Microsoft is addressing 67 vulnerabilities this June 2025 Patch Tuesday. Microsoft has evidence of in-the-wild exploitation for just one of the vulnerabilities published today, and that is reflected in CISA KEV. Separately, Microsoft is aware of existing public disclosure for one other freshly published vulnerability. Microsoft’s luck holds for a ninth consecutive Patch Tuesday, since neither of today’s zero-day vulnerabilities are evaluated as critical severity at time of publication. Today also sees the publication of eight critical remote code execution (RCE) vulnerabilities. Two browser vulnerabilities have already been published separately this month, and are not included in the total.
Windows WebDAV: zero-day RCE
Remember the WebDAV standard? It has been seven years since Microsoft has published a vulnerability in the Windows implementation of WebDAV, and today’s publication of CVE-2025-33053 is the first zero-day vulnerability on record. Originally dreamed up in the 1990s to support interactivity on the web, WebDAV may be familiar to Exchange admins and users of a certain vintage, since older versions of Exchange, up to and including Exchange Server 2010, supported WebDAV as a means for interacting with mailboxes and public folders.
It will surprise no one that Windows still more or less supports WebDAV, and that turns out to be a bit of a problem. Microsoft acknowledges Check Point Research (CPR) on the advisory; CPR in turn attributes exploitation of CVE-2025-33053 to an APT, which they track as Stealth Falcon, an established threat actor with a long-running interest in governments and government-adjacent entities across the Middle East and the surrounding area.
Curiously, the Microsoft advisory does not mention that the Windows implementation of WebDAV is listed as deprecated since November 2023, which in practical terms means that the WebClient service no longer starts by default. The advisory also has attack complexity as low, which means that exploitation does not require preparation of the target environment in any way that is beyond the attacker’s control. Exploitation relies on the user clicking a malicious link. It’s not clear how an asset would be immediately vulnerable if the service isn’t running, but all versions of Windows receive a patch, including those released since the deprecation of WebClient, like Server 2025 and Windows 11 24H2. On Server 2025, for instance, it’s still possible to install the WebDAV Redirector server feature, which then causes the WebClient service to appear.
SMB client: zero-day EoP
Publicly disclosed elevation of privilege (EoP) zero-day vulnerabilities that lead to SYSTEM are always going to be worth a closer look, and CVE-2025-33073 is no exception. The advisory sets out that the easiest path to exploitation simply requires the user to connect to a malicious SMB server controlled by the attacker. It’s not entirely clear from the advisory whether simply connecting is enough to trigger exploitation, or whether successful authentication is required, since there is currently conflicting language in two separate FAQ entries with almost-identical titles: “How could an attacker exploit this/the vulnerability?” It may well be that Microsoft will come back around and clarify this wording, but in the meantime the only safe assumption is that fortune favours the attacker.
Windows KDC Proxy: critical RCE
The Windows KDC Proxy Service (KPSSVC) receives a patch today for CVE-2025-33071, which describes a critical unauthenticated RCE vulnerability where exploitation is via abuse of a cryptographic protocol weakness. The good news is that only Windows Server assets configured as a Kerberos Key Distribution Center Proxy Protocol server — happily, this is not enabled as standard configuration for a domain controller — and exploitation requires that the attacker win a race condition. The bad news is that Microsoft considers exploitation more likely regardless, and since a KDC proxy helps Kerberos requests from untrusted networks more easily access trusted assets without any need for a direct TCP connection from the client to the domain controller, the trade-off here is that the KDC proxy itself is quite likely to be exposed to an untrusted network. Patching this vulnerability should be top of mind for affected defenders this month.
Office preview pane: trio of critical RCEs
Microsoft expects that exploitation of three Office critical RCE vulns patched today is more likely. CVE-2025-47162, CVE-2025-47164, and CVE-2025-47167 share several attributes: each was discovered by prolific researcher 0x140ce, who topped the MSRC 2025 Q1 leaderboard, and each includes the Preview Pane as a vector, which always ups the ante for defenders. Admins responsible for installations of Microsoft 365 Apps for Enterprise — also confusingly referred to as “Microsoft 365 for Office” in the advisory FAQ — will have to hang on, since patches for today’s vulnerabilities aren’t yet available for that particular facet of the Microsoft 365 kaleidoscope.
Microsoft lifecycle update
June is a quiet month for Microsoft product lifecycle changes. The next batch of significant Microsoft product lifecycle status changes are due in July 2025, when the SQL Server 2012 ESU program draws to a close, along with support for Visual Studio 2022 17.8 LTSC.
Summary charts
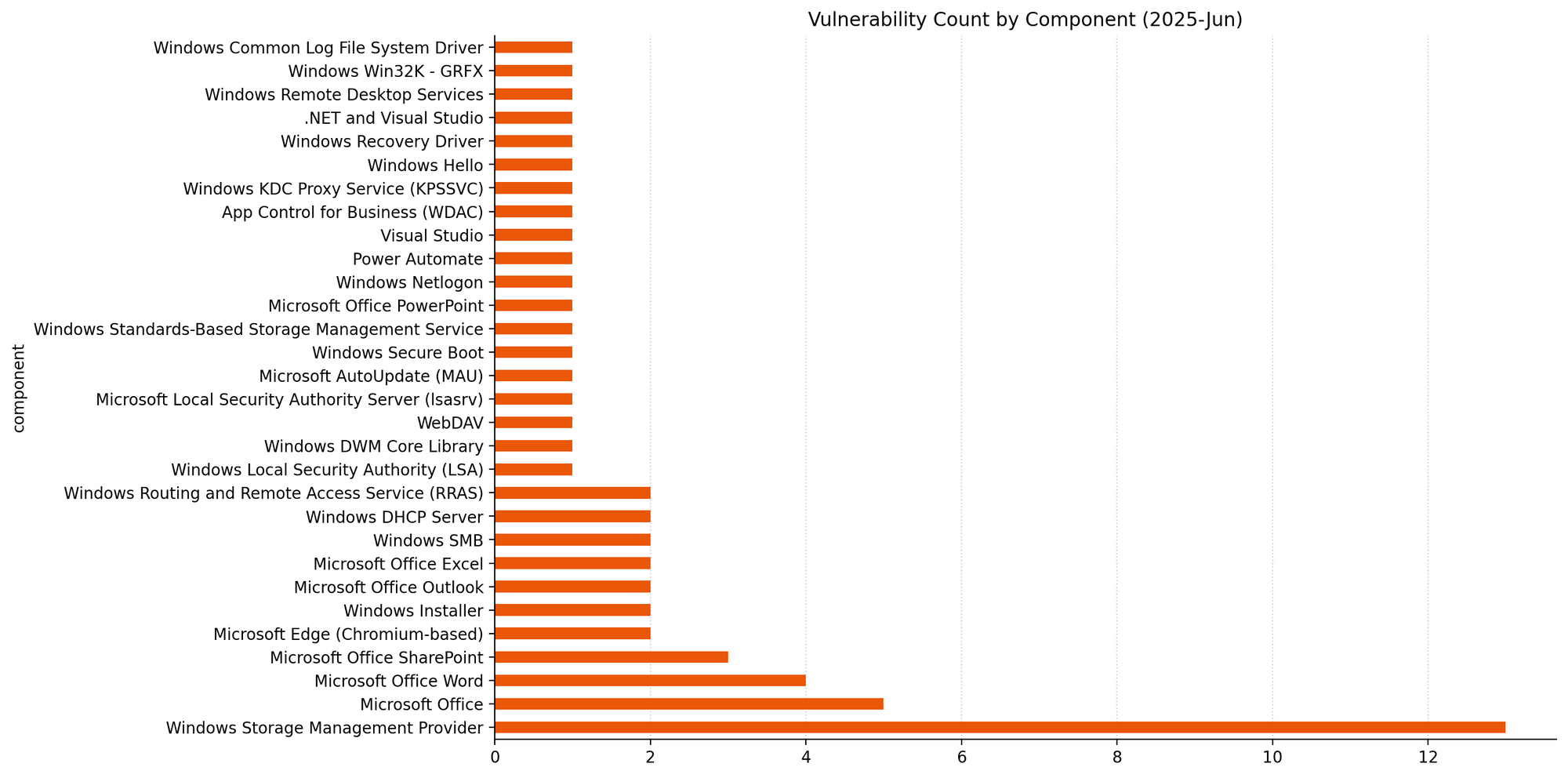
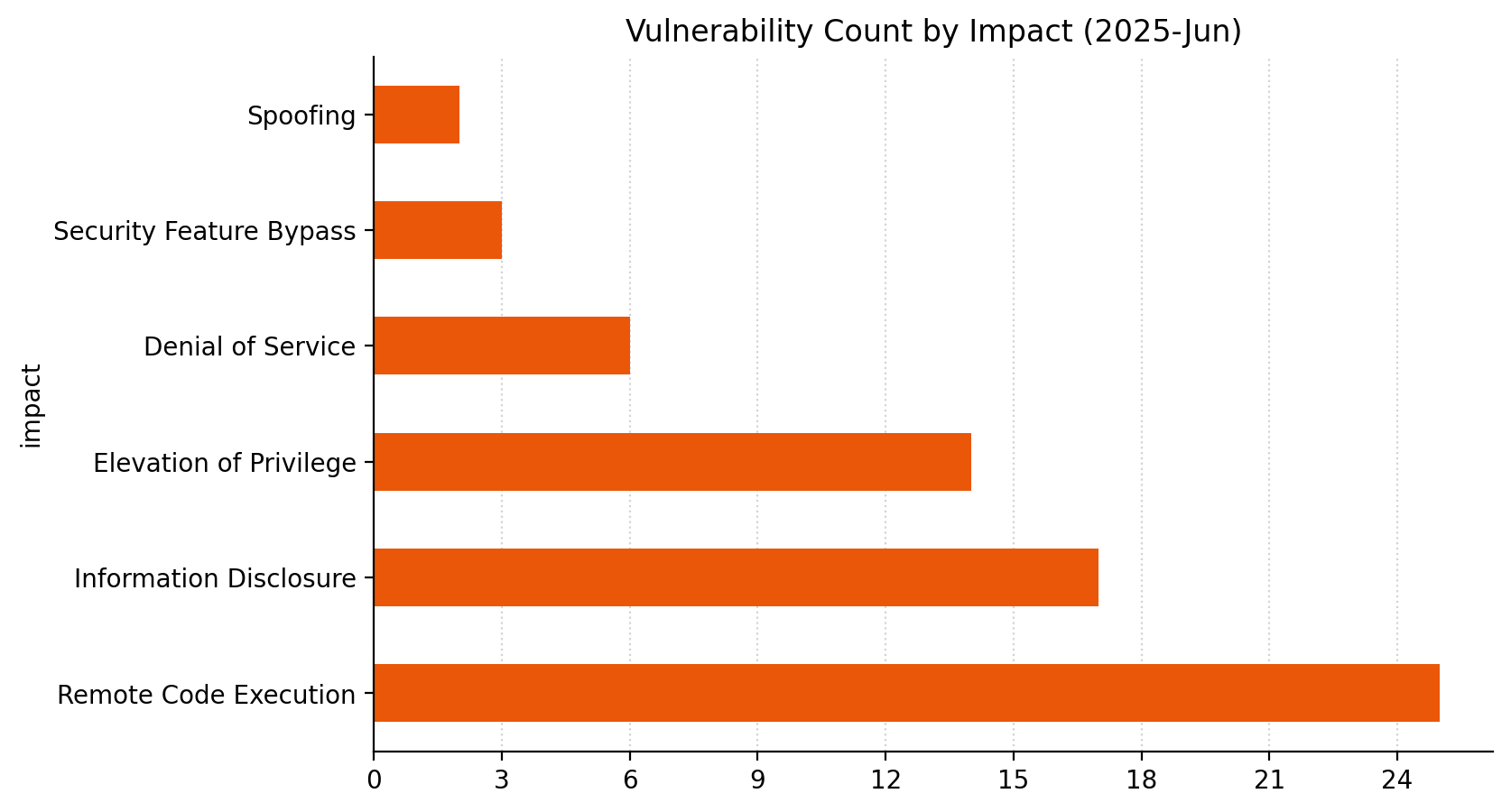
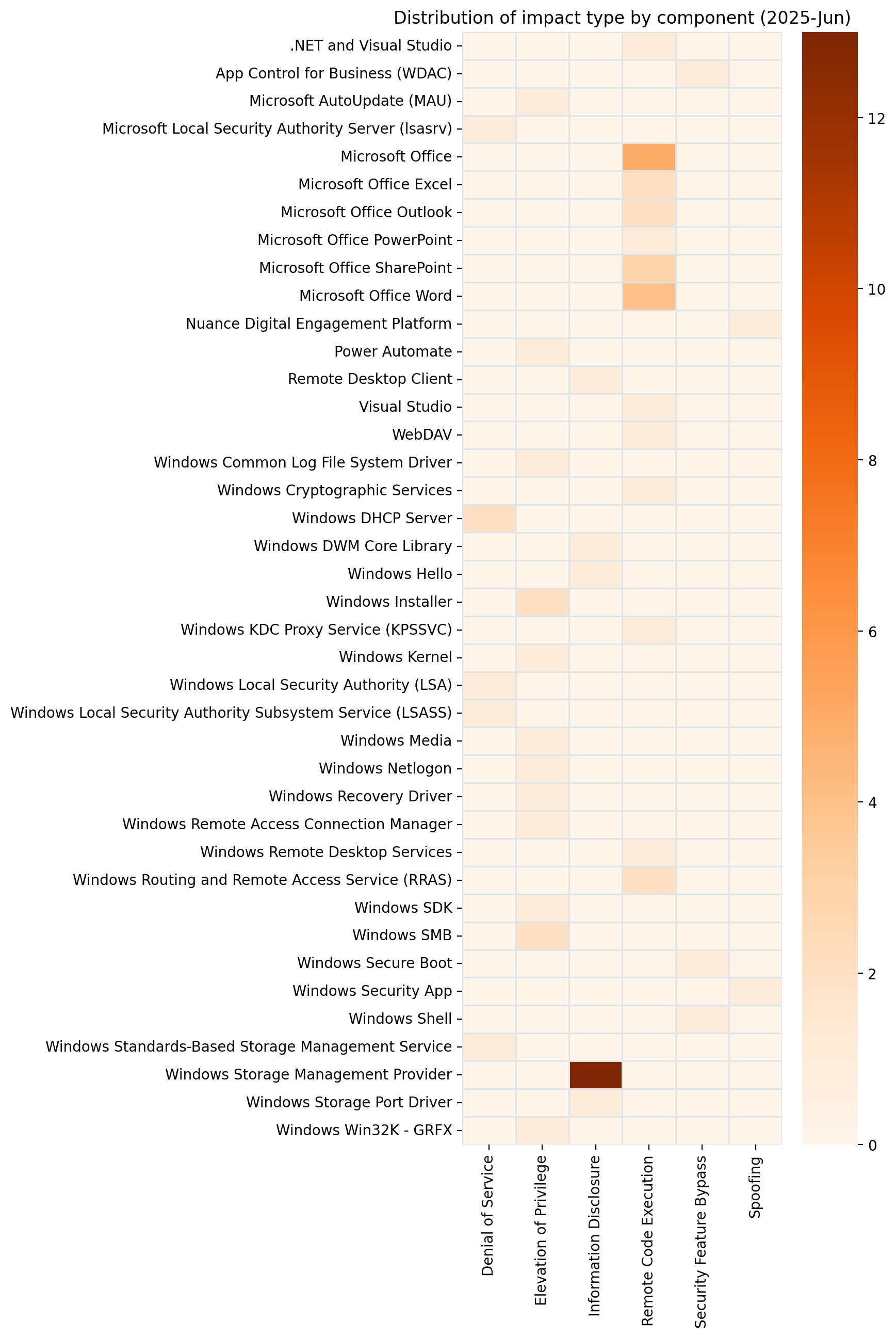
Summary tables
Azure vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-47977 | Nuance Digital Engagement Platform Spoofing Vulnerability | No | No | 7.6 |
Browser vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-5419 | Chromium: CVE-2025-5419 Out of bounds read and write in V8 | No | No | N/A |
| CVE-2025-5068 | Chromium: CVE-2025-5068 Use after free in Blink | No | No | N/A |
Developer Tools vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-47962 | Windows SDK Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-30399 | .NET and Visual Studio Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2025-47959 | Visual Studio Remote Code Execution Vulnerability | No | No | 7.1 |
Microsoft Dynamics vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-47966 | Power Automate Elevation of Privilege Vulnerability | No | No | 9.8 |
Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-47172 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-47163 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-47166 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-47957 | Microsoft Word Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-47162 | Microsoft Office Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-47953 | Microsoft Office Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-47164 | Microsoft Office Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-47167 | Microsoft Office Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-47168 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47169 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47170 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47175 | Microsoft PowerPoint Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47176 | Microsoft Outlook Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47173 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47165 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47174 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-47968 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-47171 | Microsoft Outlook Remote Code Execution Vulnerability | No | No | 6.7 |
Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-33067 | Windows Task Scheduler Elevation of Privilege Vulnerability | No | No | 8.4 |
| CVE-2025-29828 | Windows Schannel Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2025-32725 | DHCP Server Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2025-33050 | DHCP Server Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2025-32721 | Windows Recovery Driver Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2025-32719 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33058 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33059 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33061 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33062 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33063 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33065 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-24068 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-24069 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-24065 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33055 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-47956 | Windows Security App Spoofing Vulnerability | No | No | 5.5 |
| CVE-2025-33052 | Windows DWM Core Library Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33069 | Windows App Control for Business Security Feature Bypass Vulnerability | No | No | 5.1 |
| CVE-2025-47969 | Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability | No | No | 4.4 |
Windows ESU vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-33073 | Windows SMB Client Elevation of Privilege Vulnerability | No | Yes | 8.8 |
| CVE-2025-33064 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-33066 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-33053 | Web Distributed Authoring and Versioning (WEBDAV) Remote Code Execution Vulnerability | Yes | No | 8.8 |
| CVE-2025-32710 | Windows Remote Desktop Services Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2025-33070 | Windows Netlogon Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2025-33071 | Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2025-32718 | Windows SMB Client Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-47955 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-32716 | Windows Media Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-32714 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-33075 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-32713 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-32712 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-33068 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2025-33056 | Windows Local Security Authority (LSA) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2025-32724 | Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2025-3052 | Cert CC: CVE-2025-3052 InsydeH2O Secure Boot Bypass | No | No | 6.7 |
| CVE-2025-33057 | Windows Local Security Authority (LSA) Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2025-32715 | Remote Desktop Protocol Client Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-32722 | Windows Storage Port Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-32720 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-33060 | Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-47160 | Windows Shortcut Files Security Feature Bypass Vulnerability | No | No | 5.4 |

