Microsoft is addressing 61 vulnerabilities this May 2024 Patch Tuesday. Microsoft has evidence of in-the-wild exploitation and/or public disclosure for three of the vulnerabilities published today. At time of writing, two of the vulnerabilities patched today are listed on CISA KEV. Microsoft is also patching a single critical remote code execution (RCE) vulnerability today. Six browser vulnerabilities were published separately this month, and are not included in the total.
Windows DWM: zero-day EoP
The first of today’s zero-day vulnerabilities is CVE-2024-30051, an elevation of privilege (EoP) vulnerability in the Windows Desktop Windows Manager (DWM) Core Library which is listed on the CISA KEV list. Successful exploitation grants SYSTEM privileges. First introduced as part of Windows Vista, DWM is responsible for drawing everything on the display of a Windows system.
Reporters Securelist have linked exploitation of CVE-2024-30051 with deployment of QakBot malware, and the vulnerability while investigating a partial proof-of-concept contained within an unusual file originally submitted to VirusTotal by an unknown party. Securelist further notes that the exploitation method for CVE-2024-30051 is identical to a previous DWM zero-day vulnerability CVE-2023-36033, which Microsoft patched back in November 2023.
Courtesy of Microsoft’s recent enhancement of their security advisories to include Common Weakness Enumeration (CWE) data, the mechanism of exploitation is listed as CVE-122: Heap-based Buffer Overflow, which is just the sort of defect which recent US federal government calls for memory safe software development are designed to address.
MSHTML: zero-day security feature bypass
The Windows MSHTML platform receives a patch for CVE-2024-30040, a security feature bypass vulnerability for which Microsoft has evidence of exploitation in the wild, and which CISA has also listed on KEV.
The advisory states that an attacker would have to convince a user to open a malicious file; successful exploitation bypasses COM/OLE protections in Microsoft 365 and Microsoft Office to achieve code execution in the context of the user.
As Rapid7 has previously noted, MSHTML (also known as Trident) is still fully present in Windows — and unpatched assets are thus vulnerable to CVE-2024-30040 — regardless of whether or not a Windows asset has Internet Explorer 11 fully disabled.
Visual Studio: zero-day DoS
Rounding out today’s trio of zero-day vulnerabilities: a denial of service (DoS) vulnerability in Visual Studio.
Microsoft describes CVE-2024-30046 as requiring a highly complex attack to win a race condition through “[the investment of] time in repeated exploitation attempts through sending constant or intermittent data”. Since all data sent anywhere is transmitted either constantly or intermittently, and the rest of the advisory is short on detail, the potential impact of exploitation remains unclear.
Only Visual Studio 2022 receives an update, so older supported versions of Visual Studio are presumably unaffected.
SharePoint: critical post-auth RCE
SharePoint admins are no strangers to patches for critical RCE vulnerabilities. CVE-2024-30044 allows an authenticated attacker with Site Owner permissions or higher to achieve code execution in the context of SharePoint Server via upload of a specially crafted file, followed by specific API calls to trigger deserialization of the file’s parameters.
Microsoft considers exploitation of CVE-2024-30044 more likely. The original version of the advisory had the "privileges required" CVSS vector component as low, which was debatable given the Site Owner authentication requirement for exploitation; Microsoft has now updated the advisory so that "privileges required" is now correctly specified as high. Some slight confusion remains in the wording of the advisory FAQ, but the correction to the CVSS vector itself is welcome. The low attack complexity and network attack contribute to a CVSS 3.1 base score of 7.2, which is reduced from the original base score of 8.8 prior to the CVSS vector correction.
Microsoft has previously published an accessible introduction to deserialization vulnerabilities and the risks of assuming data to be trustworthy, aimed at .NET developers.
Excel: arbitrary code execution
Microsoft Excel receives a patch for CVE-2024-30042. Successful exploitation requires that an attacker convince the user to open a malicious file, which leads to code execution, presumably in the context of the user.
Remote Access Connection Manager: last month’s vulns repatched
Also of interest today: Microsoft is releasing updated patches for three Windows Remote Access Connection Manager information disclosure vulnerabilities originally published in April 2024: CVE-2024-26207, CVE-2024-26217, and CVE-2024-28902. Microsoft states that an unspecified regression introduced by the April patches is resolved by installation of the May patches.
Mobile Broadband driver: 11 local USB RCEs
The Windows Mobile Broadband driver receives patches for no fewer than 11 vulnerabilities; for example, CVE-2024-29997. All 11 vulnerabilities appear very similar based on the advisories. In each case, the relatively low CVSS base score of 6.8 reflects that an attacker must be physically present and insert a malicious USB device into the target host.
Third-party open source patches
Back in 2021, Microsoft started publishing the Assigning CNA (CVE Numbering Authority) field on advisories. A welcome trend of publishing advisories for third-party software included in Microsoft products continues this month with two vulnerabilities in MinGit patched as part of the May 2024 Windows security updates. MinGit is published by GitHub and consumed by Visual Studio. CVE-2024-32002 describes a RCE vulnerability on case-insensitive filesystems that support symlinks — macOS APFS comes to mind — and CVE-2024-32004 describes RCE while cloning specially-crafted local repositories.
Lifecycle update
There are no significant changes to the lifecycle phase of Microsoft products this month.
Summary Charts
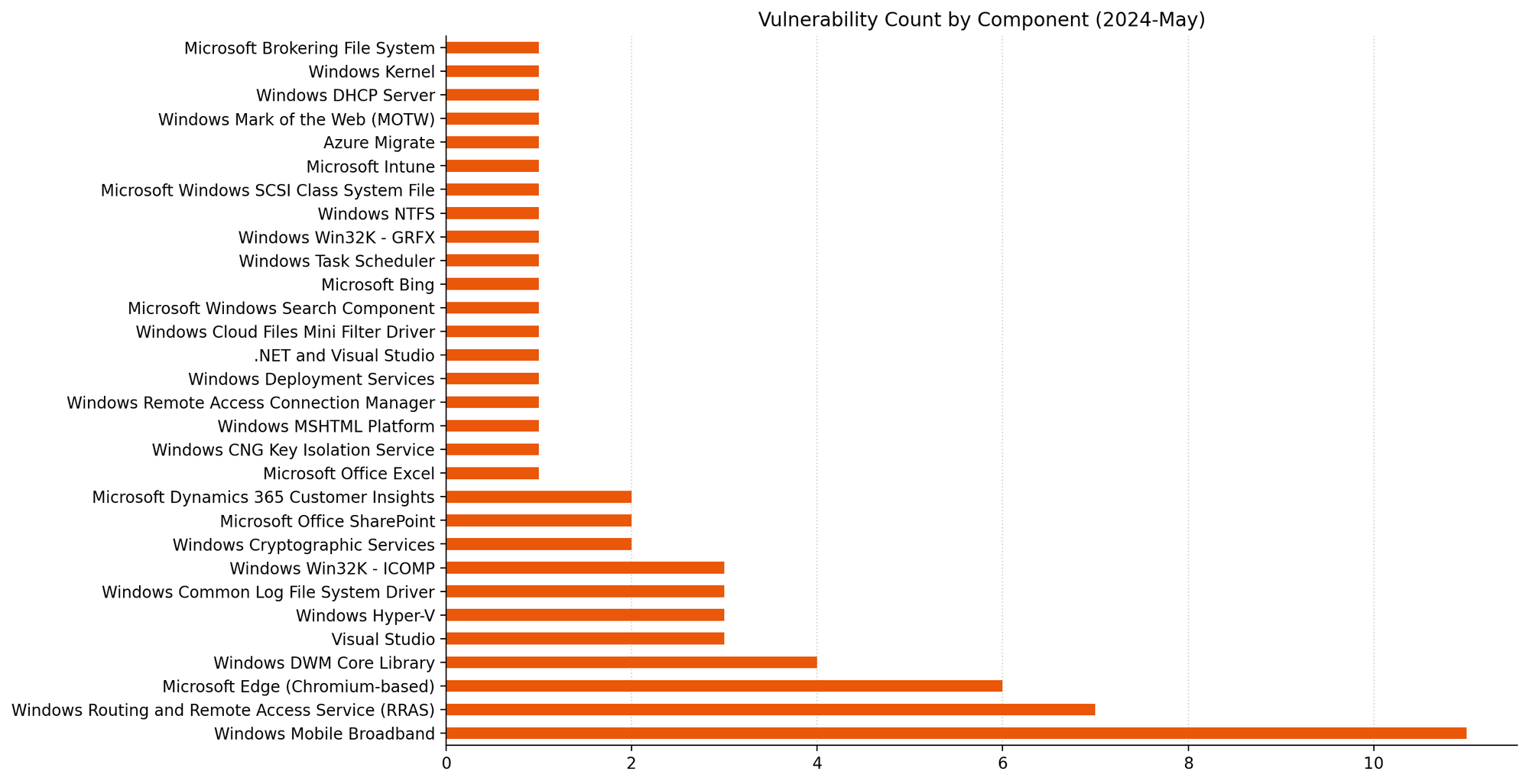
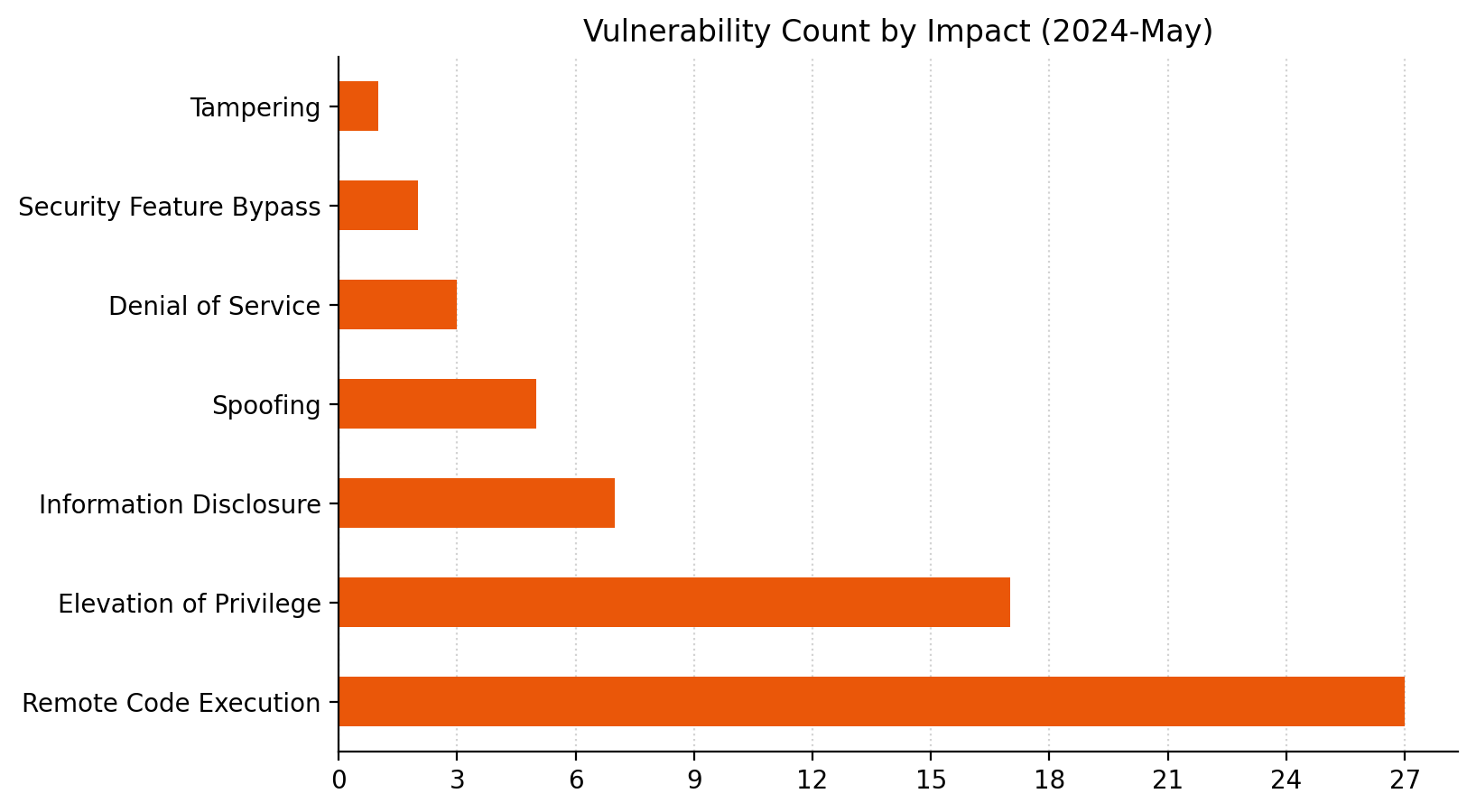
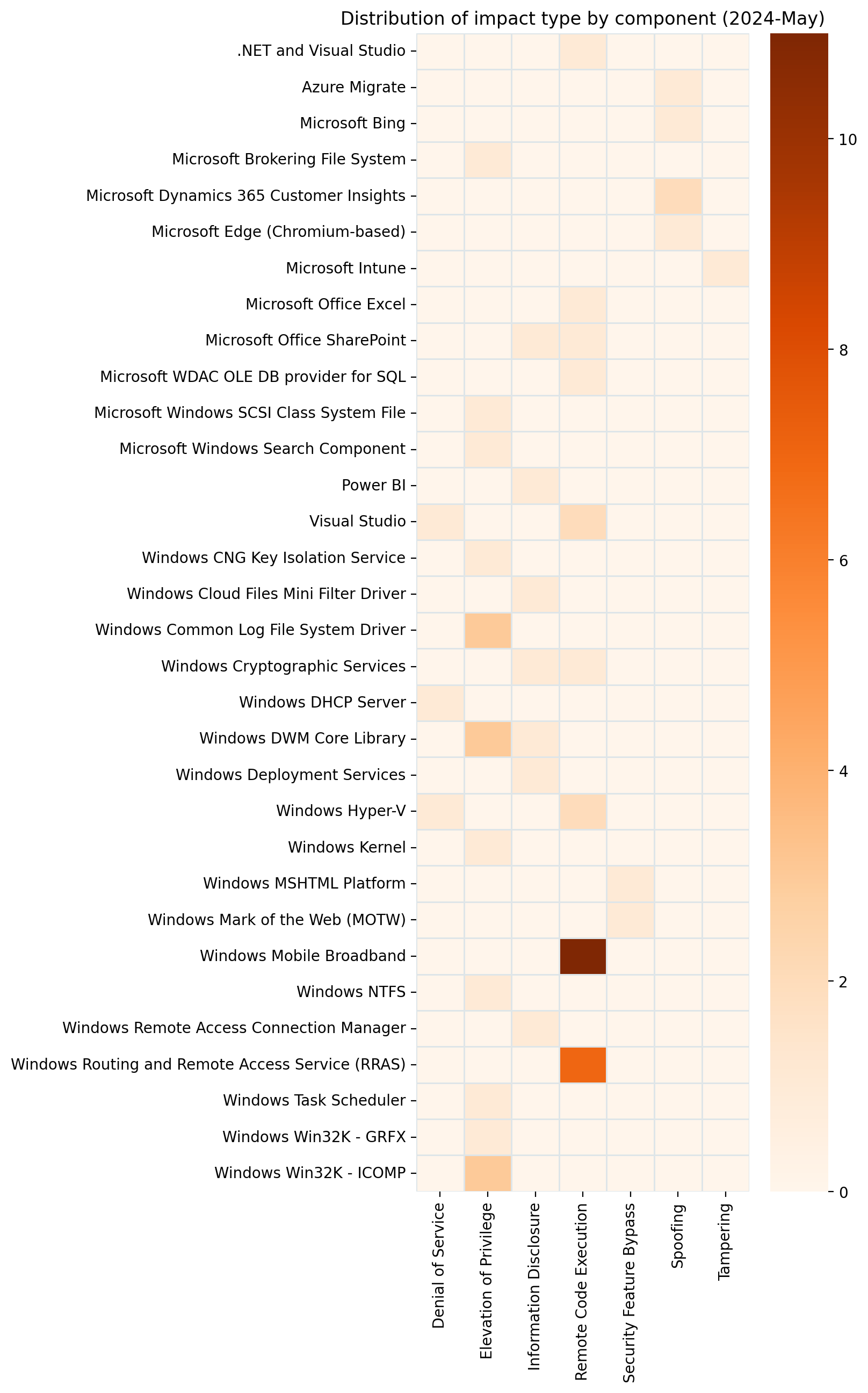
Summary Tables
Apps vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30059 | Microsoft Intune for Android Mobile Application Management Tampering Vulnerability | No | No | 6.1 |
| CVE-2024-30041 | Microsoft Bing Search Spoofing Vulnerability | No | No | 5.4 |
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30053 | Azure Migrate Cross-Site Scripting Vulnerability | No | No | 6.5 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30055 | Microsoft Edge (Chromium-based) Spoofing Vulnerability | No | No | 5.4 |
| CVE-2024-4671 | Chromium: CVE-2024-4671 Use after free in Visuals | No | No | N/A |
| CVE-2024-4559 | Chromium: CVE-2024-4559 Heap buffer overflow in WebAudio | No | No | N/A |
| CVE-2024-4558 | Chromium: CVE-2024-4558 Use after free in ANGLE | No | No | N/A |
| CVE-2024-4368 | Chromium: CVE-2024-4368 Use after free in Dawn | No | No | N/A |
| CVE-2024-4331 | Chromium: CVE-2024-4331 Use after free in Picture In Picture | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-32002 | CVE-2024-32002 Recursive clones on case-insensitive filesystems that support symlinks are susceptible to Remote Code Execution | No | No | 9 |
| CVE-2024-32004 | GitHub: CVE-2024-32004 Remote Code Execution while cloning special-crafted local repositories | No | No | 8.1 |
| CVE-2024-30045 | .NET and Visual Studio Remote Code Execution Vulnerability | No | No | 6.3 |
| CVE-2024-30046 | Visual Studio Denial of Service Vulnerability | No | Yes | 5.9 |
ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30030 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30009 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-30010 | Windows Hyper-V Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-30006 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-30020 | Windows Cryptographic Services Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2024-30049 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-29996 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30025 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30031 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30028 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30038 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30027 | NTFS Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30014 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-30015 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-30022 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-30023 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-30024 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-30029 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-30037 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.5 |
| CVE-2024-30011 | Windows Hyper-V Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2024-30036 | Windows Deployment Services Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2024-30019 | DHCP Server Service Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2024-30039 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-30016 | Windows Cryptographic Services Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-30050 | Windows Mark of the Web Security Feature Bypass Vulnerability | No | No | 5.4 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30047 | Dynamics 365 Customer Insights Spoofing Vulnerability | No | No | 7.6 |
| CVE-2024-30048 | Dynamics 365 Customer Insights Spoofing Vulnerability | No | No | 7.6 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30044 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-30042 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2024-30043 | Microsoft SharePoint Server Information Disclosure Vulnerability | No | No | 6.5 |
SQL Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30054 | Microsoft Power BI Client JavaScript SDK Information Disclosure Vulnerability | No | No | 6.5 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-30040 | Windows MSHTML Platform Security Feature Bypass Vulnerability | Yes | No | 8.8 |
| CVE-2024-30017 | Windows Hyper-V Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-30007 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2024-30018 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30051 | Windows DWM Core Library Elevation of Privilege Vulnerability | Yes | Yes | 7.8 |
| CVE-2024-30032 | Windows DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30035 | Windows DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-29994 | Microsoft Windows SCSI Class System File Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-26238 | Microsoft PLUGScheduler Scheduled Task Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-30033 | Windows Search Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-29997 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-29998 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-29999 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30000 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30001 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30002 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30003 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30004 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30005 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30012 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30021 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-30008 | Windows DWM Core Library Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2024-30034 | Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability | No | No | 5.5 |
Updates
- 2024-05-16: Updated SharePoint vulnerability CVE-2024-30044 to reflect Microsoft's correction to the CVSS vector, as suggested by the original version of this blog post.

