Also, there's a lot of focus in the market on exploits, especially with the big celebrity vulnerabilities. And that's great and it helps us because we make vulnerability management software and run the Metasploit product here. But these are areas that companies have mostly covered. The area that really gets companies breached are credentials. We see that both in, for example, the Verizon data breach report, where compromised credentials have been the number one factor why companies get compromised, but we also know it from our penetration testers.
We have a lot of penetration testers. We do about 850 pen test a year, and they tell us that credentials get them in every time. So it's a really important part to pay more attention to. When we talk about detecting compromised credentials, we are really talking about detecting attacker behavior. Because what we're trying to do is we're trying to tell a regular user who's logging in with their credentials to do their own work from an attacker who's using user credentials to log on to systems and to access data. The two look very, very similar when you’re just look at the access data at a high level.
So what we did is we took data, anonymized user data from InsightIDR, which is our user behavior analytics solution that can track things like compromised credentials. And we took about a million users' data and analyzed it and looked at what kind of trends do we see in the data, what helps us better understand what regular user behavior looks like, and how would you use that to secure organizations. This is what I'm here to talk about.
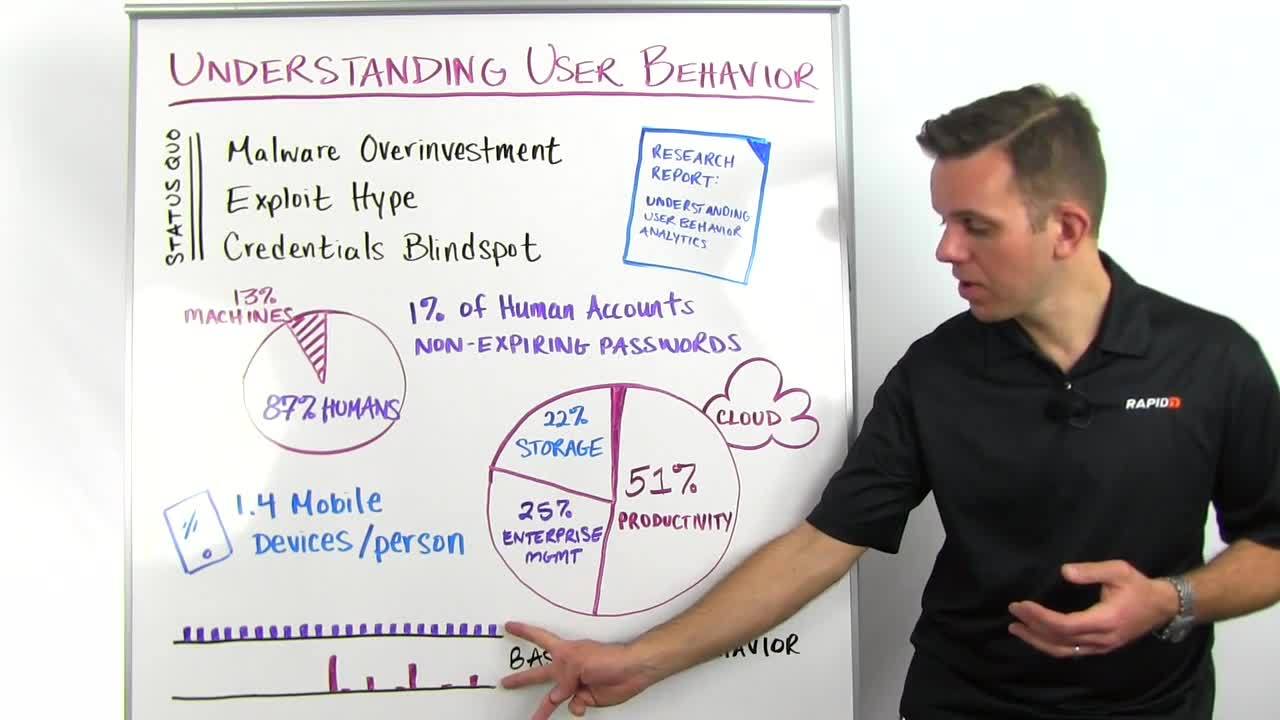
So the first thing that we did is we looked at accounts. We broke accounts down in two different things, human accounts and machine accounts. Now, human accounts is pretty self-explanatory. It's the accounts that you and I would log in with every day. The machine accounts are accounts that, for example, your vulnerability scanner would use to scan the network or your backup servers. This was important to us because these types of accounts behave in very different ways.
If your vulnerability scanner and the associate account does nothing for a month and then accesses a thousand machines at the same time, that's normal behavior. That's completely fine. That's expected. But if I, as a user, don't do anything for a month and then access a thousand machines, that's probably not fine. So knowing what type of account you're looking at is really important to understand what's normal and what's abnormal and what you need to alert on.
One interesting thing that we found is that out of the human accounts, 1% had non-expiring passwords, so weren't complying with the password policy. That data may be a little bit lower than in the general world because InsightIDR alerts you about non-expiring accounts, and a lot of our customers already helped their employees to get into compliance with their password policy.
The other thing we looked at was cloud accounts, cloud services. Here, the idea is that if you know what your employees are using in terms of cloud services, then you can start a conversation and you can say, "All right, you're using this productivity tool, for example, in the cloud, which is great because it increases productivity for the company, so it's actually valuable. Now let's figure out, is it a secure service? How can we better secure that service or can we move you to an equivalent more secure service?" So knowing what users are using is really important to open up that conversation and for you to come in as a security professional and enable the business in a secure way.
One thing that I pay a lot of attention to when I talk to customers is that they also integrate directly with their monitoring program with the strategic cloud services that they have in the enterprise. So if you're thinking of Office365, SalesForce.com, Box.com, those kind of things, high value targets but widely deployed, you actually want to monitor these accounts even if they're being accessed from outside your own environment, and these services have APIs for that.
Because you want to know if somebody is accessing these accounts that are not one of your users, so an attacker. We also looked at mobile devices. Mobile devices are always talked about in how much risk they're adding because they're often BYOD private devices that are accessing company resources. We found that on average, users have about 1.4 mobile devices, so that's smartphones, tablets, those kinds of things, connecting to company services like email.
Now, yes, there may be some risks associated with that, but you can also turn the fact that nobody ever gets separated more than 10 feet from their mobile phone in most cases, you can turn that into an advantage. Because if you know where your phone is accessing your corporate assets from, you know the user location. And if now somebody else logs in to the same user's account from a different location, you can alert on that. So that's actually very powerful.
We also looked at lateral movement, and in that context, baselining behavior inside a company. So what I have here are two graphs. One is showing regular, normal lateral movement that you would see in a company when people are accessing other servers, accessing other machines. So here, this looks like normal behavior and this is just how people use the network. Down here, we're seeing that in the beginning, there was no such behavior in this company and suddenly there's a spike in lateral movement, and them some blips.
That to me, at least, looks like something that you, for sure, want to have a look at because it might be an intrusion. This very much bears a signature of an intrusion. So what's really important to detect lateral movement is to baseline what is normal inside of an organization and then also knowing what attacker behavior looks like. If you're thinking about detecting lateral movement for your security program today, I'd encourage you to also look at solutions or pay attention that the solutions look at local accounts, not just the domain accounts, when you're profiling them.
All right. That's it for today's Whiteboard Wednesday. If you'd like to read about more results that we got out of the data and some partitioner advice, then please download the research report "Understanding User Behavior Analytics" from rapid7.com. I hope to see you next week.