Metasploit Pro's smart exploitation function is great if you want to get a session quickly and don't care about being "noisy" on the network, but there are certain situations where you may want to use just one exploit:
- You're conducting a penetration test and want to exploit just one vulnerability so you don't draw too much attention (i.e. you want to use a sniper rifle, not a machine gun)
- You're a vulnerability manager and want to validate just one vulnerability to know whether you need to fix it
- You've just remediated a vulnerability and want to know if your measures stop the vulnerability from being exploited
Here's a quick recipe on how to do this with Metasploit Pro:
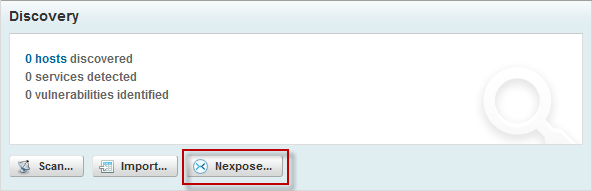
- Run a Nexpose scan to identify vulnerabilities. You must have Nexpose installed on the same machine to do this - either the commercial versions or the free vulnerability scanner Nexpose Community Edition. For other ways to import third-party vulnerability scanner reports or to import existing scans from Nexpose Enterprise scan engines, read the blog post Three Ways to Integrate Metasploit With Nexpose.
- In the Analysis tab, click on Hosts. Then, click on the host that has the vulnerability you want to exploit.
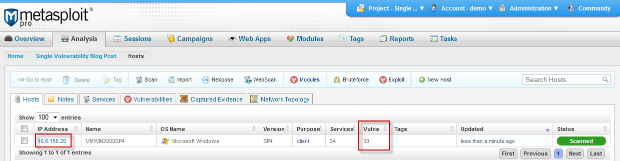
- Click on the Vulnerabilities tab and click on the Exploit in associated to the vulnerability you want to exploit
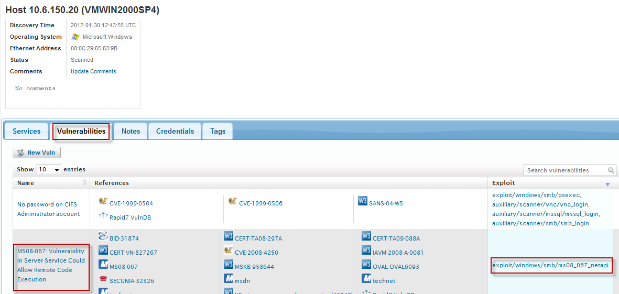
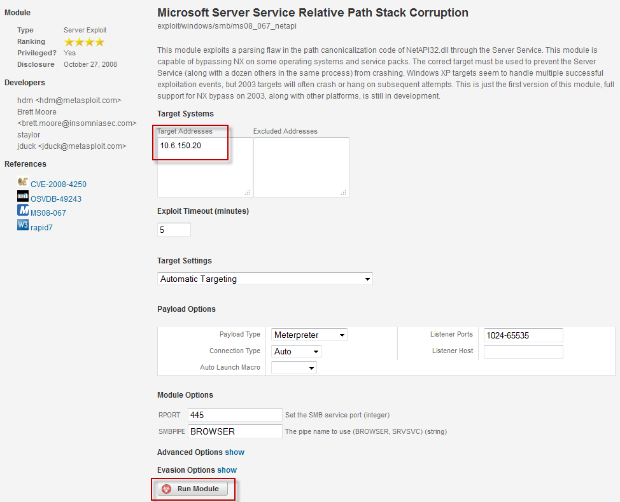
- You'll see the module page for the exploit you have just chosen. The host IP is already pre-filled. Click Run Module
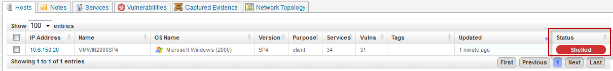
- If the module fails to exploit this vulnerability, you will see an error message in the console text and no session for this host. On the hosts tab, the status will say "scanned" (not "shelled").
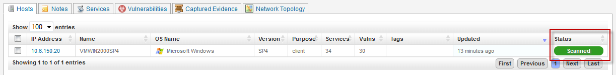
-
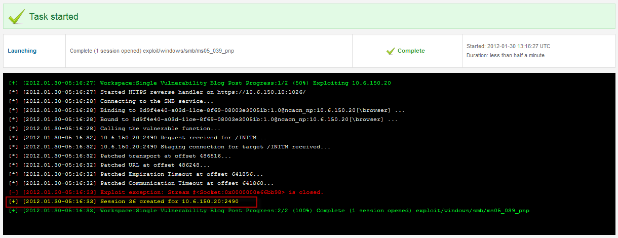
If the module successfully exploits a vulnerability and creates a session, you'll see:
- A yellow line in the console Session xx created
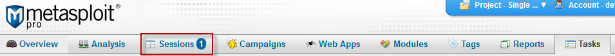
- The number 1 next to the sessions navigation menu item (or a higher number if you have already created other sessions before)
- On the host tab, the label Shelled next to the host IP