Executive Summary
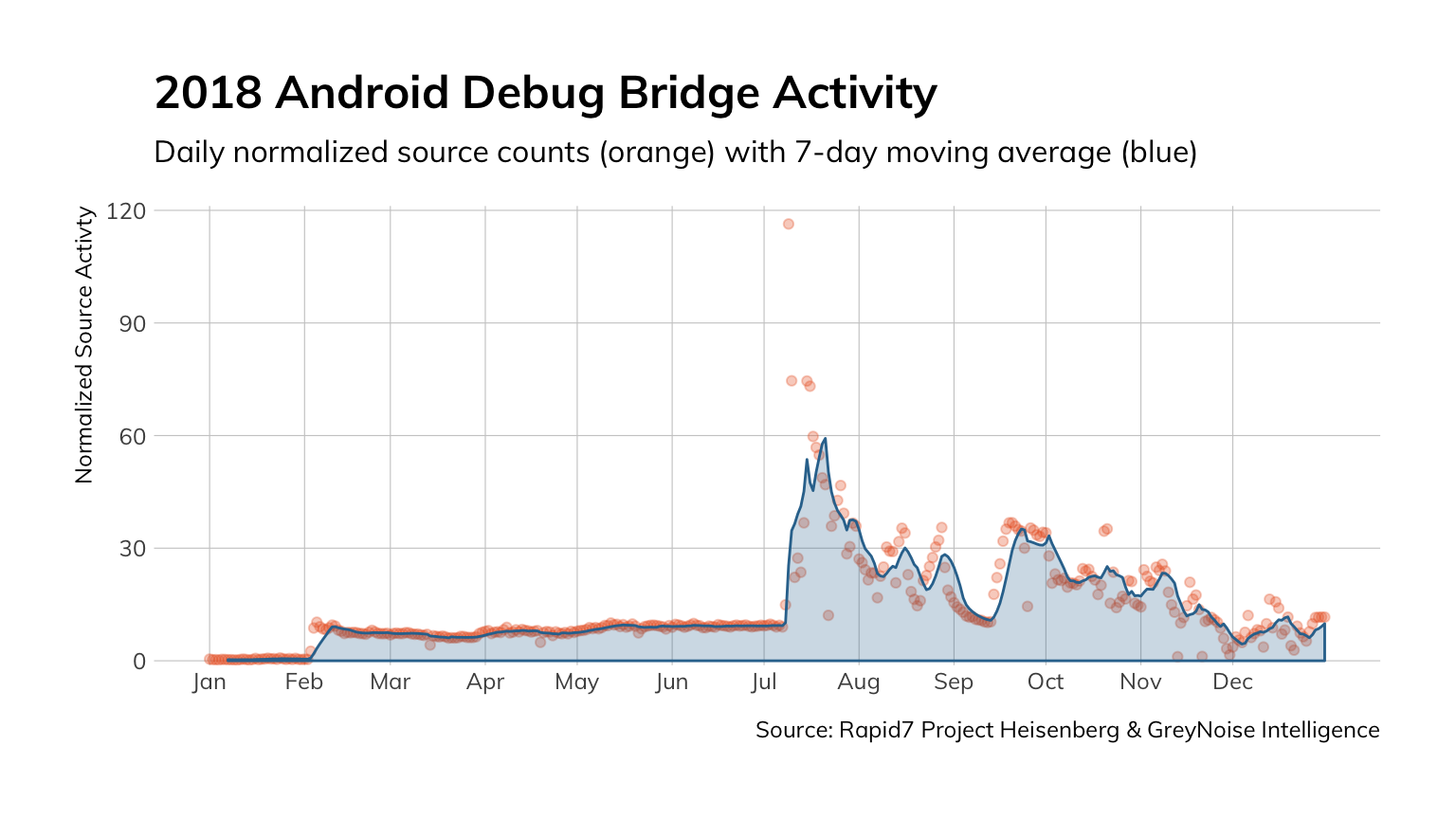
We may have officially kicked off 2019 a few weeks ago, but amidst the confetti our team was hard at work focusing on the big picture threats we saw throughout 2018 and what they might mean for the year ahead. In this issue of the Quarterly Threat Report, we explore inbound activity to our honeypot network to identify trends and patterns that reveal rising new threats, such as Android Debug Bridge (ADB) activity, the persistence of old threats such as EternalBlue, and much more. The report concludes with five steps you can take to bolster your security posture in 2019 and beyond. Read the full report to learn more, and be sure to check out our on-demand webcast to hear directly from researchers what these trends mean for 2019.
Phishing fake-outs continue:
Fake service/ login lures are still working for attackers, with DocuSign-, Dropbox-, and Microsoft-oriented services being the targets of choice for our corpus.
The excellent mileage of EternalBlue:
If the main theme of the ADB/ port 5555 story was “Attackers are innovating,” the theme of the TCP/ port 445 (Microsoft File-Sharing/ SMB) story is “We’ll stick with what works.”
Credential theft and PowerShell use:
We take a look at the most commonly used credential username/password combinations for some popular services, and the vulnerability posed by non-novel credentials as revealed to publicly exposed systems.