Welcome to Nexpose and the Rapid7 family! This blog is a step by step guide for new Nexpose customers to show you how to set up your first site, start a scan, and get your vulnerability management program under way.
First thing's first: A few definitions in Nexpose:
Site: A (usually) physical group of assets; i.e. what you want to scan
Scan Template: The things that your scan will look for and how it does discovery; i.e. how you scan
Dynamic Asset Group: A filtering of the assets from your scans/sites based on certain criteria like OS, vulnerability, PCI pass/fail, etc.; i.e. how you organize your scan results.
Related Resource: [VIDEO] Learn how to setup dynamic asset groups in Nexpose
To get started, click on the “create site” button on your Nexpose home screen:
Here, give your site a name; as sites are usually logical groupings of your assets, they're often things like “Boston Office” or “LA Datacenter”
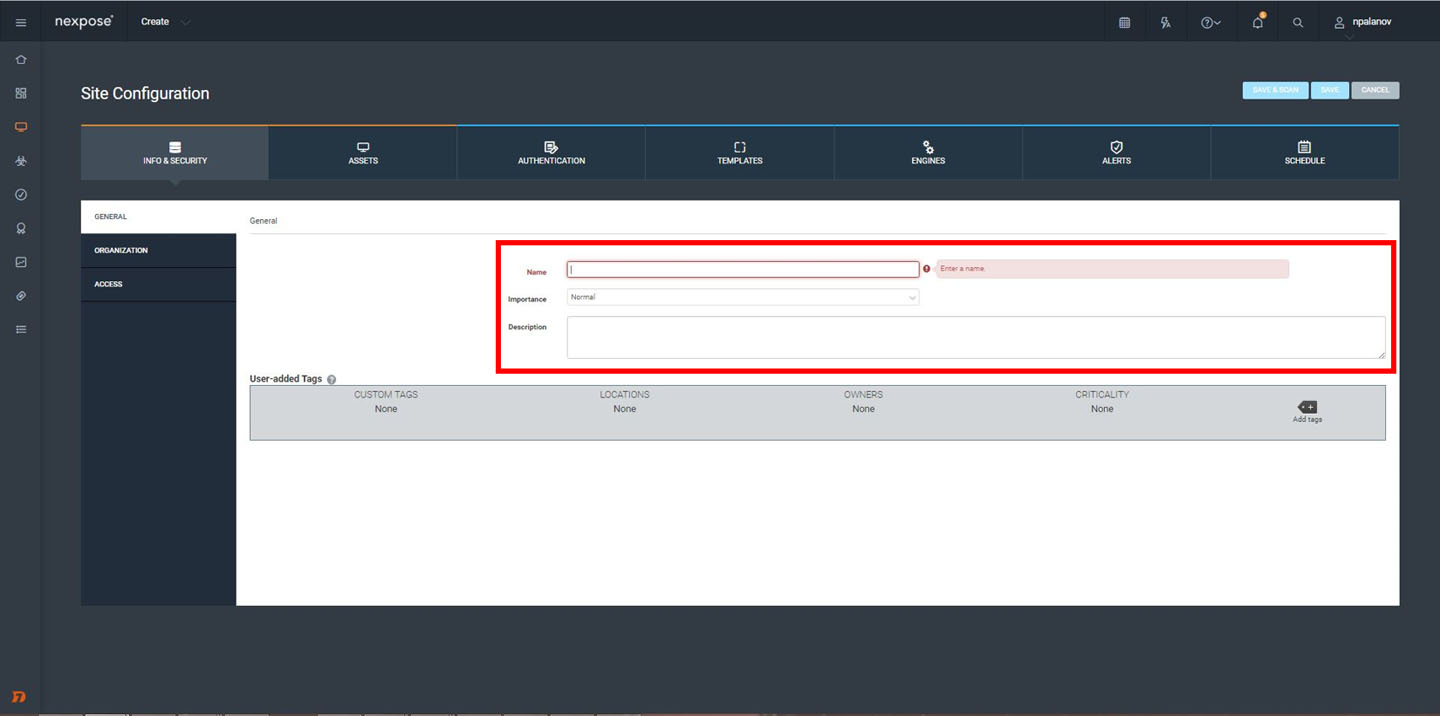
For now, don't worry about the tagging features and the organization/access tabs.
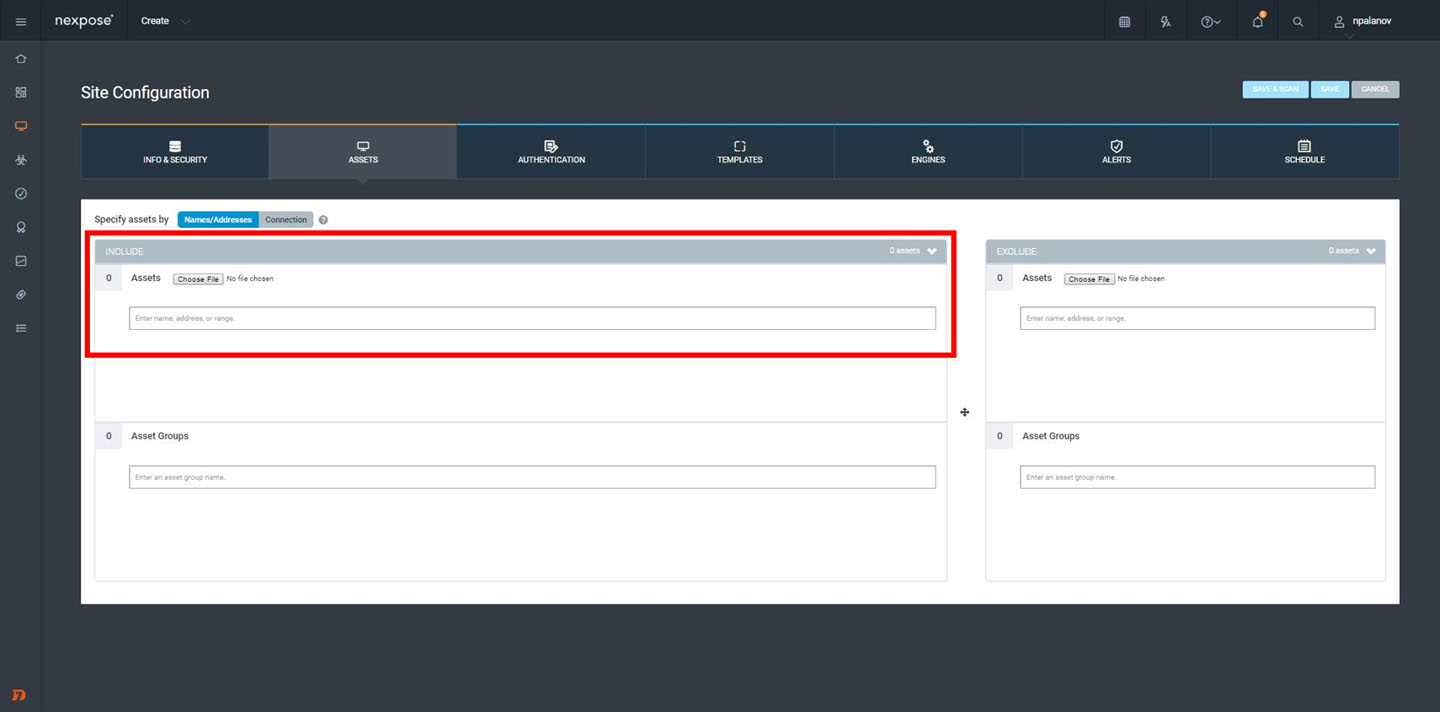
Now let's get into the meat of it. Click into the next section on the top bar, Assets, and enter the assets you want to scan into the “assets” field. You can do this a couple of ways:
- Simply type in or copy/paste a list of addresses (Nexpose accepts all the common formats)
- Import a list of assets from an XML file or similar document
- Create a connection to VMware/AWS/DHCP/ActiveSync and import assets live: We won't cover this in the scope of this blog post, but you can hook Nexpose directly to the tools above to dynamically import assets into an asset group. Simply go to “connection” and “create connection” to hook them up (you can also read up on this process in the user guide or ask our Customer Success Manager).
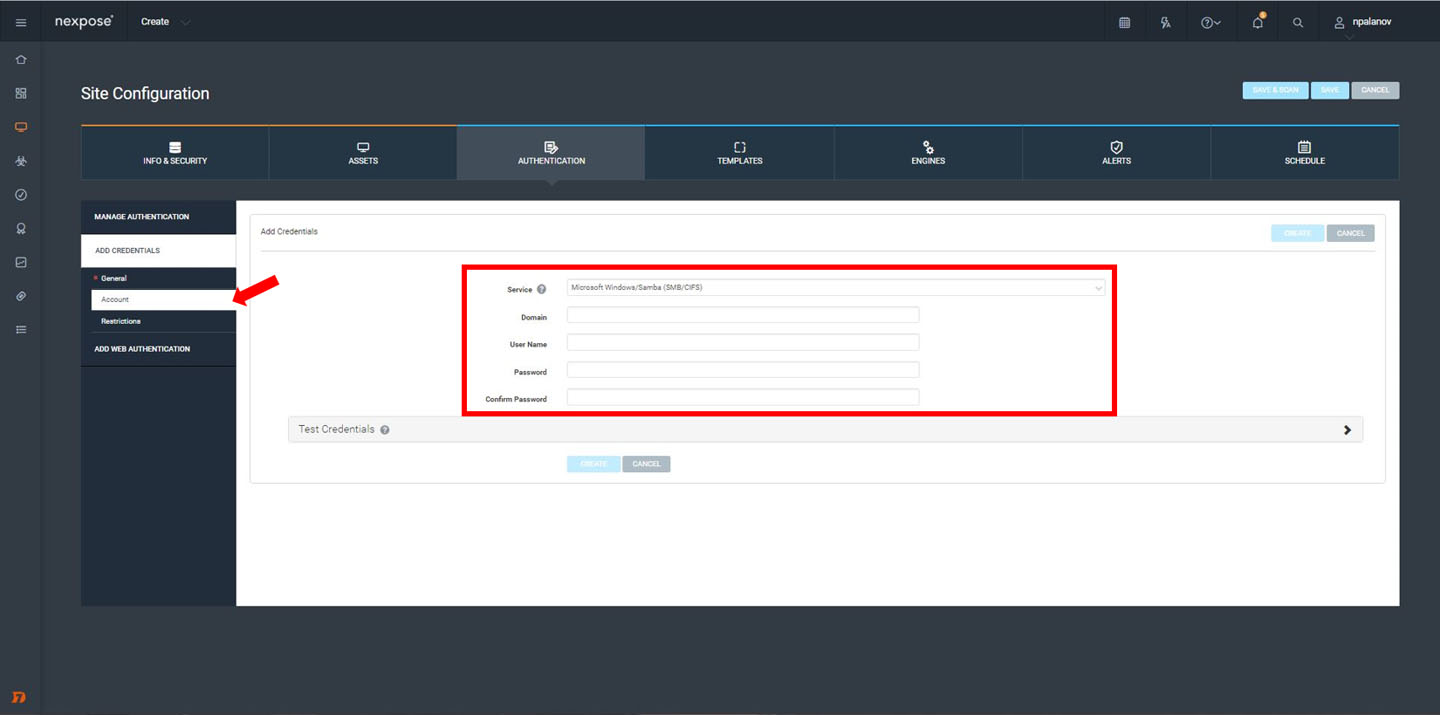
Next let's go to Credentials. Here you can enter credentials so that Nexpose can authenticate into the devices you're scanning. Although not required for scanning, we strongly recommend you do authenticated scanning whenever possible; it'll greatly reduce false positives and give you much more in depth detail on your vulnerabilities, especially for installed software/services.
Go to “add credentials” to give a new set of creds a name, select the service you're using, and input the associated details. You can also test credentials to make sure they're valid. Once you create this, let's move on to Templates!
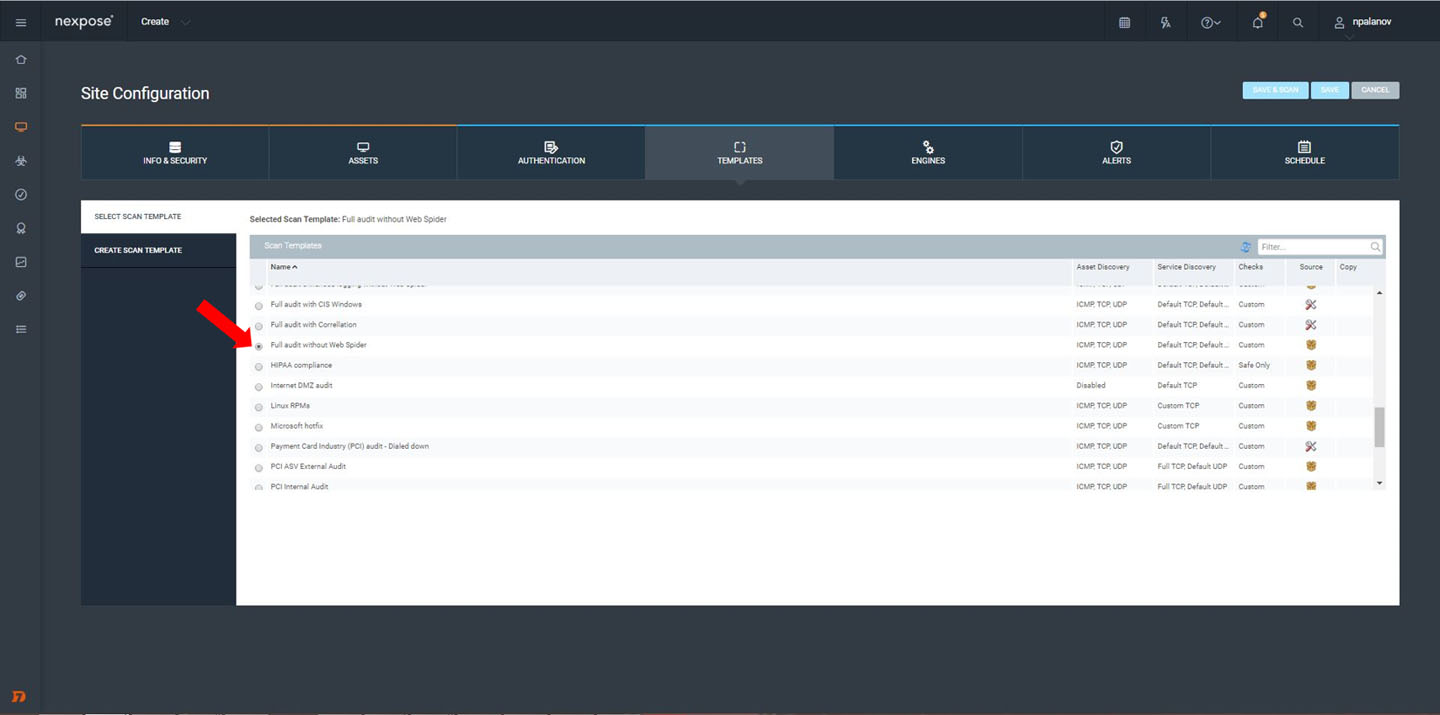
Templates are the way that scans are actually run. We have a whole bunch of prebuilt templates in Nexpose, such as for specific compliance scanning (SOX, PCI, etc) or scanning SCADA systems, and you can also copy and customize any template to get into the nuts and bolts of how Nexpose does its magic.
For our purposes though, a good scan template to start with is Full Audit without Web Spider; this will discover live assets in the range you gave and scan them for all the relevant vulnerability checks in our database, without trying to crawl through web app scanning (which usually needs some more configuration; if web apps are important for you, learn more about our web application security solutions, and be sure to check out AppSpider.
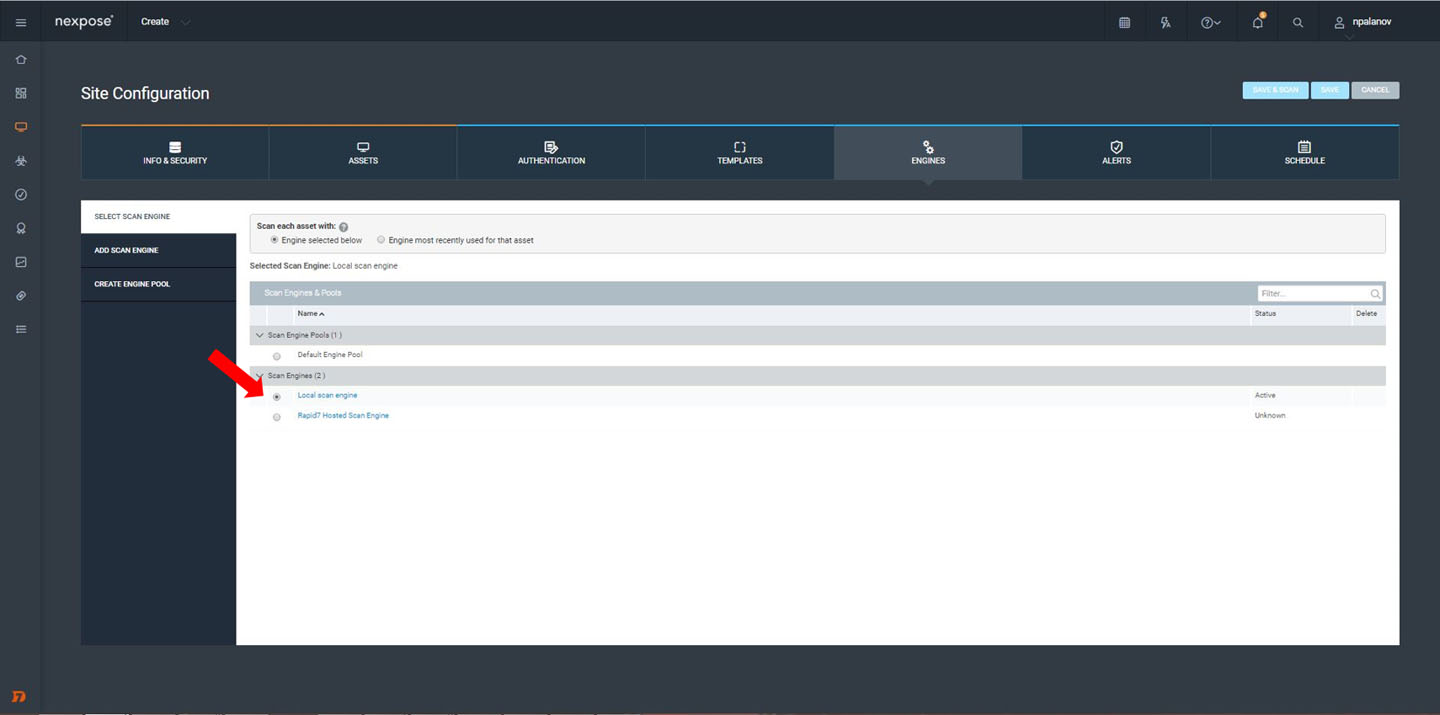
Almost there! The Engines tab lets you select which scan engine you want to do the scan; Nexpose has a distributed architecture that lets you deploy scan engines in remote locations that you don't have access to from the main console, and scan locally.
Your console will come with a scan engine built in, so you can just select “Local scan engine” to launch the scan from your main console.
And that's it! Now you can click “Save and Scan” to launch your scan right away. You can also go to the Schedule section to easily schedule your scans for a later date, or set up a recurring scan schedule.
There's a ton of things you can do to customize your scans and make them more efficient, from custom scan templates to engine pooling and alerts; be sure to reach out to your Customer Success Manager for any questions or check out the Nexpose Training options!