Update (11/17/2010 10:14PM): I've updated the title of this post, based on solely on the fact that I don't think the old title captured the essence of the post, and didn't convey the tone i wanted to take.
Clearly Metasploit is a commercial grade product, so the title is decidedly tongue-in-cheek, but it's important to highlight this fact. A huge benefit of the commercial products is that we now have the resources to provide QA'd snapshots (see below). In addition, every submission is hand-reviewed for correctness, and we regularly run regression tests. I'm very proud that we're able to do this, having been a pentester and run into issues with the framework which could have been caught by a QA pass. It didn't happen more than once, but it was enough to show me the value of having verified code.
The real key to the post below is that we're committed to helping pen testers solve as many of the problems that they run in to, and being as responsive as possible to customers and contributors alike. (How many other development teams do you know that /volunteer/ to take their frontline support requests?) I love hearing from folks, whether it be on the commercial or framework side.
As far as the QA story for the framework, it's only going to improve. Stay tuned for more information, and if you're interested in helping, please contact me ([email protected])!!
Over the last few months, we've received many feature requests for the commercial Metasploit products, and we wanted to give you the low-down on a couple new features that are in direct response to your feedback. Thanks to everyone who has been involved in getting us here, it's been a fun six months.
Metasploit Framework Tested Snapshots
First and foremost, we're now publishing tested weekly snapshots of the Framework. If you have ever run into a bug in the framework, you know how frustrating it can be to try to determine if it's your target, or the framework which is causing an error. With these snapshots, you can be sure the basic functionality of the framework is intact.
These are the same snapshots the commercial products are built upon, and they can be checked out from svn, much the same way that many of you obtain the framework today.To obtain one of the snapshots, simply run an ‘svn checkout' on the latest Metasploit Express or Metasploit Pro version number. For instance, with this week's update:
svn co https://metasploit.com/svn/framework3/tags/framework_20101109220250/
These snapshots are published weekly and links are located with each update's release notes.
Specifying Reverse Payload Connection Settings
One of the most-requested features of the commercial products was the ability to configure the port and address used for the payload connection. Users of the open source framework know these as the LHOST and LPORT options. Since the commercial products are designed to automatically select and launch multiple exploits at once, the criteria for select the correct listener host and port is a bit more complicated than the standard framework.
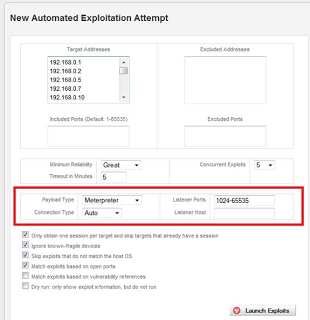
This update provides the ability to specify the listener port and listener address for the Bruteforce, Exploit, and Web Application exploit components, as well as through the Modules tab when doing manual exploit configuration.
The listener port can be specified using the Nmap syntax. For example, a single port (4444), a range of ports (4444-5555), or a list of ports / ranges (4444-5555,5556-6666). The ability to specify the listener address is critical when using the product in certain configurations, such as Amazon EC2 with Elastic IPs.A little background on automatic payload selection: If you've used the commercial Metasploit products, you may have noticed the ‘Auto' setting for the Payload Connection option. This option determines whether the product will listen for a connection from the target or try to connect to a listener running on the target. The Auto setting chooses this value for you based on the network configuration of the system where the product is installed and the configuration of the individual target. To determine whether to use connect-back (Reverse) or listen (Bind), the following rules are consulted.
- A reverse payload is selected when the target is on the same network as the product.
- A reverse payload is selected when the target and the product both use RFC1918 IPs.
- A reverse payload is selected when the target and the product both use external IPs.
- A bind payload is selected when the attacker is behind a NAT gateway
- The bind port is chosen based on the firewall rules of the target
It is possible to override these settings by choosing Reverse or Bind directly. The same rules will apply to choosing the Bind port (consult the firewall configuration of the target) and the Reverse listener port and address (based on what you specify).Concurrent exploits are restricted to the number of specified listeners. If you, for example, enter ‘4444' for the listener port, you will be restricted to one concurrent exploit at a time. To use this option in NAT-> Internet host situations, you'll need to forward ports from your router to your Metasploit host.This makes it easy to launch exploits or bruteforce attacks from one host and catch sessions on another host. For example, you may have one pentester on the target's LAN and a listener on a remote system catching shells provided by the internal pentester.To facilitate the scenario above (internally-launched exploits, remote handler), use Metasploit Pro's USB campaign handler or a Metasploit Framework multi/handler. And don't forget, it's easy to forward a range of ports to a single handler with IPTables:
iptables -t nat -A PREROUTING -p tcp -d $HOST --dport 2000:3000 -j DNAT --to $HOST:1024
Credential Import and Export
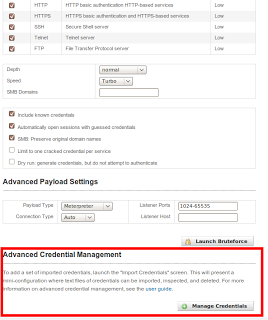
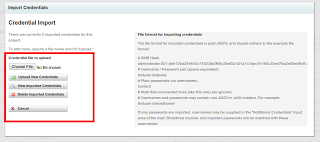
Pass-the-Hash (link) has never been easier now that you can import PWDump files. Simply import the file, select Bruteforce, specify your targets and the imported-only configuration, and prepare to own the network.
Exporting valid credentials is now easy too.
We've also added a new report type of “PWDump.” This generates a simple text file with of all the active credentials for a project. Especially handy is the ability to take this text file and use it directly with John the Ripper to crack SMB hashes. To create one, simply browse to the ‘Reports' page in a project w/ credentials, and select the “PWDump” report type.The files generated by the PWDump report can also be re-imported in two places. In addition to the ‘Manage Credentials' interface, they can be uploaded via the Host > Import tab. If imported in this manner to a new project, the credentials will be treated as unvalidated credentials, and are ready to be validated with a typical bruteforce run.The import of msf credential reports is also available in the framework:
db_import msf_pwdump_report.txt
db_creds
Nmap command line
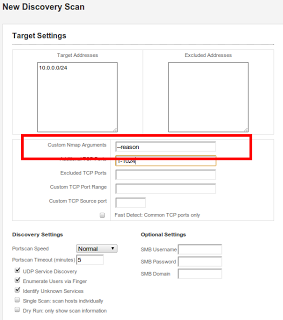
Additionally, The discovery scan has a new option of “Custom Nmap command line.” Here, you can provide options directly to the nmap command line. Specifically, this enables users to exercise more granular control over timing options (max retires, host timeouts, etc) and scan
types (maybe you want to just ACK and Xmas scan). Some limitations:Disallowed options: Users cannot set the target list (-i), set the port list (-p), or set the output options (-o). The first two are handled capability by the UI, and the last is for basic file system security (no need to allow output to be redirected willy-nilly).Administrator only: In multi-user environments, only the administrators have this option. Otherwise, it's too easy for users to ignore the project's scope and boundaries.Nmap scanning is also available in the framework:
db_nmap [options]
Source port scanning
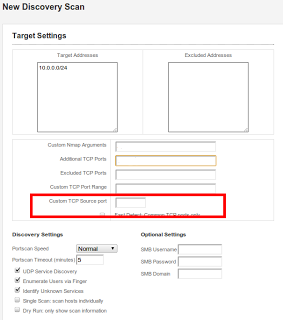
Another handy feature, and something that's often an afterthought (or missing entirely) in vulnerability scanners is source port scanning. This is super easy to configure during discovery:
**What about msfconsole?**Many of you have requested console access from within the commercial Metasploit products, and we're happy to report that you can absolutely use a console to interact with the commercial products.
Since the Framework is snapshotted, packaged, and used as the engine of the commercial versions, you can use the following commands as root:
/opt/metasploit-3.5.0/diagnostic_shell
ruby /opt/metasploit-3.5.0/apps/pro/msf3/msfconsole
-e production -y /opt/metasploit-3.5.0/apps/pro/ui/config/database.yml
This will give you a msfconsole instance tied to the Metasploit Express/Pro database. Although not everything will work the way you would expect (for example, sessions cannot be shared), this will enable you to track session data and hosts and access this information in the Web Interface.