Overview of the SAML authentication vulnerability on PAN-OS devices
released detailsCVE-2020-2021- PAN-OS 9.1 versions earlier than PAN-OS 9.1.3
- PAN-OS 9.0 versions earlier than PAN-OS 9.0.9
- PAN-OS 8.1 versions earlier than PAN-OS 8.1.15
- All versions of PAN-OS 8.0 (EOL)
However, it does not affect PAN-OS 7.1.
As of this post, there are no known proof-of-concept exploits available.
Rapid7 recommends patching your PAN-OS devices regardless of whether organizations are exposing this specific configuration, but sites that do have their PAN-OS devices configured this way should patch immediately.Security Assertion Markup Language (SAML) is an open standard that allows identity providers (think Okta, Duo, etc.) to pass authorization credentials to service providers. In other words, you can use one set of credentials to access many different websites or, in this case, devices.
enabledAttackers require network access to take advantage of this weakness, which means users of Palo Alto’s Global Protect VPN are susceptible to this vulnerability if configured with SAML authentication and identity provider certificate validation is disabled.
Exposure analysis of CVE-2020-2021
Organizations using Palo Alto images in the AWS Marketplace should take care to use VM-Series Next-Generation Firewall Bundles 1 or 2 vs. the legacy images, as only the newer ones are at >= 9.1.3 as of this post. We note this since Project Sonar discovered over 2,000 Palo Alto GlobalProtect nodes in AWS across 16 AWS regions.
Similarly, Rapid7 Labs found just under 1,500 Palo Alto GlobalProtect nodes in Microsoft Azure and recommends updating to the latest bundles there as well.
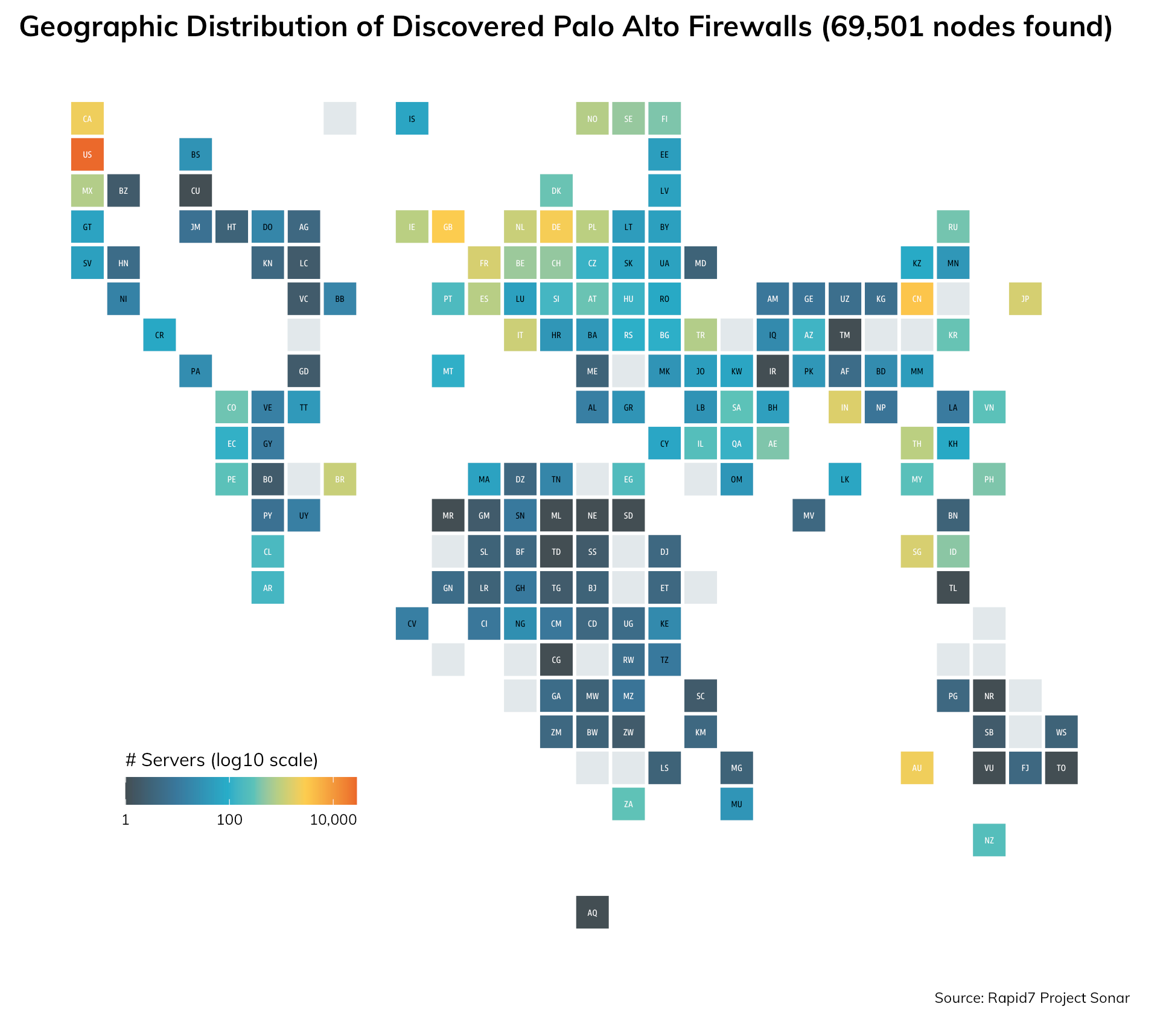
We have no specific Sonar study for GlobalProtect PAN-OS devices, but our combined generic studies discovered just over 69,000 nodes, 28,188 (40.6%) of which are in the U.S.
| Country | Count | % |
|---|---|---|
| United States | 28,188.0 | 40.56% |
| China | 3,538.0 | 5.09% |
| United Kingdom | 2,956.0 | 4.25% |
| Germany | 2,518.0 | 3.62% |
| Australia | 2,279.0 | 3.28% |
| Canada | 2,240.0 | 3.22% |
| India | 1,572.0 | 2.26% |
| Singapore | 1,414.0 | 2.03% |
| France | 1,389.0 | 2.00% |
| Japan | 1,369.0 | 1.97% |
| Italy | 1,186.0 | 1.71% |
| Taiwan | 1,136.0 | 1.63% |
| Netherlands | 1,128.0 | 1.62% |
| Brazil | 1,115.0 | 1.60% |
| Thailand | 914.0 | 1.32% |
| Poland | 910.0 | 1.31% |
| Ireland | 899.0 | 1.29% |
| Spain | 849.0 | 1.22% |
| Norway | 820.0 | 1.18% |
| Turkey | 791.0 | 1.14% |
While this particular advisory is specific to PAN-OS, it’s likely that other vendors’ SAML implementations are vulnerable to similar issues. Developers and the broader security community would be well-advised to ensure that code with implications for SAML is reviewed thoroughly, since the severity of vulnerabilities affecting authentication mechanisms is inherently high.
Rapid7 Labs will update this blog post as new information is received.
