[Last Update: October 27, 2021]
For approximately 4 hours on Friday, October 22, 2021, a widely utilized NPM package, ua-parser-js, was embedded with a malicious script intended to install a coinminer and harvest user/credential information. This package is used “to detect Browser, Engine, OS, CPU, and Device type/model from User-Agent data,” with nearly 8 million weekly downloads and 1,200 dependencies.
The malicious package was available for download starting on October 22, 2021, at 12:15 PM GMT, and ending October 22, 2021, between 4:16 PM and 4:26 PM GMT. During that time, 3 versions of the package were compromised with a script that would execute on Windows and Linux machines:
| Affected Version | Patched Version |
|---|---|
| 0.7.29 | 0.7.30 |
| 0.8.0 | 0.8.1 |
| 1.0.0 | 1.0.1 |
Both GitHub and CISA issued advisories urging users to upgrade right away and review systems for suspicious or malicious activity.
Due to the quick reporting of issues by GitHub users and action by the developer, development exposure will be limited to teams who had a pull/build during that (roughly) 4-hour timeframe.
At this time, the source of the attack is unconfirmed. However, with the use of IntSights, recently acquired by Rapid7, a suspicious thread has been identified, created on October 5, 2021, in a prominent Russian hacking forum. There, a threat actor offered access to a developer account of an undisclosed package on npmjs.com, indicating that the package has “more than 7 million installations every week, more than 1,000 others are dependent on this.” With the requested price of $20,000 dollars, the threat actor stated that the account does not have 2-factor authentication.
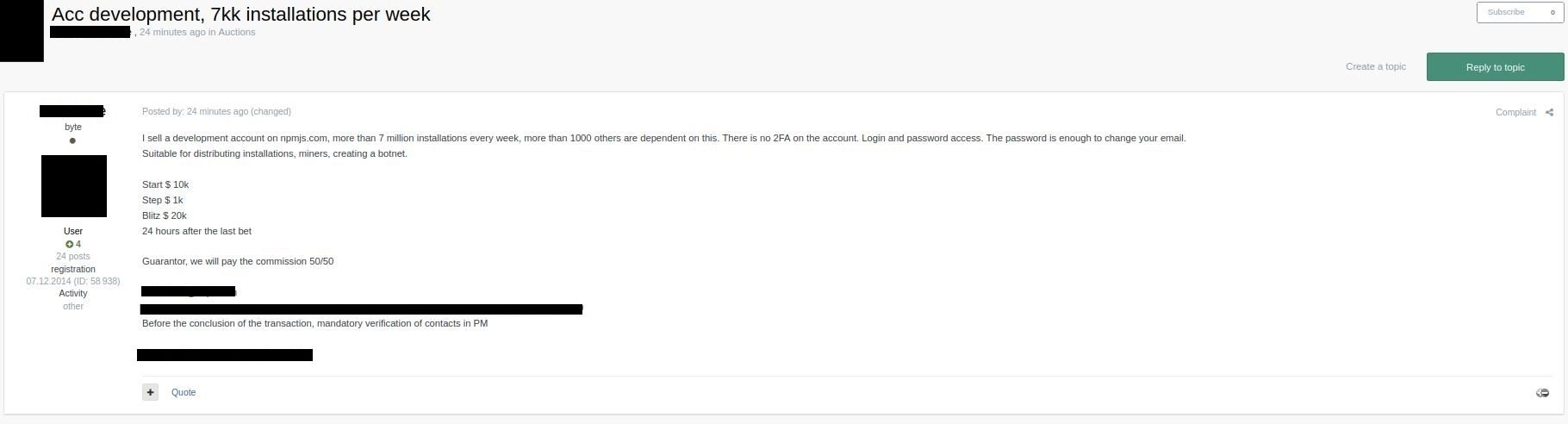
While there is no definitive evidence that the compromise of ua-parser-js is related to the above-mentioned dark-web activity, the weekly installs and dependency numbers appear to match and align with the developers' post of an account hijack.
Rapid7 guidance
Rapid7 recommends development teams immediately heed the advice for organizations to review for the use of these versions and remediate accordingly. Additionally, organizations’ security teams need to be on the lookout for users who visited a site infected with the malicious script. Several anti-malware programs have (or have since added) detections for this, and organizations should keep an eye open for network traffic that is hitting domains/IPs associated with coin mining.
Rapid7 customers
InsightVM
Updated October 27, 2021:
InsightVM users can assess their exposure to malicious versions of the ua-parser-js package via Container Security functionality. No Scan Engine or Insight Agent-based checks are currently planned.
InsightIDR
InsightIDR customers, including Managed Detection & Response customers, are already equipped to identify suspicious activity by way of InsightIDR's built-in detection rules. Alerts generated by these detection rules may be indicative of related malicious activity:
- Cryptocurrency Miner - XMRig
- Suspicious Process - Curl to External IP Address
- Wget to External IP Address
Additionally, Rapid7 has updated the following detection rules to provide additional coverage:
- Cryptocurrency Miner - Mining Pool URL in Command Line
- Attacker Technique - Determining External IP Via Command Line
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe