Rapid7 managed services teams have observed exploitation of Adobe ColdFusion in multiple customer environments. The attacks our team has responded to thus far appear to be chaining CVE-2023-29298, a Rapid7-discovered access control bypass in ColdFusion that was disclosed on July 11, with an additional vulnerability. The behavior our teams are observing appears to be consistent with a zero-day exploit published (and then subsequently taken down) by Project Discovery circa July 12.
Background
On Tuesday, July 11, Adobe released fixes for several vulnerabilities affecting ColdFusion, including a Rapid7-discovered access control bypass vulnerability (CVE-2023-29298) that we disclosed in coordination with the vendor. On July 13, Rapid7 managed services teams began observing exploitation of Adobe ColdFusion in multiple customer environments. Based on available evidence, threat actors appear to be exploiting CVE-2023-29298 in conjunction with a secondary vulnerability. The behavior our teams are observing appears to be consistent with CVE-2023-38203, which was published and then subsequently taken down by Project Discovery circa July 12.
It’s highly likely that Project Discovery thought they were publishing an n-day exploit for CVE-2023-29300 in their July 12 blog post. Adobe published a fix for CVE-2023-29300, which is a deserialization vulnerability that allows for arbitrary code execution, on July 11. In actuality, what Project Discovery had detailed was a new zero-day exploit chain that Adobe fixed in an out-of-band update on July 14.
The patch for CVE-2023-29300 implements a denylist of classes that cannot be deserialized by the Web Distributed Data eXchange (WDDX) data that forms part of some requests to ColdFusion. Adobe is likely unable to remove this WDDX functionality completely, as that would break all the things that rely on it, so instead of prohibiting deserialization of WDDX data, they implement a denylist of Java class paths that cannot be deserialized (so an attacker cannot specify a deserialization gadget located in these class paths).
The Project Discovery authors evidently figured out a gadget that worked (i.e., a class that is not on Adobe’s denylist and can be used as a deserialization gadget to achieve remote code execution) based on the class com.sun.rowset.JdbcRowSetImpl. The Project Discovery team probably did not realize their discovery was a new zero-day vulnerability and (we assume) took down their blog while Adobe fixed the flaw. On Friday July 14, Adobe published an out-of-band patch for CVE-2023-38203 — a new deserialization vulnerability. The only thing this patch does is add the class path !com.sun.rowset.** to the denylist, breaking the exploit Project Discovery had published on July 12.
Incomplete fix for CVE-2023-29298
Rapid7 researchers determined on Monday, July 17 that the fix Adobe provided for CVE-2023-29298 on July 11 is incomplete, and that a trivially modified exploit still works against the latest version of ColdFusion (released July 14). We have notified Adobe that their patch is incomplete. There was no mitigation for CVE-2023-29298 at the time this blog was published, but the exploit chain Rapid7 was observing in the wild relies on a secondary vulnerability for full execution on target systems. Therefore, updating to the latest available version of ColdFusion that fixes CVE-2023-38203 should still prevent the attacker behavior our MDR team is observing.
NOTE: Adobe released a fix for the patch bypass of CVE-2023-29298 on July 19 and assigned it CVE-2023-38205. Rapid7 has confirmed the new patch works.
Affected Products
The following versions of ColdFusion are vulnerable to both CVE-2023-29298 and CVE-2023-38203:
- Adobe ColdFusion 2023 Update 1
- Adobe ColdFusion 2021 Update 7 and below
- Adobe ColdFusion 2018 Update 17 and below
The versions of ColdFusion below contain the July 14 out-of-band patch for CVE-2023-38203 but are still vulnerable to CVE-2023-29298:
- Adobe ColdFusion 2023 Update 2 and earlier
- Adobe ColdFusion 2021 Update 8 and earlier
- Adobe ColdFusion 2018 Update 18 and earlier
The latest fixed versions of ColdFusion as of July 19 are below and should remediate CVE-2023-29298, CVE-2023-38203, and CVE-2023-38205:
- Adobe ColdFusion 2023 Updatae 3
- Adobe ColdFusion 2021 Update 9
- Adobe ColdFusion 2018 Update 19
Observed attacker behavior
Rapid7 has observed POST requests (see example below) in IIS logs that were sent to file accessmanager.cfc in order to leverage this exploit.
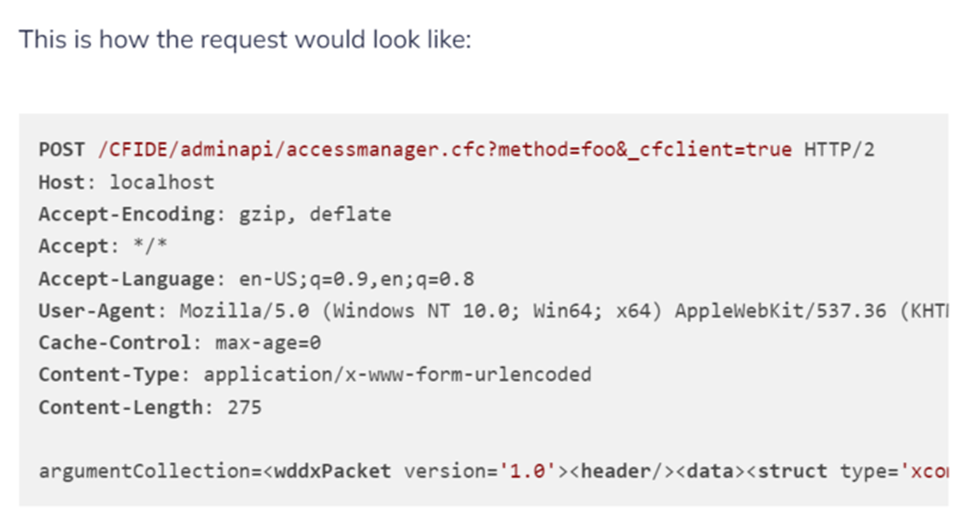
The attackers then executed encoded PowerShell commands on an endpoint in order to create a webshell to gain access to the endpoint. The webshell is typically observed in \wwwroot\CFIDE directory: .\ColdFusion11\cfusion\wwwroot\CFIDE\ckeditr.cfm
Additionally, Rapid7 observed cURL commands to the following Burpsuite URL, along with nltest /domain_trusts related activity in order to query the domain controller. : hXXp://rlgt1hin2gdk2p3teyhuetitrkxblg95.oastify[.]com
IOCs
IP addresses:
62.233.50[.]13
5.182.36[.]4
195.58.48[.]155
Domains:
- oastify[.]com
- ckeditr[.]cfm (SHA256 08D2D815FF070B13A9F3B670B2132989C349623DB2DE154CE43989BB4BBB2FB1)
Mitigation guidance
Adobe ColdFusion customers should immediately update to the latest version of ColdFusion and block domain oastify[.]com. As of July 19, the latest versions of ColdFusion are in APSB23-47 here.
Adobe’s July 14 and July 19 advisories also explicitly note the following, which ColdFusion customers may want to consider implementing in addition to applying the latest updates:
If you become aware of any package with a deserialization vulnerability in the future, use the serialfilter.txt file in <cfhome>/lib to denylist the package (eg: !org.jgroups.**;).
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to CVE-2023-29298 and CVE-2023-38203 with a vulnerability check available in the July 17 content release. Note that the previous vulnerability check for CVE-2023-29298 has been updated to reflect that the fix is incomplete. A vulnerability check for CVE-2023-38205 is in development and expected to be released in the July 20, 2023 content release.
InsightIDR and Managed Detection & Response customers have existing detection coverage through Rapid7's expansive library of detection rules. The following detection rules are deployed and alerting on post-exploitation activity related to this vulnerability:
- Webshell - Possible ColdFusion Webshell In Command Line (deployed: March, 2023)
- Attacker Technique - ColdFusion Spawning curl.exe or wget.exe (deployed: July, 2023)
- Attacker Tool - PowerShell -noni -ep -nop Flags (deployed: August, 2019)
- Attacker Technique - PowerShell Download Cradles (deployed: January, 2019)
- PowerShell - Obfuscated Script (deployed: March, 2018)
- Suspicious Process - Burpsuite Related Domain in Command Line (deployed: October 2020)
Managed Detection & Response customers please note: If the Rapid7 MDR team detects suspicious activity in your environment, your Customer Advisor will reach out to you directly.
Download Rapid7's Annual Vulnerability Intelligence Report ▶︎

