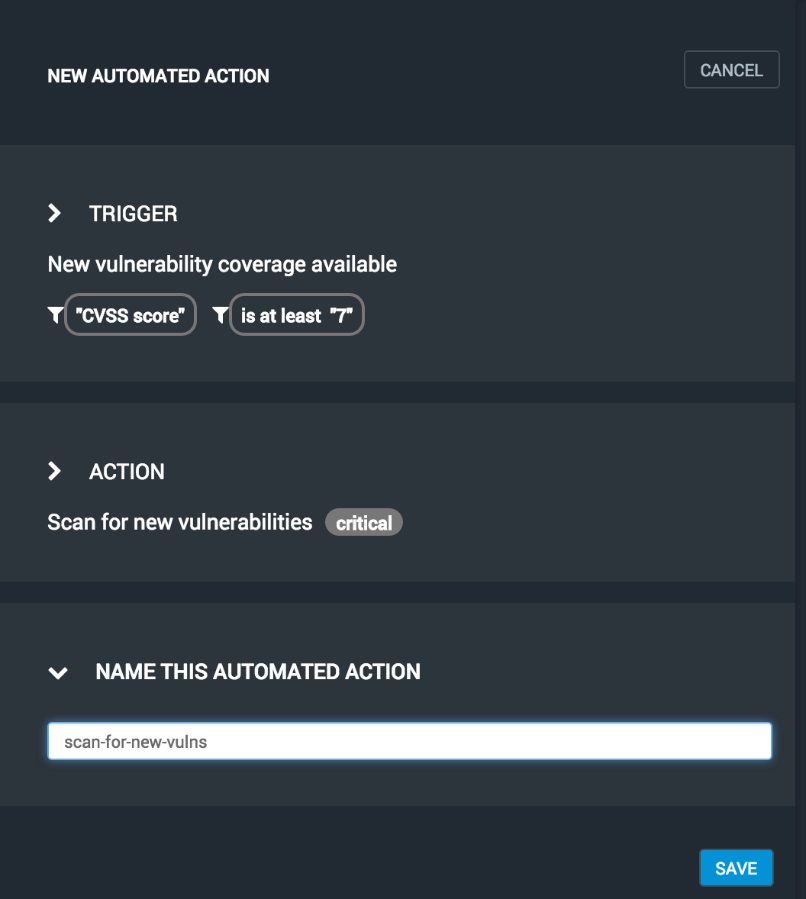
Your new action will be displayed in the list of automated actions. Again, you may view the action state or turn it on and off from here.
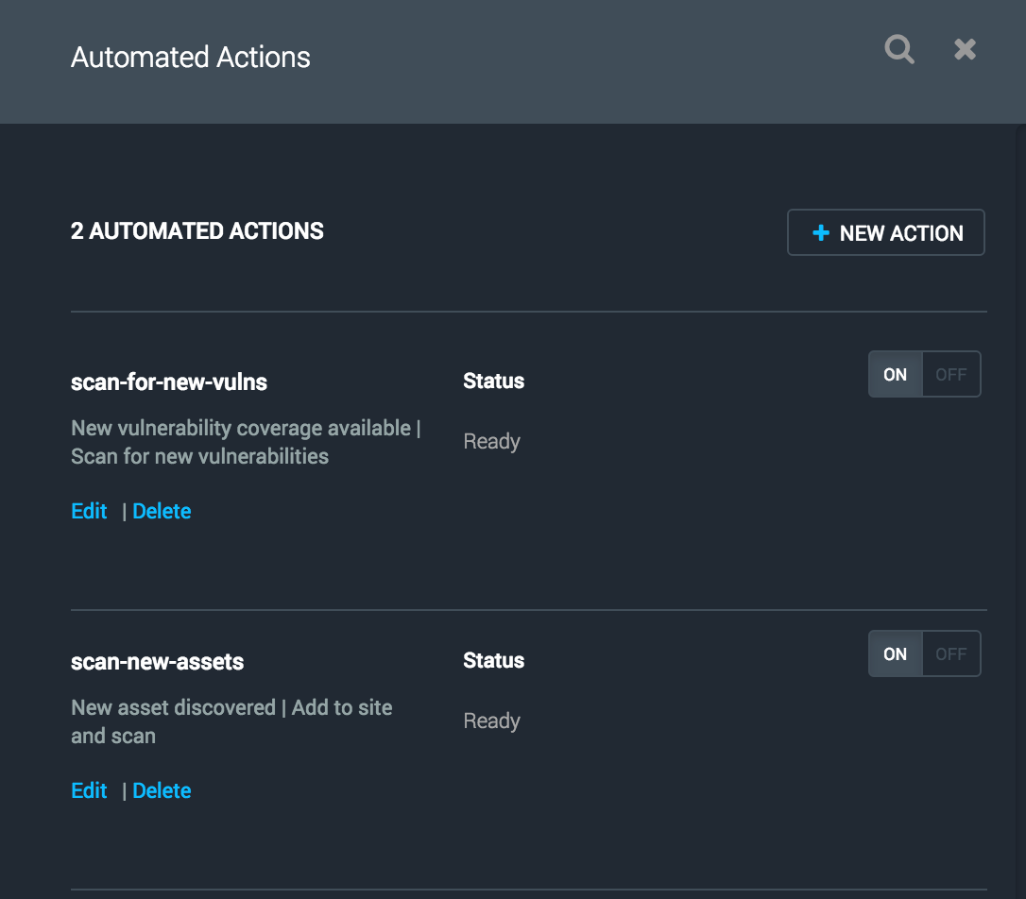
Your new action will now automatically scan the specified site for the new vulnerabilities that are published and meet your filter criteria.
Conclusion
Nexpose was already a major player in your vulnerability management program. Adaptive security makes monitoring possible to complete the loop.