On Sept. 6, 2019, the Exim development team released a patch for CVE-2019-15846, which fixed a privileged, unauthenticated remote code execution (RCE) weakness in its popular internet email server software. Exim is one of the most popular mail transfer agents (MTAs) running on the open internet today.
Attackers who successfully exploit this flaw will gain full “root” access to their target systems.
Organizations that run Exim—which would include major corporations, regional ISPs, state universities, and other large organizations—are strongly encouraged to patch their systems immediately, as the Exim team has a working, private proof-of-concept (PoC) exploit for this vulnerability. Currently, there are no known public exploits for CVE-2019-15846, but that could change at any time. Mitigation is possible without patching, but it requires disabling the ability to send encrypted mail, which is not recommended for privacy reasons.
Versions of Exim prior to 4.80 do not appear to be vulnerable to this particular RCE vulnerability, but do have other remote code execution flaws and other serious issues that make them even more vital to get up and running on current, patched releases.
Organizations using cPanel to manage Exim can follow cPanel’s patch guidance to ensure they are running a version of Exim that is not vulnerable to CVE-2019-15846. cPanel is one of the most popular GUI administration wrappers for Exim and is used extensively in Exim deployments.
Rapid7 InsightVM and Nexpose customers have full scan coverage available for this vulnerability as of Sept. 7, 2019.
Not a customer of ours? Scan your environment for this vulnerability today with our free 30-day InsightVM trial.
Get StartedInternet-facing Exim
The Rapid7 Labs team regularly scans for internet mailers via Project Sonar and found over 5 million live Exim servers, of which over 4.5 million had detectable, valid version numbers.
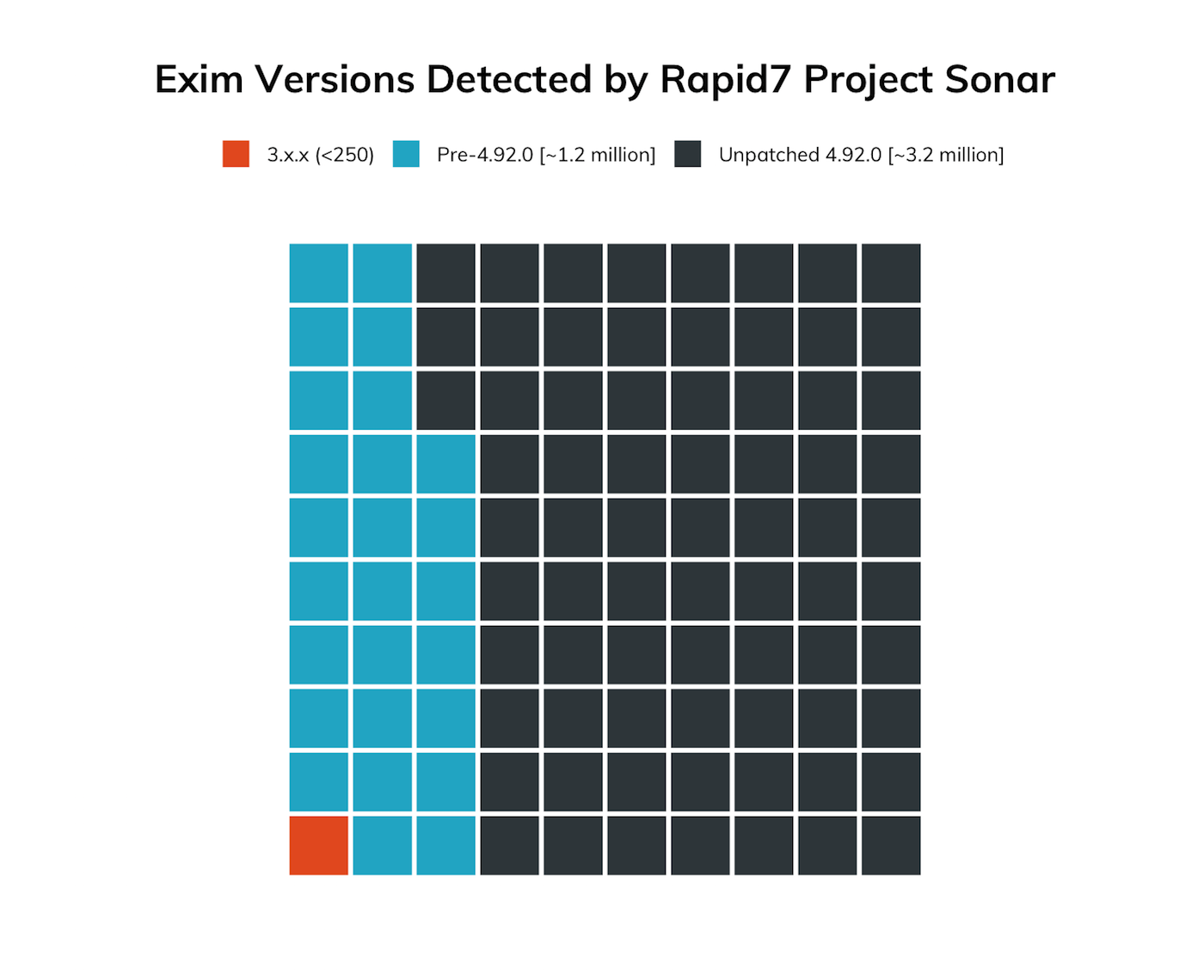
Over 73% of Exim versions detected were at version 4.92.0, which is the latest version prior to the patch release. This is great news, since it indicates most organizations that run Exim servers seem to prioritize keeping this critical server software up-to-date, so we expect that most email administrators will have it patched well before the next Sonar SMTP server study run.
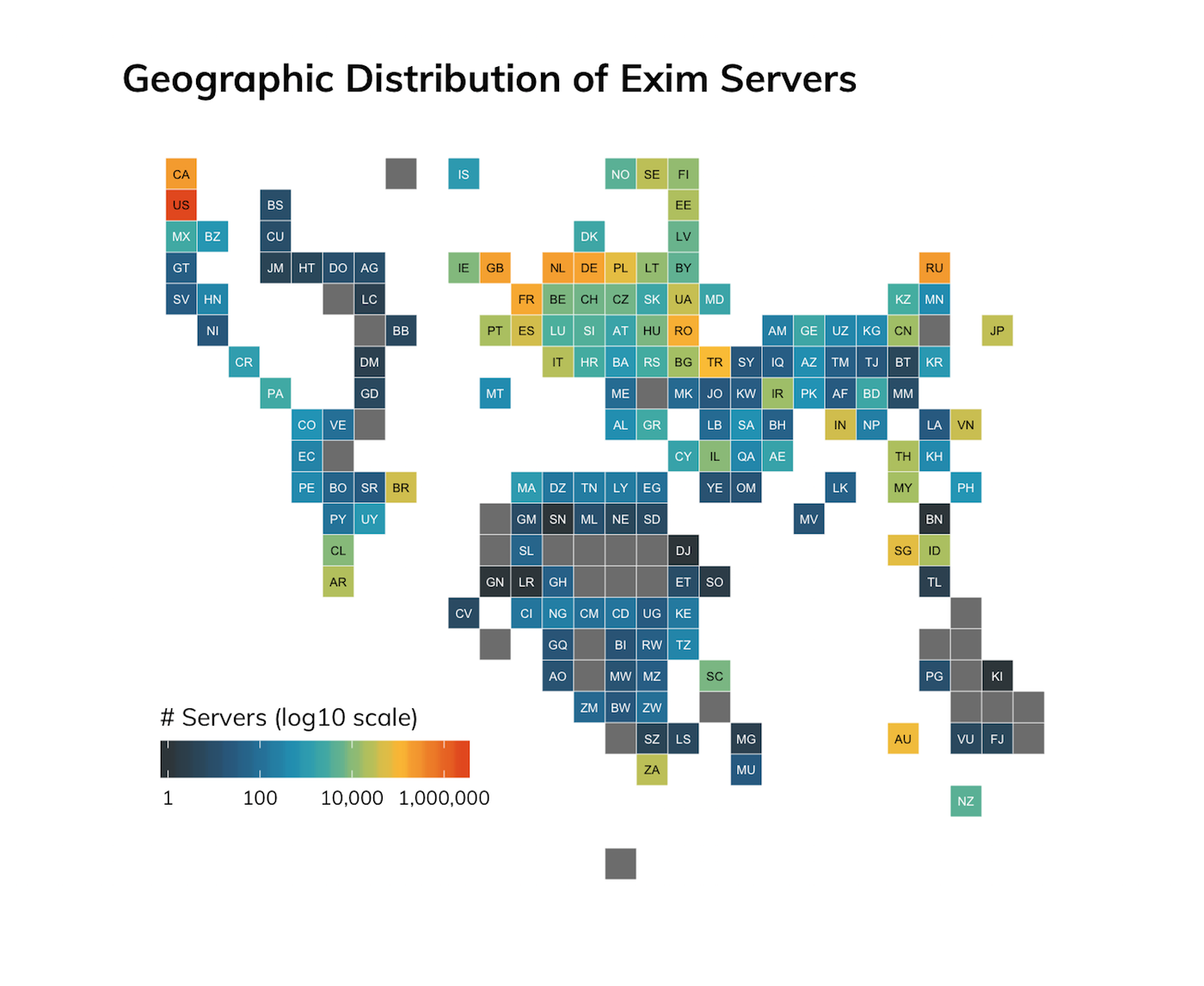
Unsurprisingly, organizations and hosting providers in the United States have a large percentage (>51%) of Exim deployments, and there are concentrations in the 1%–5% range in most of the other countries that top internet-system counts lists.
| Provider | n | % |
|---|---|---|
| Unified Layer | 764,536 | 16.15% |
| OVH SAS | 303,647 | 6.41% |
| Liquid Web, L.L.C | 140,632 | 2.97% |
| InMotion Hosting, Inc. | 130,142 | 2.75% |
| EGIHosting | 95,816 | 2.02% |
| Hetzner Online GmbH | 85,922 | 1.81% |
| A Small Orange LLC | 84,819 | 1.79% |
| A2 Hosting, Inc. | 74,798 | 1.58% |
| DigitalOcean LLC | 56,472 | 1.19% |
| JSC The First | 54,698 | 1.16% |
For a change, most cloud hosting providers aren’t in the top 10, save for Digital Ocean. This is due, in part, to a high concentration of Exim in Unified Layer, a hosting provider that has a fairly troubled record when it comes to email protection. If you run Exim in any of the hosting providers in the “top 10” and manage it yourself, you should strive to patch even more quickly, since these high concentrations will be very tempting mass-targets for attackers once a public exploit becomes available.
SMTP Scanning and Attack Activity
The Rapid7 Labs team also looked at SMTP probe and attack activity via Project Lorelei.
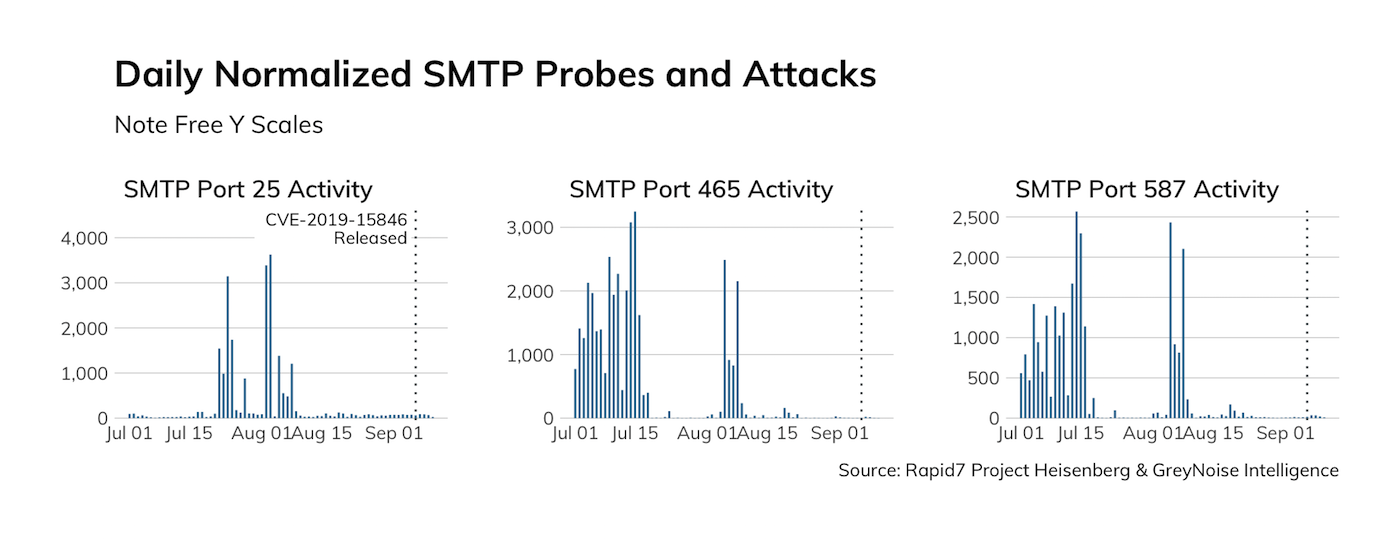
While there have been a few large SMTP spam and compromise campaigns since the beginning half of the year, there does not appear to be a significant amount of increased activity as a result of the publication of this Exim weakness.
If we zoom in to just September 2019, we see that there was a slight uptick in probes after the release of the patch, which were very likely inventory scans:
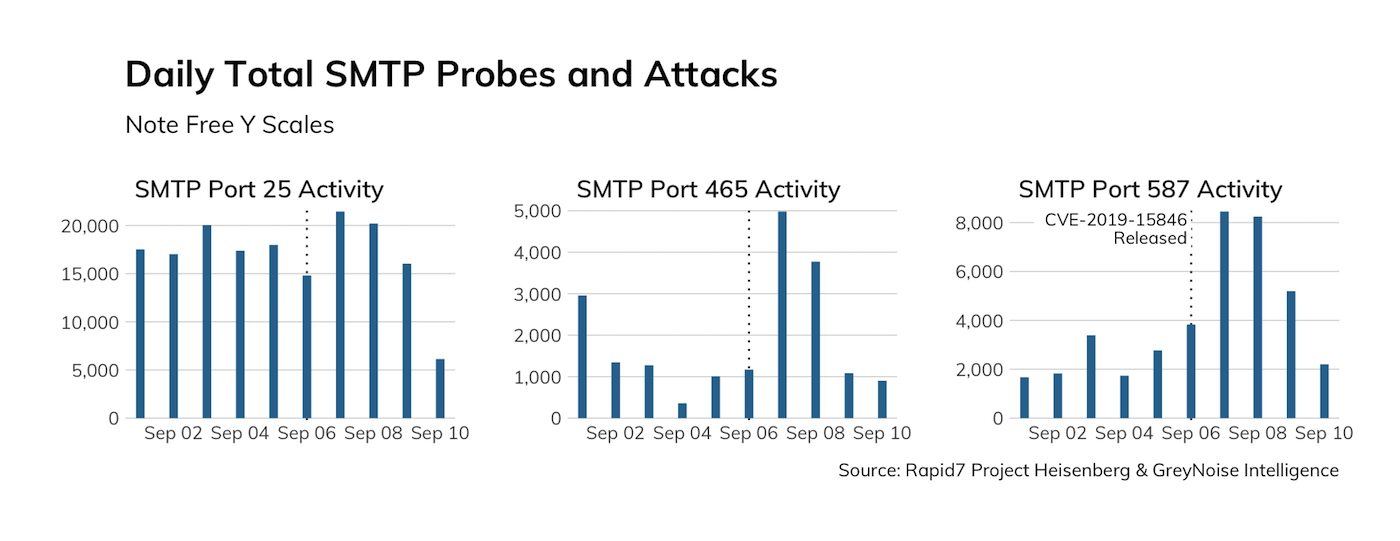
None of this activity appears to be trying to exploit this new Exim vulnerability (i.e., the payloads are all inventory-related vs. compromise-oriented). A public exploit is very likely to exist soon—it only takes the inclusion of a backslash-null sequence in one field during a client’s initial TLS handshake with a vulnerable Exim server.
Rapid7 Labs will monitor SMTP activity, watch for the release of a public exploit, and provide updates as warranted.
