Microsoft is addressing 176 vulnerabilities today, which seems like a lot, and it is. Curiously, Microsoft’s own Security Update Guide (SUG) for September 2025 Patch Tuesday only lists 86 vulns, and that’s because the SUG doesn’t include a large number of open source software (OSS) fixes published today as part of updates for Azure Linux/CBL-Mariner. Microsoft is aware of public disclosure for just two of the vulnerabilities published today, and claims no evidence of in-the-wild exploitation. Yet again, there are zero-day vulnerabilities patched, but none of them evaluate as critical severity. Today’s release includes the publication of five critical remote code execution (RCE) vulnerabilities, although Microsoft expects that none of these are particularly likely to see exploitation. Five browser vulnerabilities have already been published separately this month, and are not included in the total.
SQL Server: zero-day DoS
What happens if you ask SQL Server to deserialize a JSON object with thousands of levels of nested objects? If you guessed denial of service, then you are good at guessing, because that’s what CVE-2024-21907 describes. As zero-day vulnerabilities go, it doesn’t seem particularly terrifying, since presumably the worst an attacker can do is knock down a service, which can then be picked up again. Of course, that’s all relative, since some SQL Server instances are doing very important work: think hospitals, airports, and other critical infrastructure. Taking a step back: if an unauthenticated attacker can send arbitrary queries directly into your SQL Server instances, then that’s already a broader security architecture issue.
Perhaps the most interesting thing about CVE-2024-21907 is its long and convoluted history. The underlying defect is not in SQL Server, but in Newtonsoft.Json, which is the de facto standard for handling JSON in .NET applications, including SQL Server and many other products. Versions of Newtonsoft.Json prior to 13.0.1 are vulnerable, and this isn’t new information; CVE-2024-21907 was originally made public on 2024-01-03 with some help from VulnCheck, so Microsoft is playing catch-up here. The underlying defect has been public knowledge for way longer than that, however, since Aleph Security first flagged it up way back in 2018 without attaching a CVE number. It remains unclear why Microsoft chose to address this now, but better late than never.
SMB server: zero-day(?) EoP
How’s your SMB server configuration? Is it fully hardened, with SMB server signing and Extended Protection for Authentication enabled? If not, then CVE-2025-55234 set out clearly why you should be worrying about SMB Server relay attacks, where an attacker pretends to be a legitimate server using ARP spoofing, DNS poisoning, or some other suitable trickery. Any pen testers or threat actors reading this will no doubt be thinking of the popular OSS tool Responder, which streamlines exactly this sort of attack. Options for attackers include credential relaying (which is mitigated by SMB signing), as well as offline cracking of the hash to reveal the password.
The key takeaway from the CVE-2025-55234 advisory, other than the explanation of the well-known attack surface around SMB authentication, is that this is one of those times where simply patching isn’t enough; in fact, the patches provide administrators with more auditing options to determine whether their SMB Server is interacting with clients that won’t support the recommended hardening options. Other Microsoft server products (e.g. Exchange) offer a similar tough choice: lock out less capable clients, or leave your server in a state which permits relay attacks. None of the attack techniques covered are new, so this isn’t really a zero-day vulnerability, except inasmuch as it was published today, and describes an attack which is already publicly disclosed.
Azure Networking: critical EoP
It’s not every day that we see a perfect(?) 10.0 CVSS v3 base score, but CVE-2025-54914 is one such rare beast, thanks to the seldom-seen scope change described by the CVSS v3 vector. However, that’s all we get; the aggressively minimalist advisory fails to explain the nature of the vulnerability in any way at all. Mercifully, the advisory does pour a little oil on its own troubled waters by clarifying that this is a cloud service vulnerability, Microsoft has already fixed it, and there is no action to be taken by users of the service. Other reasons to consider not panicking: the Acknowledgements section lists only Microsoft researchers, so we can hope that no one else knows enough to do any damage. For anyone wondering which cloud service was impacted, the answer is Azure Networking, which is probably only important if your cloud assets ever need to communicate with anything at all.
Azure HPC: critical RCE
Azure High Performance Computer (HPC) admins should pay close attention to CVE-2025-55232, a critical unauthenticated RCE exploitable over the network. The advisory sets out the pre-requisites for the actual patch, and also hints that appropriate firewall rules should be in place, especially for TCP port 5999. The advisory doesn’t describe exactly what those firewall rules should look like or what they’re protecting, but port 5999 is the default port for the HpcScheduler, which orchestrates HPC jobs, resource management, and cluster communication.
Microsoft lifecycle update
There are no significant changes to Microsoft product lifecycles this month. A few Azure services move into retirement towards the end of September: Azure Basic Load Balancer, Azure Database for MariaDB, Azure HPC Cache, Azure Remote Rendering, Azure Service Map, Azure SQL Edge, Azure Unmanaged Disks, and Azure vFXT. As Rapid7 noted previously, there will be a number of significant changes in October, including the categorical end of support for non-LTSC versions of Windows 10.
Summary charts
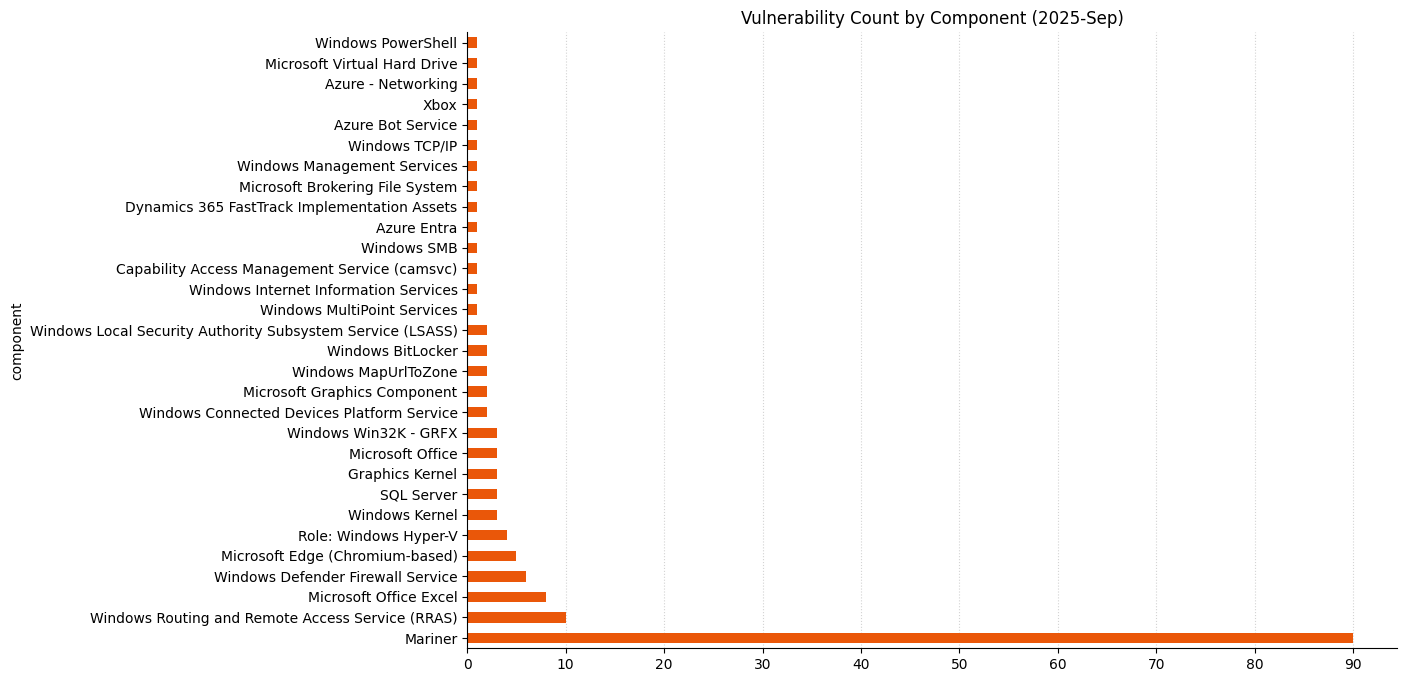
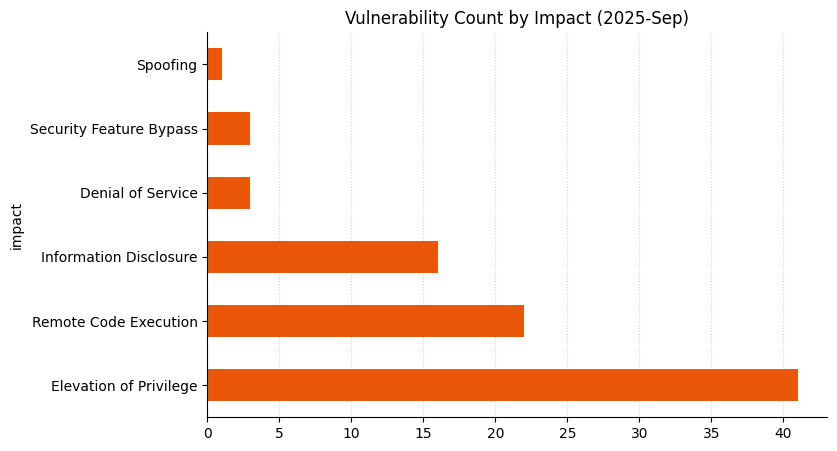
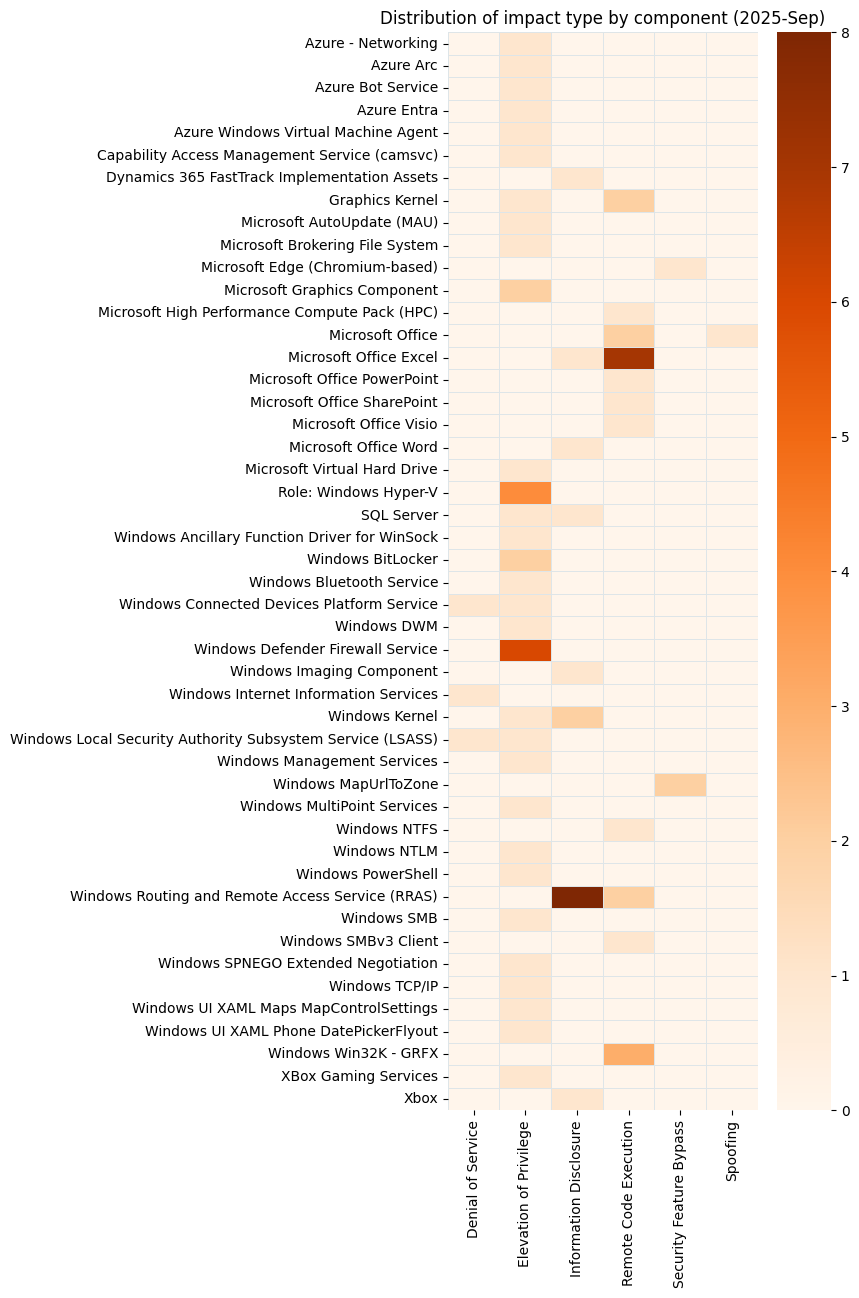
Update history
- 2025-09-10: corrected link to Microsoft Security Update Guide and a small typo in a product name.
Summary tables
Apps vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-55245 | Xbox Gaming Services Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-55242 | Xbox Certification Bug Copilot Djando Information Disclosure Vulnerability | No | No | 6.5 |
Azure vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-54914 | Azure Networking Elevation of Privilege Vulnerability | No | No | 10 |
| CVE-2025-55232 | Microsoft High Performance Compute (HPC) Pack Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2025-55241 | Azure Entra Elevation of Privilege Vulnerability | No | No | 9 |
| CVE-2025-55244 | Azure Bot Service Elevation of Privilege Vulnerability | No | No | 9 |
| CVE-2025-49692 | Azure Connected Machine Agent Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-55316 | Azure Arc Elevation of Privilege Vulnerability | No | No | 7.8 |
Browser vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53791 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability | No | No | 4.7 |
| CVE-2025-9867 | Chromium: CVE-2025-9867 Inappropriate implementation in Downloads | No | No | N/A |
| CVE-2025-9866 | Chromium: CVE-2025-9866 Inappropriate implementation in Extensions | No | No | N/A |
| CVE-2025-9865 | Chromium: CVE-2025-9865 Inappropriate implementation in Toolbar | No | No | N/A |
| CVE-2025-9864 | Chromium: CVE-2025-9864 Use after free in V8 | No | No | N/A |
ESU Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-55234 | Windows SMB Elevation of Privilege Vulnerability | No | Yes | 8.8 |
| CVE-2025-54106 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-54113 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-54918 | Windows NTLM Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-54110 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-54916 | Windows NTFS Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54091 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54098 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54912 | Windows BitLocker Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54895 | SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54894 | Local Security Authority Subsystem Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54911 | Windows BitLocker Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2025-54093 | Windows TCP/IP Driver Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-54099 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53808 | Windows Defender Firewall Service Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2025-53810 | Windows Defender Firewall Service Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2025-54094 | Windows Defender Firewall Service Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2025-54104 | Windows Defender Firewall Service Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2025-54109 | Windows Defender Firewall Service Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2025-54915 | Windows Defender Firewall Service Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2025-55226 | Graphics Kernel Remote Code Execution Vulnerability | No | No | 6.7 |
| CVE-2025-53797 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-53798 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-54095 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-54096 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-54097 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-55225 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-53796 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-53806 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-53804 | Windows Kernel-Mode Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-53803 | Windows Kernel Memory Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-54101 | Windows SMB Client Remote Code Execution Vulnerability | No | No | 4.8 |
| CVE-2025-54107 | MapUrlToZone Security Feature Bypass Vulnerability | No | No | 4.3 |
| CVE-2025-54917 | MapUrlToZone Security Feature Bypass Vulnerability | No | No | 4.3 |
ESU Windows Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53799 | Windows Imaging Component Information Disclosure Vulnerability | No | No | 5.5 |
Mariner vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-57052 | cJSON 1.5.0 through 1.7.18 allows out-of-bounds access via the decode_array_index_from_pointer function in cJSON_Utils.c, allowing remote attackers to bypass array bounds checking and access restricted data via malformed JSON pointer strings containing alphanumeric characters. | No | No | 9.8 |
| CVE-2025-9566 | Podman: podman kube play command may overwrite host files | No | No | 8.1 |
Microsoft Dynamics vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-55238 | Dynamics 365 FastTrack Implementation Assets Information Disclosure Vulnerability | No | No | 7.5 |
Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-54897 | Microsoft SharePoint Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-54910 | Microsoft Office Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-54908 | Microsoft PowerPoint Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54907 | Microsoft Office Visio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54906 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54896 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54898 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54899 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54902 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54903 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54904 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54900 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-55317 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-55243 | Microsoft OfficePlus Spoofing Vulnerability | No | No | 7.5 |
| CVE-2025-54905 | Microsoft Word Information Disclosure Vulnerability | No | No | 7.1 |
| CVE-2025-54901 | Microsoft Excel Information Disclosure Vulnerability | No | No | 5.5 |
Open Source Software vulnerabilities
At time of writing, Microsoft has published patches for these OSS vulnerabilities, but without providing an accompanying advisory for most of them.
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-38714 | hfsplus: fix slab-out-of-bounds in hfsplus_bnode_read() | No | No | 9 |
| CVE-2025-38699 | scsi: bfa: Double-free fix | No | No | 7.8 |
| CVE-2025-38702 | fbdev: fix potential buffer overflow in do_register_framebuffer() | No | No | 7.8 |
| CVE-2025-38685 | fbdev: Fix vmalloc out-of-bounds write in fast_imageblit | No | No | 7.8 |
| CVE-2025-38703 | drm/xe: Make dma-fences compliant with the safe access rules | No | No | 7.8 |
| CVE-2025-39730 | NFS: Fix filehandle bounds checking in nfs_fh_to_dentry() | No | No | 7.5 |
| CVE-2025-39683 | tracing: Limit access to parser->buffer when trace_get_user failed | No | No | 7.1 |
| CVE-2025-38697 | jfs: upper bound check of tree index in dbAllocAG | No | No | 7.1 |
| CVE-2025-38698 | jfs: Regular file corruption check | No | No | 7.1 |
| CVE-2025-39702 | ipv6: sr: Fix MAC comparison to be constant-time | No | No | 7.1 |
| CVE-2025-38688 | iommufd: Prevent ALIGN() overflow | No | No | 7.1 |
| CVE-2025-39689 | ftrace: Also allocate and copy hash for reading of filter files | No | No | 7.1 |
| CVE-2025-39691 | fs/buffer: fix use-after-free when call bh_read() helper | No | No | 7.1 |
| CVE-2025-39732 | wifi: ath11k: fix sleeping-in-atomic in ath11k_mac_op_set_bitrate_mask() | No | No | 7 |
| CVE-2025-38718 | sctp: linearize cloned gso packets in sctp_rcv | No | No | 7 |
| CVE-2025-38695 | scsi: lpfc: Check for hdwq null ptr when cleaning up lpfc_vport structure | No | No | 7 |
| CVE-2025-39694 | s390/sclp: Fix SCCB present check | No | No | 7 |
| CVE-2025-39673 | ppp: fix race conditions in ppp_fill_forward_path | No | No | 7 |
| CVE-2025-38732 | netfilter: nf_reject: don't leak dst refcount for loopback packets | No | No | 7 |
| CVE-2025-38684 | net/sched: ets: use old 'nbands' while purging unused classes | No | No | 7 |
| CVE-2025-39677 | net/sched: Fix backlog accounting in qdisc_dequeue_internal | No | No | 7 |
| CVE-2025-39703 | net, hsr: reject HSR frame if skb can't hold tag | No | No | 7 |
| CVE-2025-39713 | media: rainshadow-cec: fix TOCTOU race condition in rain_interrupt() | No | No | 7 |
| CVE-2025-39711 | media: ivsc: Fix crash at shutdown due to missing mei_cldev_disable() calls | No | No | 7 |
| CVE-2025-38709 | loop: Avoid updating block size under exclusive owner | No | No | 7 |
| CVE-2025-38735 | gve: prevent ethtool ops after shutdown | No | No | 7 |
| CVE-2025-38710 | gfs2: Validate i_depth for exhash directories | No | No | 7 |
| CVE-2025-38701 | ext4: do not BUG when INLINE_DATA_FL lacks system.data xattr | No | No | 7 |
| CVE-2025-38692 | exfat: add cluster chain loop check for dir | No | No | 7 |
| CVE-2025-39721 | crypto: qat - flush misc workqueue during device shutdown | No | No | 7 |
| CVE-2025-38729 | ALSA: usb-audio: Validate UAC3 power domain descriptors, too | No | No | 7 |
| CVE-2025-38724 | nfsd: handle get_client_locked() failure in nfsd4_setclientid_confirm() | No | No | 6.8 |
| CVE-2025-39682 | tls: fix handling of zero-length records on the rx_list | No | No | 6.5 |
| CVE-2025-38708 | drbd: add missing kref_get in handle_write_conflicts | No | No | 6.3 |
| CVE-2025-38713 | hfsplus: fix slab-out-of-bounds read in hfsplus_uni2asc() | No | No | 6.1 |
| CVE-2025-38678 | netfilter: nf_tables: reject duplicate device on updates | No | No | 6 |
| CVE-2025-9901 | Libsoup: improper handling of http vary header in libsoup caching | No | No | 5.9 |
| CVE-2025-39681 | x86/cpu/hygon: Add missing resctrl_cpu_detect() in bsp_init helper | No | No | 5.5 |
| CVE-2025-39718 | vsock/virtio: Validate length in packet header before skb_put() | No | No | 5.5 |
| CVE-2025-39692 | smb: server: split ksmbd_rdma_stop_listening() out of ksmbd_rdma_destroy() | No | No | 5.5 |
| CVE-2025-38728 | smb3: fix for slab out of bounds on mount to ksmbd | No | No | 5.5 |
| CVE-2025-38711 | smb/server: avoid deadlock when linking with ReplaceIfExists | No | No | 5.5 |
| CVE-2025-39724 | serial: 8250: fix panic due to PSLVERR | No | No | 5.5 |
| CVE-2025-39676 | scsi: qla4xxx: Prevent a potential error pointer dereference | No | No | 5.5 |
| CVE-2025-39726 | s390/ism: fix concurrency management in ism_cmd() | No | No | 5.5 |
| CVE-2025-38704 | rcu/nocb: Fix possible invalid rdp's->nocb_cb_kthread pointer access | No | No | 5.5 |
| CVE-2025-39715 | parisc: Revise gateway LWS calls to probe user read access | No | No | 5.5 |
| CVE-2025-39716 | parisc: Revise __get_user() to probe user read access | No | No | 5.5 |
| CVE-2025-38691 | pNFS: Fix uninited ptr deref in block/scsi layout | No | No | 5.5 |
| CVE-2025-38721 | netfilter: ctnetlink: fix refcount leak on table dump | No | No | 5.5 |
| CVE-2025-38725 | net: usb: asix_devices: add phy_mask for ax88772 mdio bus | No | No | 5.5 |
| CVE-2025-38736 | net: usb: asix_devices: Fix PHY address mask in MDIO bus initialization | No | No | 5.5 |
| CVE-2025-38717 | net: kcm: Fix race condition in kcm_unattach() | No | No | 5.5 |
| CVE-2025-38734 | net/smc: fix UAF on smcsk after smc_listen_out() | No | No | 5.5 |
| CVE-2025-38681 | mm/ptdump: take the memory hotplug lock inside ptdump_walk_pgd() | No | No | 5.5 |
| CVE-2025-39709 | media: venus: protect against spurious interrupts during probe | No | No | 5.5 |
| CVE-2025-38679 | media: venus: Fix OOB read due to missing payload bound check | No | No | 5.5 |
| CVE-2025-39714 | media: usbtv: Lock resolution while streaming | No | No | 5.5 |
| CVE-2025-39720 | ksmbd: fix refcount leak causing resource not released | No | No | 5.5 |
| CVE-2025-38730 | io_uring/net: commit partial buffers on retry | No | No | 5.5 |
| CVE-2025-39687 | iio: light: as73211: Ensure buffer holes are zeroed | No | No | 5.5 |
| CVE-2025-39719 | iio: imu: bno055: fix OOB access of hw_xlate array | No | No | 5.5 |
| CVE-2025-38712 | hfsplus: don't use BUG_ON() in hfsplus_create_attributes_file() | No | No | 5.5 |
| CVE-2025-38715 | hfs: fix slab-out-of-bounds in hfs_bnode_read() | No | No | 5.5 |
| CVE-2025-38716 | hfs: fix general protection fault in hfs_find_init() | No | No | 5.5 |
| CVE-2025-38722 | habanalabs: fix UAF in export_dmabuf() | No | No | 5.5 |
| CVE-2025-38707 | fs/ntfs3: Add sanity check for file name | No | No | 5.5 |
| CVE-2025-39731 | f2fs: vm_unmap_ram() may be called from an invalid context | No | No | 5.5 |
| CVE-2025-39679 | drm/nouveau/nvif: Fix potential memory leak in nvif_vmm_ctor(). | No | No | 5.5 |
| CVE-2025-39706 | drm/amdkfd: Destroy KFD debugfs after destroy KFD wq | No | No | 5.5 |
| CVE-2025-39707 | drm/amdgpu: check if hubbub is NULL in debugfs/amdgpu_dm_capabilities | No | No | 5.5 |
| CVE-2025-38705 | drm/amd/pm: fix null pointer access | No | No | 5.5 |
| CVE-2025-39705 | drm/amd/display: fix a Null pointer dereference vulnerability | No | No | 5.5 |
| CVE-2025-39693 | drm/amd/display: Avoid a NULL pointer dereference | No | No | 5.5 |
| CVE-2025-39675 | drm/amd/display: Add null pointer check in mod_hdcp_hdcp1_create_session() | No | No | 5.5 |
| CVE-2025-39685 | comedi: pcl726: Prevent invalid irq number | No | No | 5.5 |
| CVE-2025-38687 | comedi: fix race between polling and detaching | No | No | 5.5 |
| CVE-2025-39686 | comedi: Make insn_rw_emulate_bits() do insn->n samples | No | No | 5.5 |
| CVE-2025-39684 | comedi: Fix use of uninitialized memory in do_insn_ioctl() and do_insnlist_ioctl() | No | No | 5.5 |
| CVE-2025-39697 | NFS: Fix a race when updating an existing write | No | No | 5.5 |
| CVE-2025-38696 | MIPS: Don't crash in stack_top() for tasks without ABI or vDSO | No | No | 5.5 |
| CVE-2025-38723 | LoongArch: BPF: Fix jump offset calculation in tailcall | No | No | 5.5 |
| CVE-2025-38700 | scsi: libiscsi: Initialize iscsi_conn->dd_data only if memory is allocated | No | No | 4.7 |
| CVE-2025-38706 | ASoC: core: Check for rtd == NULL in snd_soc_remove_pcm_runtime() | No | No | 4.7 |
| CVE-2025-7039 | Glib: buffer under-read on glib through glib/gfileutils.c via get_tmp_file() | No | No | 3.7 |
| CVE-2025-38680 | media: uvcvideo: Fix 1-byte out-of-bounds read in uvc_parse_format() | No | No | 3.3 |
| CVE-2025-39710 | media: venus: Add a check for packet size after reading from shared memory | No | No | N/A |
| CVE-2025-39701 | ACPI: pfr_update: Fix the driver update version check | No | No | N/A |
SQL Server vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-55227 | Microsoft SQL Server Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-47997 | Microsoft SQL Server Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2024-21907 | VulnCheck: CVE-2024-21907 Improper Handling of Exceptional Conditions in Newtonsoft.Json | No | Yes | N/A |
Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-54111 | Windows UI XAML Phone DatePickerFlyout Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54913 | Windows UI XAML Maps MapControlSettings Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-55224 | Windows Hyper-V Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-54092 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-55228 | Windows Graphics Component Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53800 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54102 | Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53801 | Microsoft DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-54919 | Windows Graphics Component Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2025-53805 | HTTP.sys Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2025-54103 | Windows Management Service Elevation of Privilege Vulnerability | No | No | 7.4 |
| CVE-2025-54116 | Windows MultiPoint Services Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2025-55236 | Graphics Kernel Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2025-54115 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53807 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-54114 | Windows Connected Devices Platform Service (Cdpsvc) Denial of Service Vulnerability | No | No | 7 |
| CVE-2025-53802 | Windows Bluetooth Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-49734 | PowerShell Direct Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-54112 | Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-54105 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-55223 | DirectX Graphics Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-54108 | Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53809 | Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability | No | No | 6.5 |

