Network traffic analysis (NTA) is an essential way to monitor network availability and activity to identify anomalies, maximize performance, and keep an eye out for attacks. Alongside log aggregation, UEBA, and endpoint data, network traffic is a core piece of the comprehensive visibility and security analysis to discover threats early and extinguish them fast. Common use cases for NTA include:
-
Collecting a real-time and historical record of what’s happening on your network
-
Detecting malware such as ransomware activity
-
Detecting the use of vulnerable protocols and ciphers
-
Troubleshooting a slow network
-
Improving internal visibility
-
Eliminating blind spots
Implementing a solution that can continuously monitor network traffic gives you the insight you need to optimize network performance, minimize your attack surface, enhance security, and improve the management of your resources. When choosing a NTA solution, consider the current blind spots on your network, the data sources you need information from, and the critical points on the network where they converge for efficient monitoring. With NTA added as a layer to your security information and event management (SIEM) solution, you’ll gain visibility into even more of your environment and your users.
More Network Traffic Analysis Resources
Why Does NTA Security Matter?
Keeping a close eye on your network perimeter is always good practice. Even with strong firewalls in place, mistakes can happen and rogue traffic could get through. Users could also leverage methods such as tunneling, external anonymizers, and VPNs to get around firewall rules.
Additionally, the rise of ransomware as a common attack type in recent years makes network traffic monitoring even more critical. A network monitoring solution should be able to detect activity indicative of ransomware attacks via insecure protocols. Take WannaCry, for example, where attackers actively scanned for networks with TCP port 445 open, and then used a vulnerability in SMBv1 to access network file shares.
Monitoring traffic inside your firewalls allows you to validate rules, gain valuable insight, and can also be used as a source of network traffic-based alerts.
How Does a Network Traffic Analysis Tool Work?
Network Traffic Analysis solutions collect network traffic metadata for analysis and observation. Not all tools for monitoring network traffic are the same. Generally, they can be broken down into two types: flow-based tools and deep packet inspection (DPI) tools. Within these tools you’ll have options for software agents, storing historical data, and intrusion detection systems. When evaluating which solution is right for your organization, consider these five things:
Availability of flow-enabled devices: Do you have flow-enabled devices on your network capable of generating the flows required by a NTA tool that only accepts flows like Cisco Netflow?
The data source: Flow data and packet data come from different sources, and not all NTA tools collect both.
The points on the network: Be careful not to monitor too many data sources right out the gate. Instead, be strategic in picking locations where data converges, such as internet gateways or VLANs associated with critical servers.
Real-time data vs. historical data: Historical data is critical to analyzing past events, but some tools for monitoring network traffic don’t retain that data as time goes on.
Full packet capture, cost and complexity: Some DPI tools capture and retain all packets, resulting in expensive appliances, increased storage costs, and much training/expertise to operate. Others do more of the 'heavy lifting,’ capturing full packets but extracting only the critical detail and metadata for each protocol.
A key step of setting up NTA is ensuring you’re collecting data from the right sources. Flow data is great if you are looking for traffic volumes and mapping the journey of a network packet from its origin to its destination, but it can lack rich detail and context to dig into cybersecurity issues.
Deep packet inspection (DPI) tools can help network managers understand how users are implementing/operating applications, track usage on WAN links, and monitor for suspicious malware or other security incidents, providing 100% visibility over the network and enabling network and security managers to drill down to the minutest detail.
The Importance of NTA Security in Threat Detection and Response Programs
Network Traffic Analysis is a critical piece of modern threat detection and response practices because many operational and security issues can be investigated by implementing NTA at both the network edge and the network core. With a traffic analysis tool, you can spot things like large downloads, streaming, or suspicious inbound or outbound traffic.
NTA also provides an organization with more visibility into threats on their networks, beyond the endpoint. With the rise in mobile devices, IoT devices, smart TV’s, etc., you need something with more intelligence than just the logs from firewalls. Firewall logs are also problematic when a network is under attack. You may find that they are inaccessible due to resource load on the firewall or that they’ve been overwritten (or sometimes even modified by hackers), resulting in the loss of vital forensic information.
Use cases for analyzing and monitoring network traffic include:
- Detection of ransomware activity
- Monitoring data exfiltration/internet activity
- Monitor access to files on file servers or MSSQL databases
- Track a user’s activity on the network, though User Forensics reporting
- Provide an inventory of what devices, servers and services are running on the network
- Highlight and identity root cause of bandwidth peaks on the network
How Rapid7 Can Help You Monitor and Analyze Network Traffic
By deploying the lightweight Insight Network Sensor, InsightIDR customers can continuously monitor network traffic at any location or site across their network. This data builds visibility across the attack surface and detects intrusions (or other potential security events) on the network. Together, alongside the existing user, log, and endpoint data in InsightIDR, network traffic analysis will help analysts ensure continuous visibility everywhere, recognize compromise quickly, and trace the steps of potential attackers across systems and applications.
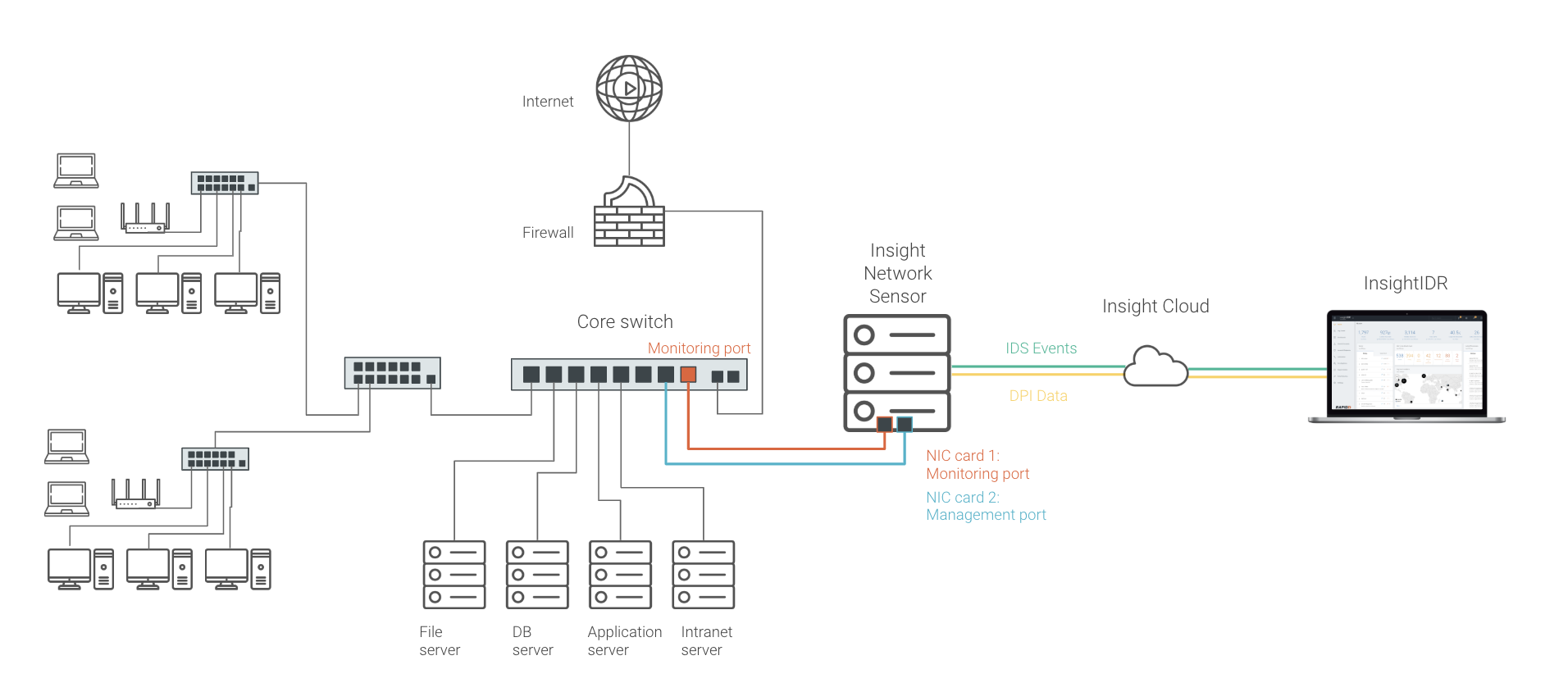
The Insight Network Sensor is easily downloaded and deployed, either on-premises or on a virtual VMware network. The sensor collects all network traffic metadata for analysis and observation on the central management portal, without interacting with other devices or impacting network performance. These IDS events and DPI data are passed to InsightIDR and aggregated with other critical data sources.
Traditional Intrusion Detection System (IDS) tools can be incredibly noisy. The Rapid7 managed detection and response (MDR) services team has carefully filtered IDS events to capture only the most critical and actionable detections. This means when malware, botnets, or other compromises are detected, teams won’t have to go through tedious cycles to determine their validity. Analysts can take action confidently, on reliable, vetted alerts.
Rapid7’s proprietary DPI engine captures and analyzes traffic in readable, interpretable details, without the complexity and overhead of full packet capture. This passive analysis also means no performance impact to the network. With this rich flow data, teams have deep detail with which to track attacker entry and movement across the network. This can help accelerate investigations and inform response action.