Microsoft is offering fixes for 114 vulnerabilities for April 2023 Patch Tuesday. This month’s haul includes a single zero-day vulnerability, as well as seven critical Remote Code Execution (RCE) vulnerabilities. There is a strong focus on fixes for Windows OS this month.
Zero-day vulnerability: CLFS
Over the last 18 months or so, Rapid7 has written several times about the prevalence of driver-based attacks. This month's sole zero-day vulnerability – a driver-based elevation of privilege – will only reinforce the popularity of the vector among threat actors. Successful exploitation of CVE-2023-28252 allows an attacker to obtain SYSTEM privileges via a vulnerability in the Windows Common Log File System (CLFS) driver. Microsoft has patched more than one similar CLFS driver vulnerability over the past year, including CVE-2023-23376 in February 2023 and CVE-2022-37969 in September 2022.
Microsoft has released patches for the zero-day vulnerability CVE-2023-28252 for all current versions of Windows. Microsoft is not aware of public disclosure, but has detected in-the-wild exploitation and is aware of functional exploit code. The assigned base CVSSv3 score of 7.8 lands this vulnerability near the top of the High severity range, which is expected since it gives complete control of an asset, but a remote attacker must first find some other method to access the target.
Critical RCE: MSQS, Raw Image Extension, DHCP etc.
April 2023 also sees 45 separate Remote Code Execution (RCE) vulnerabilities patched, which is a significant uptick from the average of 33 per month over the past three months.
Microsoft rates seven of this month’s RCE vulnerabilities as Critical, including two related vulnerabilities with a CVSSv3 base score of 9.8. CVE-2023-28250 describes a vulnerability in Windows Pragmatic General Multicast (PGM) which allows an attacker to achieve RCE by sending a specially crafted file over the network. CVE-2023-21554 allows an attacker to achieve RCE by sending a specially crafted Microsoft Messaging Queue packet. In both cases, the Microsoft Message Queueing Service must be enabled and listening on port 1801 for an asset to be vulnerable. The Message Queueing Service is not installed by default. Even so, Microsoft considers exploitation of CVE-2023-21554 more likely.
The other five Critical RCE this month are spread across various Windows components: Windows Raw Image Extension, Windows DHCP Protocol, and two frequent fliers: Windows Point-to-Point Tunneling Protocol and the Windows Layer 2 Tunneling Protocol.
The RAW Image Extension vulnerability CVE-2023-28921 is another example of what Microsoft refers to as an Arbitrary Code Execution (ACE), explaining “The attack itself is carried out locally. This means an attacker or victim needs to execute code from the local machine to exploit the vulnerability.” For some defenders, this may stretch the definition of the word Remote in Remote Code Execution, but there are many ways to deliver a file to a user, and an unpatched system remains vulnerable regardless.
DHCP server vulnerability CVE-2023-28231 requires an attacker to be on the same network as the target, but offers RCE via a specially crafted RPC call. Microsoft considers that exploitation is more likely.
Defender: Denial-of-Service
The hunter becomes the hunted as Microsoft patches a Denial of Service vulnerability in Defender. The advisory for CVE-2023-24860 includes some unusual guidance: “Systems that have disabled Microsoft Defender are not in an exploitable state.” In practice this vulnerability is less likely to be exploited, and the default update cadence for Defender should mean that most assets are automatically patched in a short timeframe.
Windows Server: remote kernel memory disclosure
Windows Server administrators should take note of CVE-2023-28247. Successful exploitation allows an attacker to view contents of kernel memory remotely from the context of a user process. Microsoft lists Windows Server 2012, 2016, 2019, and 2022 as vulnerable. Although Microsoft assesses that exploitation is less likely, Windows stores many secrets in kernel memory, including cryptographic keys.
Active Directory Certificate Services: tighter Kerberos authentication
Back in May 2022, Microsoft publicized a trio of related Elevation of Privilege vulnerabilities affecting the Key Distribution Center (KDC) via Kerberos: CVE-2022-26923 (aka Certifried), CVE-2022-26931, and CVE-2022-34691. Insufficient validation allowed certificate spoofing under certain circumstances. The April 2023 security updates introduce further relevant changes.
The May 2022 patches for all affected versions of Windows introduced a two-tiered remediation for this trio of vulnerabilities:
- Full Enforcement mode: require strong mapping for certificates, otherwise authentication is denied. Microsoft intends to make this the default setting by November 2023.
- Compatibility mode: some allowance for weak mapping of certificates, but old certificates will still result in denial. This has been the default behaviour since May 2022.
Microsoft provided a time-limited ability to disable this security remediation entirely using a registry key. Although none of these vulnerabilities are listed in Microsoft's April 2023 Security Updates Release Notes, administrators should note that Windows assets with the April 2023 updates installed will now ignore the registry key which previously disabled these certificate mapping checks. Microsoft provides guidance to administrators concerned with the balance of usability vs. security.
In addition to detection of vulnerable assets via InsightVM, Rapid7 offers a Metasploit module allowing fully-automated privilege escalation using the Certifried vulnerability, as well as a thorough AttackerKB analysis.
Azure: information disclosure and security bypass
Machine learning is everywhere these days, and this month’s Patch Tuesday is no exception: CVE-2023-28312 describes a vulnerability in Azure Machine Learning which allows an attacker to access system logs, although any attack would need to be launched from within the same secure network. The advisory contains links to Microsoft detection and remediation guidance.
The other Azure vulnerability this month is a Azure Service Connector Security Feature Bypass. Microsoft rates Attack Complexity for CVE-2023-28300 as High, since this vulnerability is only useful when chained with other exploits to defeat other security measures. However, the Azure Service Connector only updates when the Azure Command-Line Interface is updated, and automatic updates are not enabled by default.
End-of-life: the class of 2013
Final curtain call tonight for a raft of familiar names, since April 2023 Patch Tuesday includes the very last round of Extended Security Updates (ESU) for a number of Microsoft products. These include:
- Exchange Server 2013.
- Lync Server 2013.
- Office 2013 and individual component applications such as Excel 2013, PowerPoint 2013 etc.
- Project 2013 and Project Server 2013.
- SharePoint Server 2013 and SharePoint Foundation 2013.
- Skype for Business 2015; the 2016 edition is still in ESU until October 2025.
As always, the end of ESU means that Microsoft does not expect to patch or even disclose any future vulnerabilities which might emerge in these venerable software products, so it is no longer possible to secure them; these dates have been well-publicized far in advance under the fixed lifecycle policy. No vendor can feasibly support ancient software indefinitely, and some administrators may be glad that they will never have to install another Exchange Server 2013 patch.
Summary Charts
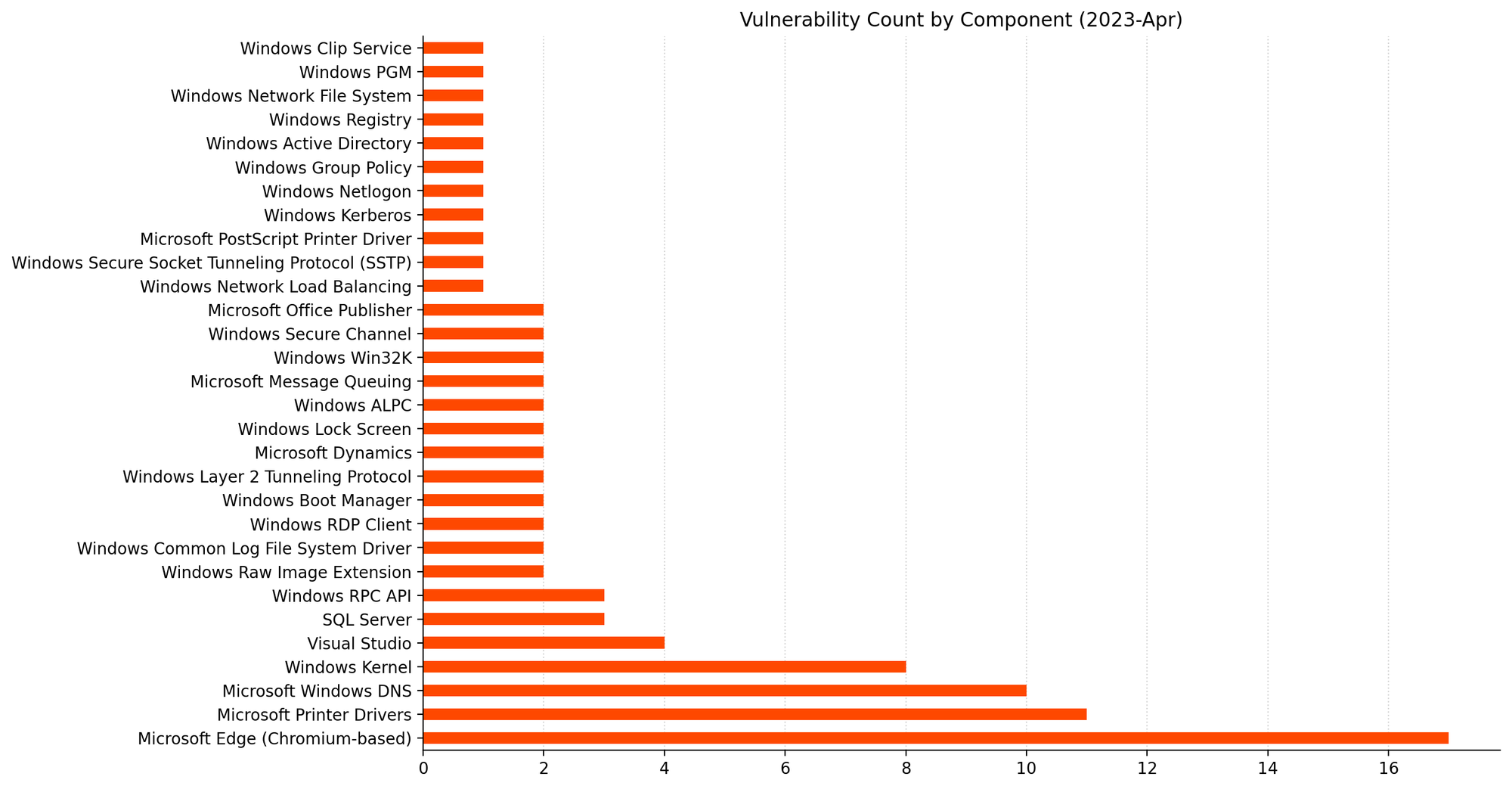
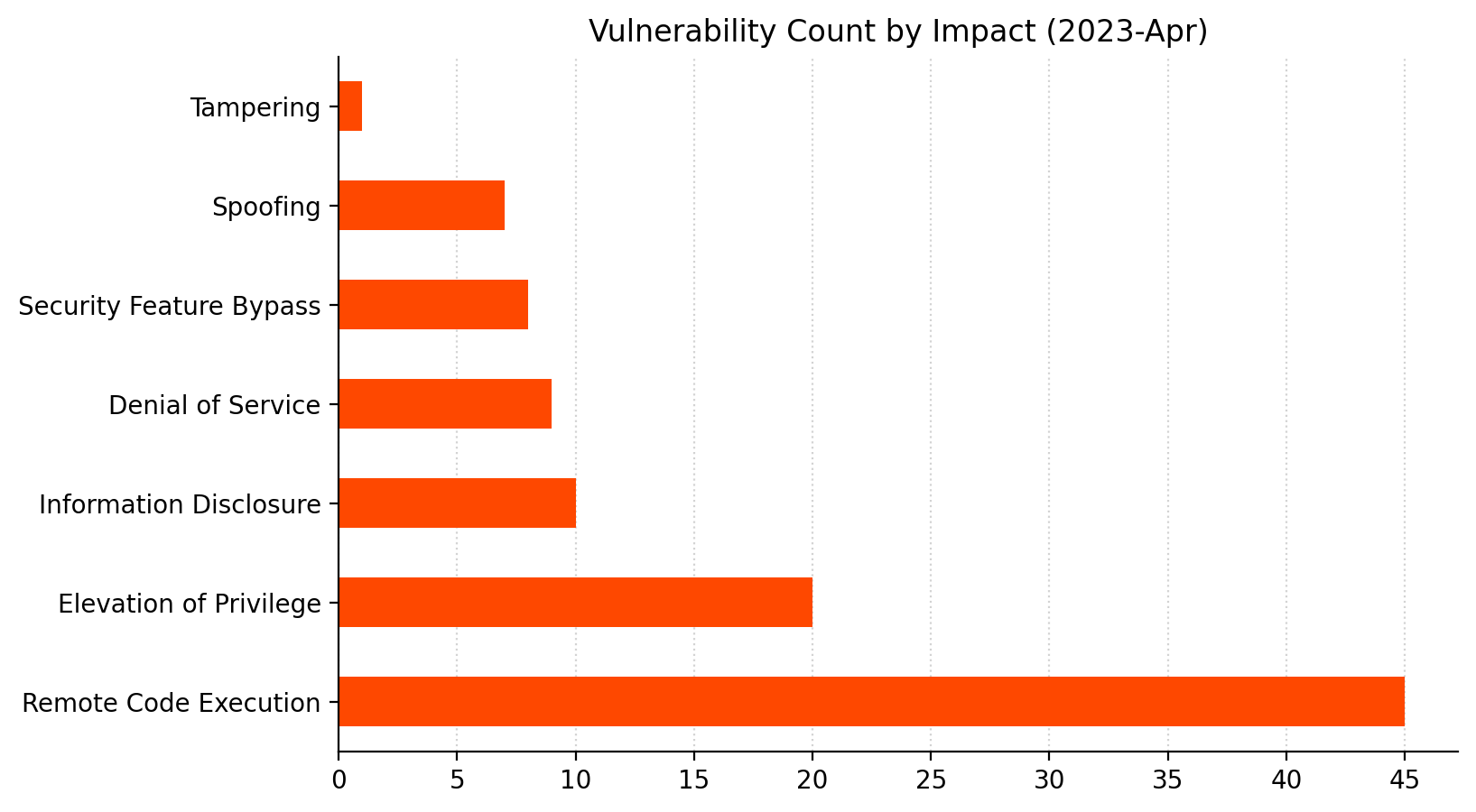
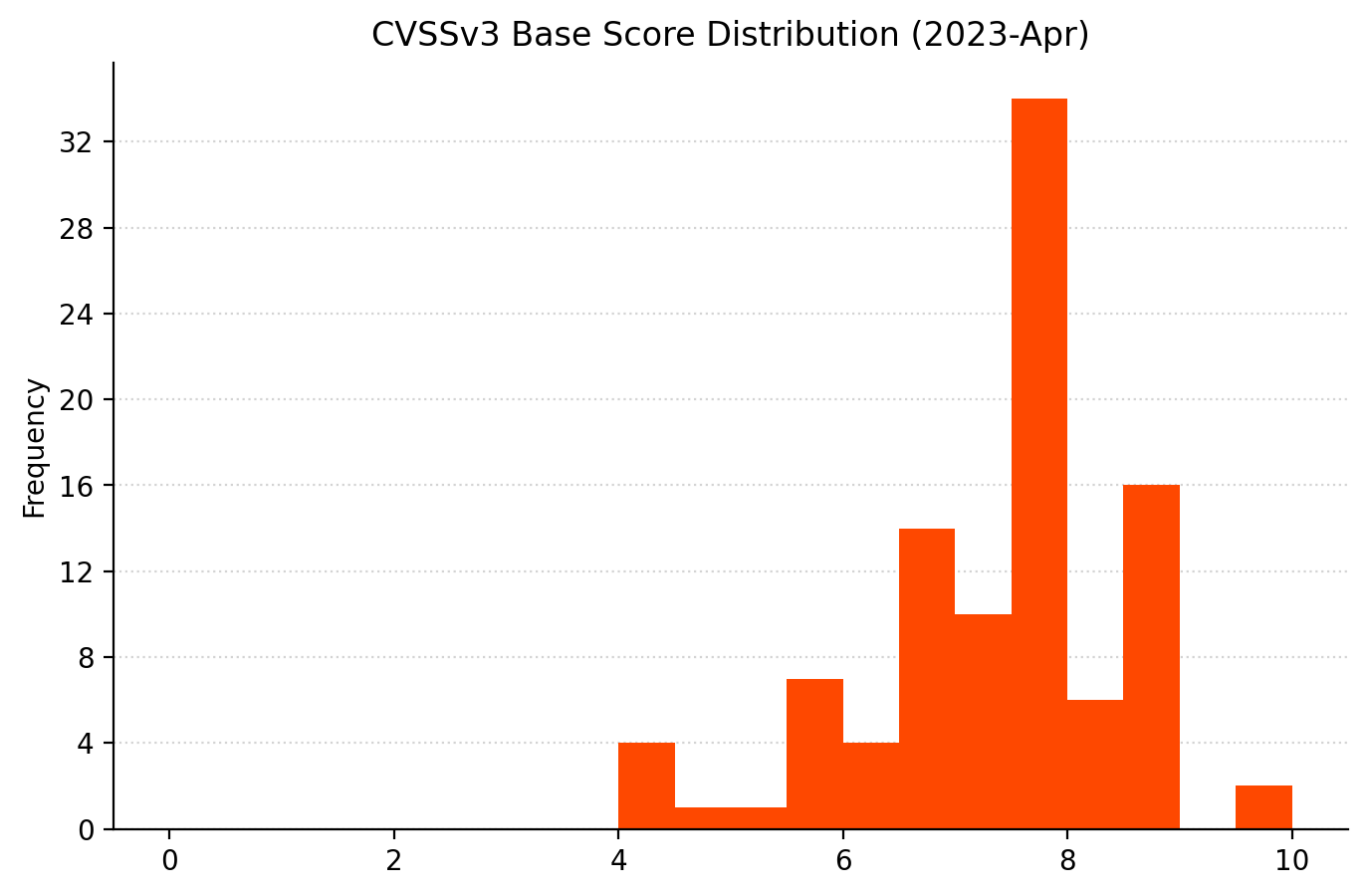
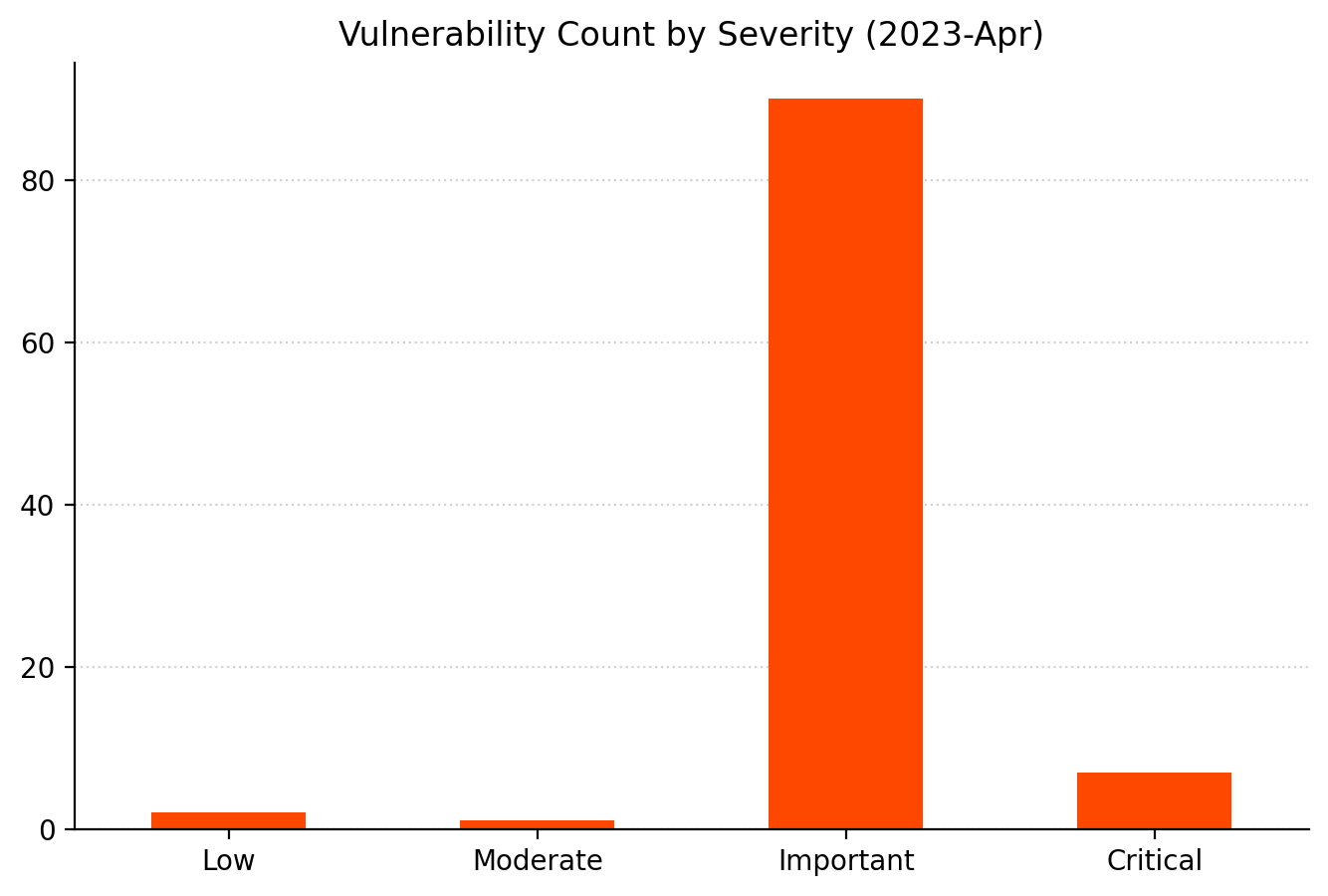
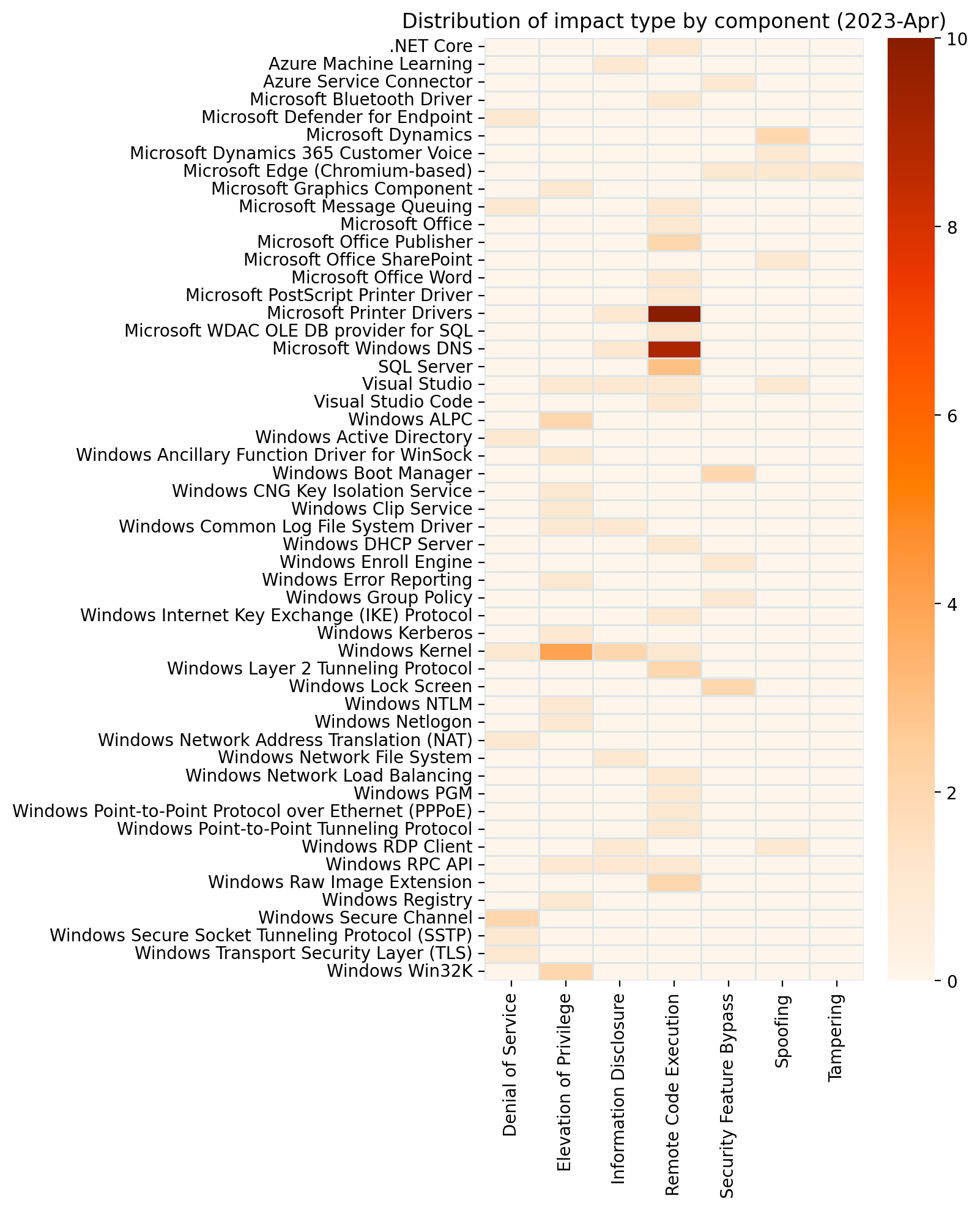
Summary tables
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-28300 | Azure Service Connector Security Feature Bypass Vulnerability | No | No | 7.5 |
| CVE-2023-28312 | Azure Machine Learning Information Disclosure Vulnerability | No | No | 6.5 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-28284 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability | No | No | 4.3 |
| CVE-2023-28301 | Microsoft Edge (Chromium-based) Tampering Vulnerability | No | No | 4.2 |
| CVE-2023-24935 | Microsoft Edge (Chromium-based) Spoofing Vulnerability | No | No | N/A |
| CVE-2023-1823 | Chromium: CVE-2023-1823 Inappropriate implementation in FedCM | No | No | N/A |
| CVE-2023-1822 | Chromium: CVE-2023-1822 Incorrect security UI in Navigation | No | No | N/A |
| CVE-2023-1821 | Chromium: CVE-2023-1821 Inappropriate implementation in WebShare | No | No | N/A |
| CVE-2023-1820 | Chromium: CVE-2023-1820 Heap buffer overflow in Browser History | No | No | N/A |
| CVE-2023-1819 | Chromium: CVE-2023-1819 Out of bounds read in Accessibility | No | No | N/A |
| CVE-2023-1818 | Chromium: CVE-2023-1818 Use after free in Vulkan | No | No | N/A |
| CVE-2023-1817 | Chromium: CVE-2023-1817 Insufficient policy enforcement in Intents | No | No | N/A |
| CVE-2023-1816 | Chromium: CVE-2023-1816 Incorrect security UI in Picture In Picture | No | No | N/A |
| CVE-2023-1815 | Chromium: CVE-2023-1815 Use after free in Networking APIs | No | No | N/A |
| CVE-2023-1814 | Chromium: CVE-2023-1814 Insufficient validation of untrusted input in Safe Browsing | No | No | N/A |
| CVE-2023-1813 | Chromium: CVE-2023-1813 Inappropriate implementation in Extensions | No | No | N/A |
| CVE-2023-1812 | Chromium: CVE-2023-1812 Out of bounds memory access in DOM Bindings | No | No | N/A |
| CVE-2023-1811 | Chromium: CVE-2023-1811 Use after free in Frames | No | No | N/A |
| CVE-2023-1810 | Chromium: CVE-2023-1810 Heap buffer overflow in Visuals | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-28296 | Visual Studio Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2023-28262 | Visual Studio Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-24893 | Visual Studio Code Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28260 | .NET DLL Hijacking Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28299 | Visual Studio Spoofing Vulnerability | No | No | 5.5 |
| CVE-2023-28263 | Visual Studio Information Disclosure Vulnerability | No | No | 5.5 |
ESU SQL Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-23384 | Microsoft SQL Server Remote Code Execution Vulnerability | No | No | 7.3 |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-28250 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-21554 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-28240 | Windows Network Load Balancing Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-21727 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-28275 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-28231 | DHCP Server Service Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-28244 | Windows Kerberos Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2023-28268 | Netlogon RPC Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2023-28219 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-28220 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-28272 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-28293 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-24912 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-28252 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Yes | No | 7.8 |
| CVE-2023-28241 | Windows Secure Socket Tunneling Protocol (SSTP) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-24931 | Windows Secure Channel Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-28232 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2023-28217 | Windows Network Address Translation (NAT) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-28238 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2023-28227 | Windows Bluetooth Driver Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2023-21769 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-28302 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-28254 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-28222 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-28229 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-28218 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-28216 | Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-28305 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28255 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28278 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28256 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28306 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28307 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28308 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28223 | Windows Domain Name Service Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-28267 | Remote Desktop Protocol Client Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-28228 | Windows Spoofing Vulnerability | No | No | 5.5 |
| CVE-2023-28271 | Windows Kernel Memory Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-28253 | Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-28298 | Windows Kernel Denial of Service Vulnerability | No | No | 5.5 |
| CVE-2023-28266 | Windows Common Log File System Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-28276 | Windows Group Policy Security Feature Bypass Vulnerability | No | No | 4.4 |
| CVE-2023-21729 | Remote Procedure Call Runtime Information Disclosure Vulnerability | No | No | 4.3 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-28309 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 7.6 |
| CVE-2023-28313 | Microsoft Dynamics 365 Customer Voice Cross-Site Scripting Vulnerability | No | No | 6.1 |
| CVE-2023-28314 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 6.1 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-28311 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28287 | Microsoft Publisher Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28295 | Microsoft Publisher Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28285 | Microsoft Office Graphics Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28288 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 6.5 |
SQL Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-23375 | Microsoft ODBC and OLE DB Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28304 | Microsoft ODBC and OLE DB Remote Code Execution Vulnerability | No | No | 7.8 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-24860 | Microsoft Defender Denial of Service Vulnerability | No | No | 7.5 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-28297 | Windows Remote Procedure Call Service (RPCSS) Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-24924 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24925 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24884 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24926 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24885 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24927 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24886 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24928 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24887 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24929 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-28243 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-28291 | Raw Image Extension Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2023-28274 | Windows Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-28246 | Windows Registry Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-28225 | Windows NTLM Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-28237 | Windows Kernel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28236 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-28248 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-28292 | Raw Image Extension Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-28233 | Windows Secure Channel Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-28234 | Windows Secure Channel Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-28247 | Windows Network File System Information Disclosure Vulnerability | No | No | 7.5 |
| CVE-2023-28224 | Windows Point-to-Point Protocol over Ethernet (PPPoE) Remote Code Execution Vulnerability | No | No | 7.1 |
| CVE-2023-28221 | Windows Error Reporting Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-28273 | Windows Clip Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-24914 | Win32k Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-28235 | Windows Lock Screen Security Feature Bypass Vulnerability | No | No | 6.8 |
| CVE-2023-28270 | Windows Lock Screen Security Feature Bypass Vulnerability | No | No | 6.8 |
| CVE-2023-24883 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-28269 | Windows Boot Manager Security Feature Bypass Vulnerability | No | No | 6.2 |
| CVE-2023-28249 | Windows Boot Manager Security Feature Bypass Vulnerability | No | No | 6.2 |
| CVE-2023-28226 | Windows Enroll Engine Security Feature Bypass Vulnerability | No | No | 5.3 |
| CVE-2023-28277 | Windows DNS Server Information Disclosure Vulnerability | No | No | 4.9 |

