Microsoft is publishing 172 new vulnerabilities today. Microsoft is aware of public disclosure for just two of the vulnerabilities published today, and claims no evidence of in-the-wild exploitation. Today sees six zero-day vulnerabilities patched, but only a single one is evaluated as critical severity. Microsoft is aware of public disclosure in three cases, and exploitation in the wild in the remaining three. Today’s release includes the publication of five further critical remote code execution (RCE) vulnerabilities, although Microsoft expects that only one is likely to see exploitation. 14 browser vulnerabilities and a significant array of fixes for Azure Linux (aka Mariner) have already been published separately this month, and are not included in the total. Alongside older versions of Exchange and Office, the behemoth that is Windows 10 receives its final security patches today, although there are some exceptions.
TPM 2.0: zero-day information disclosure
When the Trusted Computing Group (TCG) consortium’s TPM 2.0 reference implementation contains a flaw, under normal circumstances that flaw is likely to be replicated in the downstream implementation by each manufacturer. That is the case with CVE-2025-2884, an information disclosure vulnerability which Microsoft is treating as a zero day despite the curious circumstance that Microsoft is a founder member of TCG, and thus presumably privy to the discovery before its publication. Windows 11 and newer versions of Windows Server receive patches. In place of patches, admins for older Windows products such as Windows 10 and Server 2019 receive another implicit reminder that Microsoft would strongly prefer that everyone upgrade.
Remote Access Connection Manager: zero-day EoP
Local elevation of privilege (EoP) is always attractive to an attacker, since even if it doesn’t get them where they need to be, it can provide an important link in the chain. Microsoft is already aware of exploitation in the wild for CVE-2025-59230, a vulnerability in the Windows Remote Access Connection Manager. With no user interaction required, this will go straight into an attacker’s standard toolkit. There’s very little information in the advisory itself, but someone out there knows exactly how to exploit this vulnerability. Credit where credit is due: Microsoft detected the exploitation, and now we have patches for all supported versions of Windows.
Agere fax modem driver: pair of zero-day EoP
Are you a doctor, a lawyer, or a hipster? If so, you might be one of the holdouts who still feels the need to connect a fax machine to a computer, and you should brace yourself for some bad news, then some good news, and then some more bad news. For starters, Microsoft has published two zero-day vulnerabilities in the Agere Modem driver: CVE-2025-24052, which is publicly disclosed, and CVE-2025-24990, which has already been exploited in the wild. The vulnerable driver ships with every version of Windows, up to and including Server 2025. Maybe your fax modem uses a different chipset, and so you don’t need the Agere driver? Perhaps you’ve simply discovered email? Tough luck. Your PC is still vulnerable, and a local attacker with a minimally privileged account can elevate to administrator. The good news is that Microsoft is patching both of these vulnerabilities today. The sting in the tail is that they’re fixing the glitch by removing the vulnerable driver altogether, so if you are still using a fax modem with an Agere chipset, no fax for you!
IGEL OS: UEFI zero-day
If you don’t run thin clients targeting Windows environments, you might be unaware of the existence of IGEL OS, but today’s publication of the advisory for CVE-2025-47827 — which is a zero-day vulnerability — may put it on the radar a little more widely. Successful exploitation abuses overly lax cryptographic verification of root filesystem, and allows bypass of Secure Boot. Microsoft is aware of exploitation in the wild, and is offering patches for the usual array of Windows products.
The advisory doesn’t explain what the Windows patches are protecting against when the flaw is in IGEL OS itself. However, the write-up by the original discoverer contains a significant amount of interesting backstory, and we can infer that the Windows patches will include additions to the UEFI revocation list, theoretically rendering a specific asset immune to this attack.
AMD: zero-day information disclosure
Every so often, a processor vulnerability gets some attention. When they are included in a set of Patch Tuesday vulns, processor vulnerabilities tend to march to the beat of their own drummer, since Microsoft likely has very little control over how or when these are announced. AMD published CVE-2025-0033 yesterday, and Microsoft has responded with their own advisory today. The flaw affects only fairly recent AMD EPYC processors, which are more likely to be found in a cloud data centre than they are in a metal box underneath your desk.
This is technically a zero-day vulnerability, since Microsoft is acknowledging that at least some products are affected, and there’s no patch yet. Specifically, Microsoft acknowledges that patches are needed for several variants of Azure Confidential Compute VM, and that they are working towards providing those patches. There isn’t anything much to do here yet from a Windows administration perspective, since AMD’s advisory understandably addresses only the underlying hardware, and Microsoft hasn’t said anything yet about any possible impact on Windows itself.
Windows Server Update Service: critical pre-auth RCE
The Windows Server Update Service (WSUS) provides admins with some very handy features. You can download updates from Microsoft once, and then redistribute them locally. It also allows scheduling of deployments to minimize impact on business activities, as well as centralized monitoring of updates. What’s not to love, right? Answer: CVE-2025-59287, a critical RCE which allows an attacker to execute code remotely. Although Microsoft isn’t currently claiming knowledge of disclosure or exploitation in the wild, they do consider exploitation more likely. Although the advisory doesn’t explicitly mark this one out as a pre-authentication RCE, the CVSS v3 base score of 9.8 tells an alarming story: a network attack vector, no privileges required, and low attack complexity. Patches are available for all versions of Windows Server. Taking all that into account, along with the Acknowledgements section of the advisory, a good time to apply these patches is right meow.
Microsoft lifecycle update
Today marks the end of an era, sort of. As Rapid7 has previously noted, today marks the end of support for non-LTSC versions of Windows 10. Of course, there’s a lot of nuance here. First, let’s address Windows 10 Long Term Support Channel (LTSC) installations, which are Microsoft’s way of providing risk-averse enterprise customers with the same exact OS almost indefinitely. An LTSC installation never has to worry about huge feature updates, but instead receives only security patches.
All versions of Windows 10 LTSC will continue to receive security updates for quite some time, with the exception of Windows 10 Enterprise LTSC 2015, which is now too old even for Microsoft to support. Still, that’s been an extra eight-and-a-half years of security updates vs. the equivalent non-LTSC version of Windows 10. When you’re relying on Windows 10 for the safe operation of an MRI scanner or a critical industrial control system at a steel plant, stability is key. A frank discussion of whether or not Windows is the optimal choice in these scenarios is beyond the scope of this analysis. Regular LTSC runs until 2027, whereas IoT Enterprise LTSC 2021 is scheduled to limp onwards all the way until January 2032.
It’s likely that Microsoft’s Extended Security Update (ESU) offering will be much more widely discussed in the coming weeks than is typical. Via the ESU program, Microsoft offers further security updates for software which has moved past the end of support. It is generally a paid “cash for updates” service, although consumers in the European Union can take advantage of Microsoft’s offer of one free year of ESU for Windows 10 Home or Professional. It may well be a coincidence that Microsoft has extended this generous offer only to consumers in a large jurisdiction with strong consumer rights. Users without spare cash or an EU home address can consider syncing their PC settings to OneDrive — make sure to enable multi-factor authentication on your Microsoft account if you do this — or spending 1000 Microsoft Rewards points, if you know what those are and have some to spare.
Microsoft, of course, has been pushing us all to upgrade to Windows 11 for a long time, but this leaves some people out in the cold. Windows 10 users without the cash to upgrade to Windows 11-compatible PC hardware or the IT situational awareness to realize that they are now at increased risk of compromise will now drift further and further away from a solid security stance. Not for the first time, the most vulnerable users with the fewest resources will end up in the most precarious situation.
Also receiving their final guaranteed patches today: Office 2016 and Office 2019. Another significant change: both Exchange 2016 and Exchange 2019 are now entirely replaced by Exchange Server Subscription Edition. A huge amount of lifecycle change today, and one which Microsoft has been building towards for many years now. The full impact may not become clear for a while, especially the retirement of Windows 10.
Summary charts
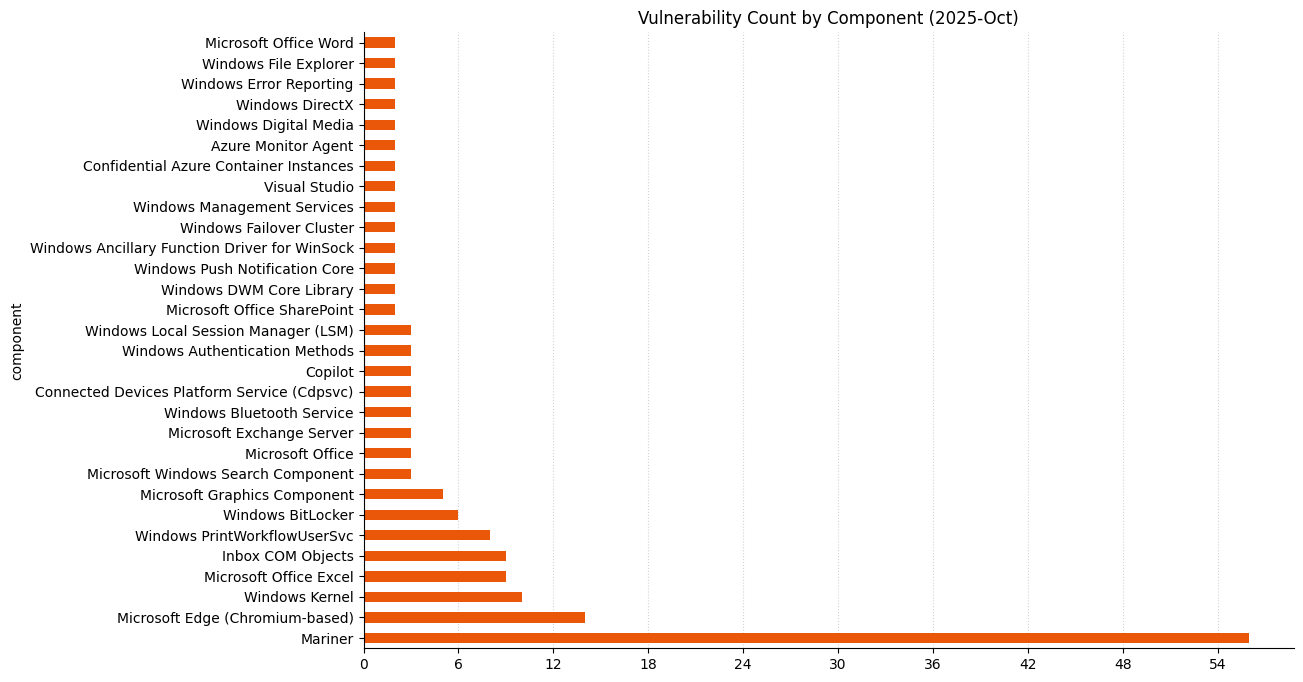
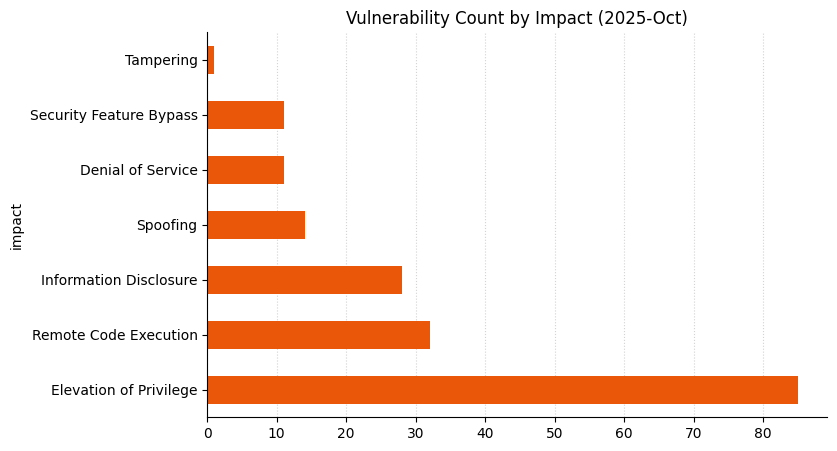
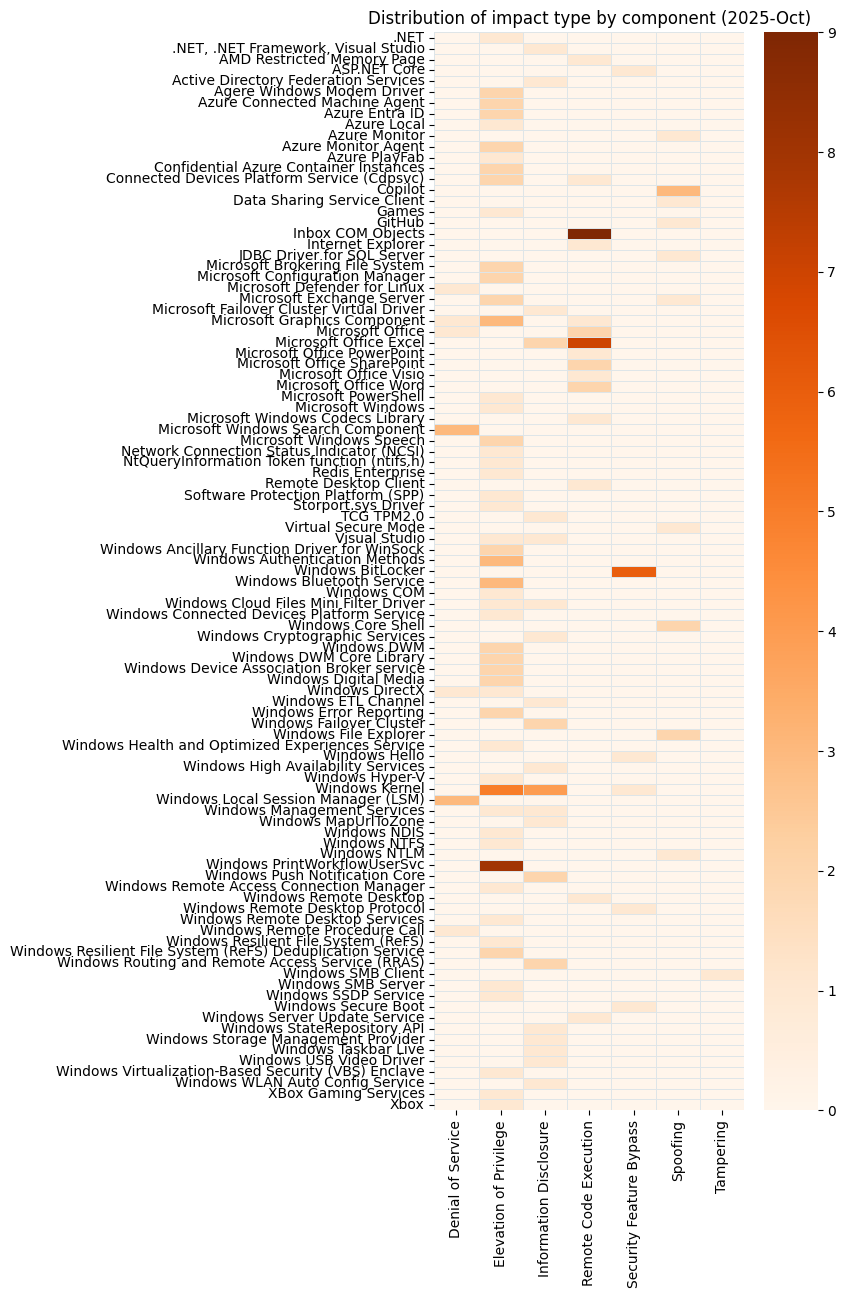
Summary tables
Apps vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
MITRE: CVE-2025-59489 Unity Gaming Engine Editor vulnerability | No | No | 8.4 | |
Xbox Gaming Services Elevation of Privilege Vulnerability | No | No | 7.8 | |
M365 Copilot Spoofing Vulnerability | No | No | 6.5 | |
Copilot Spoofing Vulnerability | No | No | 6.5 | |
Copilot Spoofing Vulnerability | No | No | 6.5 |
Azure vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Azure Entra ID Elevation of Privilege Vulnerability | No | No | 9.8 | |
Azure Entra ID Elevation of Privilege Vulnerability | No | No | 9.6 | |
Azure PlayFab Elevation of Privilege Vulnerability | No | No | 8.8 | |
Redis Enterprise Elevation of Privilege Vulnerability | No | No | 8.7 | |
Azure Monitor Log Analytics Spoofing Vulnerability | No | No | 8.7 | |
Confidential Azure Container Instances Elevation of Privilege Vulnerability | No | No | 8.2 | |
Azure Compute Gallery Elevation of Privilege Vulnerability | No | No | 8.2 | |
AMD CVE-2025-0033: RMP Corruption During SNP Initialization | No | Yes | 8.2 | |
Azure Monitor Agent Elevation of Privilege Vulnerability | No | No | 7.8 | |
Arc Enabled Servers - Azure Connected Machine Agent Elevation of Privilege Vulnerability | No | No | 7.8 | |
Azure Monitor Agent Elevation of Privilege Vulnerability | No | No | 7 | |
Azure Connected Machine Agent Elevation of Privilege Vulnerability | No | No | 7 |
Browser vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Chromium: CVE-2025-11460 Use after free in Storage | No | No | N/A | |
Chromium: CVE-2025-11458 Heap buffer overflow in Sync | No | No | N/A | |
Chromium: CVE-2025-11219 Use after free in V8 | No | No | N/A | |
Chromium: CVE-2025-11216 Inappropriate implementation in Storage | No | No | N/A | |
Chromium: CVE-2025-11215 Off by one error in V8 | No | No | N/A | |
Chromium: CVE-2025-11213 Inappropriate implementation in Omnibox | No | No | N/A | |
Chromium: CVE-2025-11212 Inappropriate implementation in Media | No | No | N/A | |
Chromium: CVE-2025-11211 Out of bounds read in Media | No | No | N/A | |
Chromium: CVE-2025-11210 Side-channel information leakage in Tab | No | No | N/A | |
Chromium: CVE-2025-11209 Inappropriate implementation in Omnibox | No | No | N/A | |
Chromium: CVE-2025-11208 Inappropriate implementation in Media | No | No | N/A | |
Chromium: CVE-2025-11207 Side-channel information leakage in Storage | No | No | N/A | |
Chromium: CVE-2025-11206 Heap buffer overflow in Video | No | No | N/A | |
Chromium: CVE-2025-11205 Heap buffer overflow in WebGPU | No | No | N/A |
Developer Tools vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
ASP.NET Security Feature Bypass Vulnerability | No | No | 9.9 | |
Visual Studio Elevation of Privilege Vulnerability | No | No | 7.3 | |
.NET Elevation of Privilege Vulnerability | No | No | 7.3 | |
.NET, .NET Framework, and Visual Studio Information Disclosure Vulnerability | No | No | 4.8 | |
GitHub CVE-2025-54132: Arbitrary Image Fetch in Mermaid Diagram Tool | No | No | 4.4 |
Developer Tools ESU Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
PowerShell Elevation of Privilege Vulnerability | No | No | 7.3 |
ESU Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Windows Server Update Service (WSUS) Remote Code Execution Vulnerability | No | No | 9.8 | |
Windows URL Parsing Remote Code Execution Vulnerability | No | No | 8.8 | |
Remote Desktop Client Remote Code Execution Vulnerability | No | No | 8.8 | |
Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | Yes | No | 7.8 | |
Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Error Reporting Service Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Authentication Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Authentication Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Authentication Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Authentication Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Agere Modem Driver Elevation of Privilege Vulnerability | No | Yes | 7.8 | |
Windows Agere Modem Driver Elevation of Privilege Vulnerability | Yes | No | 7.8 | |
Network Connection Status Indicator (NCSI) Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows SMB Server Elevation of Privilege Vulnerability | No | No | 7.5 | |
Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability | No | No | 7.4 | |
Windows NTFS Elevation of Privilege Vulnerability | No | No | 7.4 | |
Windows MapUrlToZone Information Disclosure Vulnerability | No | No | 7.1 | |
Windows Simple Search and Discovery Protocol (SSDP) Service Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Remote Desktop Services Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7 | |
Windows COM+ Event System Service Elevation of Privilege Vulnerability | No | No | 7 | |
Remote Desktop Protocol Remote Code Execution Vulnerability | No | No | 7 | |
Internet Information Services (IIS) Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
DirectX Graphics Kernel Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 | |
Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 | |
Windows Local Session Manager (LSM) Denial of Service Vulnerability | No | No | 6.5 | |
Windows Local Session Manager (LSM) Denial of Service Vulnerability | No | No | 6.5 | |
NTLM Hash Disclosure Spoofing Vulnerability | No | No | 6.5 | |
NTLM Hash Disclosure Spoofing Vulnerability | No | No | 6.5 | |
Microsoft Windows File Explorer Spoofing Vulnerability | No | No | 6.5 | |
Microsoft Windows File Explorer Spoofing Vulnerability | No | No | 6.5 | |
Windows Active Directory Federation Services (ADFS) Information Disclosure Vulnerability | No | No | 6.2 | |
Windows WLAN AutoConfig Service Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Search Service Denial of Service Vulnerability | No | No | 5.5 | |
Windows Search Service Denial of Service Vulnerability | No | No | 5.5 | |
Windows Push Notification Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Push Notification Information Disclosure Vulnerability | No | No | 5.5 | |
Microsoft Failover Cluster Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Search Service Denial of Service Vulnerability | No | No | 5 | |
MITRE CVE-2025-47827: Secure Boot bypass in IGEL OS before 11 | Yes | No | 4.6 | |
MITRE CVE-2016-9535: LibTIFF Heap Buffer Overflow Vulnerability | No | No | 4 | |
Windows SMB Client Tampering Vulnerability | No | No | 3.1 |
Mariner Open Source Software vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Redis Lua Use-After-Free may lead to remote code execution | No | No | 9.9 | |
Use-after-free vulnerability in Qt SVG qsvghandler.cpp allows denial of service via crafted SVG | No | No | 9.3 | |
Qemu-kvm: vnc websocket handshake use-after-free | No | No | 7.5 | |
Lua library commands may lead to integer overflow and potential RCE | No | No | 7 | |
Redis is vulnerable to DoS via specially crafted LUA scripts | No | No | 6.3 | |
Redis: Authenticated users can execute LUA scripts as a different user | No | No | 6 | |
ssh in OpenSSH before 10.1 allows the '\0' character in an ssh:// URI, potentially leading to code execution when a ProxyCommand is used. | No | No | 4.5 | |
ZIP64 End of Central Directory (EOCD) Locator record offset not checked | No | No | 4.3 | |
ssh in OpenSSH before 10.1 allows control characters in usernames that originate from certain possibly untrusted sources, potentially leading to code execution when a ProxyCommand is used. The untrusted sources are the command line and %-sequence expansion of a configuration file. (A configuration file that provides a complete literal username is not categorized as an untrusted source.) | No | No | 3.6 | |
GNU Binutils Linker elflink.c get_link_hash_entry out-of-bounds | No | No | 3.3 | |
GNU Binutils Linker elflink.c elf_link_add_object_symbols out-of-bounds | No | No | 3.3 | |
GNU Binutils Linker elflink.c bfd_elf_gc_record_vtentry out-of-bounds | No | No | 3.3 | |
GNU Binutils Linker elf64-x86-64.c elf_x86_64_relocate_section heap-based overflow | No | No | 3.3 | |
Uncontrolled recursion in Qt SVG module | No | No | N/A |
Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Microsoft SharePoint Remote Code Execution Vulnerability | No | No | 8.8 | |
Microsoft SharePoint Remote Code Execution Vulnerability | No | No | 8.8 | |
Microsoft Excel Remote Code Execution Vulnerability | No | No | 8.4 | |
Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft PowerPoint Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Office Visio Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | |
Microsoft Excel Information Disclosure Vulnerability | No | No | 7.1 | |
Microsoft Excel Information Disclosure Vulnerability | No | No | 7.1 | |
Microsoft Word Remote Code Execution Vulnerability | No | No | 7 | |
Microsoft Office Denial of Service Vulnerability | No | No | 5.5 |
Open Source Software vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
mtd: rawnand: stm32_fmc2: avoid overlapping mappings on ECC buffer | No | No | 9.8 | |
mm/vmalloc, mm/kasan: respect gfp mask in kasan_populate_vmalloc() | No | No | 9.8 | |
ksmbd: smbdirect: validate data_offset and data_length field of smb_direct_data_transfer | No | No | 9.8 | |
e1000e: fix heap overflow in e1000_set_eeprom | No | No | 9.8 | |
can: j1939: implement NETDEV_UNREGISTER notification handler | No | No | 9.8 | |
wifi: wilc1000: avoid buffer overflow in WID string configuration | No | No | 7.8 | |
octeontx2-pf: Fix use-after-free bugs in otx2_sync_tstamp() | No | No | 7.8 | |
cnic: Fix use-after-free bugs in cnic_delete_task | No | No | 7.8 | |
tcp: Clear tcp_sk(sk)->fastopen_rsk in tcp_disconnect(). | No | No | 7.1 | |
net: phylink: add lock for serializing concurrent pl->phydev writes with resolver | No | No | 7.1 | |
i40e: remove read access to debugfs files | No | No | 7.1 | |
af_unix: Fix null-ptr-deref in unix_stream_sendpage(). | No | No | 7.1 | |
tcp_bpf: Call sk_msg_free() when tcp_bpf_send_verdict() fails to allocate psock->cork. | No | No | 6.6 | |
um: virtio_uml: Fix use-after-free after put_device in probe | No | No | 6.1 | |
dm-stripe: fix a possible integer overflow | No | No | 6.1 | |
iommu/amd/pgtbl: Fix possible race while increase page table level | No | No | 5.8 | |
Elasticsearch Insertion of sensitive information in log file | No | No | 5.7 | |
wifi: mwifiex: Initialize the chan_stats array to zero | No | No | 5.5 | |
tracing: Silence warning when chunk allocation fails in trace_pid_write | No | No | 5.5 | |
tls: make sure to abort the stream if headers are bogus | No | No | 5.5 | |
smb: client: let smbd_destroy() call disable_work_sync(&info->post_send_credits_work) | No | No | 5.5 | |
smb: client: let recv_done verify data_offset, data_length and remaining_data_length | No | No | 5.5 | |
smb: client: fix smbdirect_recv_io leak in smbd_negotiate() error path | No | No | 5.5 | |
sched: Fix sched_numa_find_nth_cpu() if mask offline | No | No | 5.5 | |
qed: Don't collect too many protection override GRC elements | No | No | 5.5 | |
pcmcia: Add error handling for add_interval() in do_validate_mem() | No | No | 5.5 | |
net: rfkill: gpio: Fix crash due to dereferencering uninitialized pointer | No | No | 5.5 | |
net/mlx5e: Harden uplink netdev access against device unbind | No | No | 5.5 | |
mm: /proc/pid/smaps_rollup: fix no vma's null-deref | No | No | 5.5 | |
mm/slub: avoid accessing metadata when pointer is invalid in object_err() | No | No | 5.5 | |
mm/damon/reclaim: avoid divide-by-zero in damon_reclaim_apply_parameters() | No | No | 5.5 | |
mm/damon/lru_sort: avoid divide-by-zero in damon_lru_sort_apply_parameters() | No | No | 5.5 | |
ksmbd: smbdirect: verify remaining_data_length respects max_fragmented_recv_size | No | No | 5.5 | |
drm: bridge: anx7625: Fix NULL pointer dereference with early IRQ | No | No | 5.5 | |
dmaengine: qcom: bam_dma: Fix DT error handling for num-channels/ees | No | No | 5.5 | |
crypto: af_alg - Set merge to zero early in af_alg_sendmsg | No | No | 5.5 | |
cgroup: split cgroup_destroy_wq into 3 workqueues | No | No | 5.5 | |
ASoC: qcom: q6apm-lpass-dais: Fix NULL pointer dereference if source graph failed | No | No | 5.5 | |
Playwright Spoofing Vulnerability | No | No | 5.3 | |
ceph: fix race condition validating r_parent before applying state | No | No | 4.7 | |
wifi: mac80211: increase scan_ies_len for S1G | No | No | 4 | |
iommu/s390: Make attach succeed when the device was surprise removed | No | No | 4 | |
i40e: fix IRQ freeing in i40e_vsi_request_irq_msix error path | No | No | 3.3 |
SQL Server vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
JDBC Driver for SQL Server Spoofing Vulnerability | No | No | 8.1 |
Server Software vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Microsoft Exchange Server Elevation of Privilege Vulnerability | No | No | 8.8 | |
Microsoft Exchange Server Elevation of Privilege Vulnerability | No | No | 8.4 | |
Microsoft Exchange Server Spoofing Vulnerability | No | No | 7.5 |
System Center vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Configuration Manager Elevation of Privilege Vulnerability | No | No | 8.4 | |
Microsoft Defender for Linux Denial of Service Vulnerability | No | No | 7 | |
Configuration Manager Elevation of Privilege Vulnerability | No | No | 6.7 |
Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
Microsoft Graphics Component Elevation of Privilege Vulnerability | No | No | 9.9 | |
Windows Speech Runtime Elevation of Privilege Vulnerability | No | No | 8.8 | |
Windows Speech Runtime Elevation of Privilege Vulnerability | No | No | 8.8 | |
Xbox IStorageService Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Network Driver Interface Specification Driver Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Health and Optimized Experiences Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Error Reporting Service Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Digital Media Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Digital Media Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Device Association Broker Service Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Cryptographic Services Information Disclosure Vulnerability | No | No | 7.8 | |
Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Bluetooth Service Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Bluetooth Service Elevation of Privilege Vulnerability | No | No | 7.8 | |
Storport.sys Driver Elevation of Privilege Vulnerability | No | No | 7.8 | |
Software Protection Platform (SPP) Elevation of Privilege Vulnerability | No | No | 7.8 | |
NtQueryInformation Token function (ntifs.h) Elevation of Privilege Vulnerability | No | No | 7.8 | |
Microsoft DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 | |
Microsoft DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 | |
Azure Local Elevation of Privilege Vulnerability | No | No | 7.8 | |
Windows Hello Security Feature Bypass Vulnerability | No | No | 7.7 | |
DirectX Graphics Kernel Denial of Service Vulnerability | No | No | 7.7 | |
Data Sharing Service Spoofing Vulnerability | No | No | 7.7 | |
Windows Connected Devices Platform Service (Cdpsvc) Remote Code Execution Vulnerability | No | No | 7.5 | |
Remote Procedure Call Denial of Service Vulnerability | No | No | 7.5 | |
Windows Resilient File System (ReFS) Deduplication Service Elevation of Privilege Vulnerability | No | No | 7.4 | |
Windows Resilient File System (ReFS) Deduplication Service Elevation of Privilege Vulnerability | No | No | 7.4 | |
Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.4 | |
Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7.4 | |
Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7.4 | |
Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Remote Desktop Protocol Security Feature Bypass | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Management Services Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Kernel Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Device Association Broker Service Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Bluetooth Service Elevation of Privilege Vulnerability | No | No | 7 | |
Microsoft Graphics Component Denial of Service Vulnerability | No | No | 7 | |
MITRE CVE-2025-54957: Integer overflow in Dolby Digital Plus audio decoder | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | No | No | 7 | |
Desktop Windows Manager Elevation of Privilege Vulnerability | No | No | 7 | |
Windows Local Session Manager (LSM) Denial of Service Vulnerability | No | No | 6.5 | |
Virtual Secure Mode Spoofing Vulnerability | No | No | 6.3 | |
Windows Kernel Security Feature Bypass Vulnerability | No | No | 6.2 | |
Windows BitLocker Security Feature Bypass Vulnerability | No | No | 6.1 | |
Windows BitLocker Security Feature Bypass Vulnerability | No | No | 6.1 | |
Windows BitLocker Security Feature Bypass Vulnerability | No | No | 6.1 | |
Windows BitLocker Security Feature Bypass Vulnerability | No | No | 6.1 | |
Windows BitLocker Security Feature Bypass Vulnerability | No | No | 6.1 | |
Windows BitLocker Security Feature Bypass Vulnerability | No | No | 6.1 | |
Windows USB Video Class System Driver Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Storage Management Provider Information Disclosure Vulnerability | No | No | 5.5 | |
Windows State Repository API Server File Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Management Services Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 | |
Windows ETL Channel Information Disclosure Vulnerability | No | No | 5.5 | |
Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability | No | No | 5.5 | |
Storage Spaces Direct Information Disclosure Vulnerability | No | No | 5.5 | |
Microsoft Failover Cluster Virtual Driver Information Disclosure Vulnerability | No | No | 5.5 | |
Microsoft Failover Cluster Information Disclosure Vulnerability | No | No | 5.5 | |
Cert CC: CVE-2025-2884 Out-of-Bounds read vulnerability in TCG TPM2.0 reference implementation | No | Yes | 5.3 | |
Windows Kernel Information Disclosure Vulnerability | No | No | 5.1 | |
Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | No | No | 4.7 | |
Windows NTLM Spoofing Vulnerability | No | No | 3.3 | |
Windows Taskbar Live Preview Information Disclosure Vulnerability | No | No | 2.1 |
Update history
- 2025-10-20: added Summary Tables.

