Microsoft is addressing 105 vulnerabilities this October Patch Tuesday, including three zero-day vulnerabilities, as well as 12 critical remote code execution (RCE) vulnerabilities, and one republished third-party vulnerability.
WordPad: zero-day NTLM hash disclosure
Another Patch Tuesday, another zero-day vulnerability offering NTLM hash disclosure, this time in WordPad. The advisory for CVE-2023-36563 describes two possible attack vectors:
- enticing the user to open a specially crafted malicious file delivered via email, IM, or some other means, or;
- by causing a custom application to run.
The advisory itself doesn’t give much more detail, but to take full advantage, the attacker would either need prior access to the system, or some means of exfiltrating the NTLM hash as part of the attack. Microsoft has published further detail on the attack mechanism under KB5032314, as well as mitigation strategies. WordPad is vulnerable due to its use of the OleConvertOLESTREAMToIStorage and OleConvertOLESTREAMToIStorageEx Windows API functions, so the same is presumably true of other applications which make use of those functions.
It may or may not be a coincidence that Microsoft announced last month that WordPad is no longer being updated, and will be removed in a future version of Windows, although no specific timeline has yet been given. Unsurprisingly, Microsoft recommends Word as a replacement for WordPad.
Skype for Business server: zero-day info disclosure
Defenders responsible for a Skype for Business server should take note of an exploited-in-the-wild information disclosure vulnerability for which public exploit code exists. Successful exploitation of CVE-2023-41763 via a specially crafted network call could result in the disclosure of IP addresses and/or port numbers. Although Microsoft does not specify what the scope of the disclosure might be, it will presumably be limited to whatever the Skype for Business server can see; as always, appropriate network segmentation will pay defense-in-depth dividends.
ASP.NET Kestrel web server: zero-day denial of service
Rounding out this month’s trio of exploited-in-the-wild vulnerabilities: the cross-platform Kestrel web server for ASP.NET Core receives a fix for CVE-2023-44487, a denial of service vulnerability.
CVE-2023-44487 is perhaps of less concern to defenders, unless the Kestrel instance is internet-facing. Dubbed "HTTP/2 rapid reset", the vulnerability is not specific to Microsoft, but is inherent to HTTP/2. Exploitation involves abuse of the lack of bounds on HTTP/2 request cancellation to bring about severe load on the server for a very low cost to the attacker.
In the advisory, Microsoft provides essentially no information about attack vector beyond the fact that the vulnerability is specific to HTTP/2 , but does suggest two potential workarounds:
- Disabling the HTTP/2 protocol via a Windows Registry modification; and/or
- Restricting protocols offered each Kestrel endpoint to exclude HTTP/2.
Downgrading to HTTP/1.1 is likely to lead to a significant degradation in performance. Microsoft advises timely patching, whether or not workarounds are applied.
N.B. In the Microsoft advisory, a hyperlink attached to the word “workarounds” does not resolve to anything specific, and Kestrel is misspelled as “Kestral” more than once, although these issues will likely be resolved soon.
Layer 2 Tunneling Protocol: lots of critical RCEs
Twelve critical RCE vulnerabilities seems like a lot, and it is. Fully three-quarters of these are in the same Windows component — the Layer 2 Tunneling Protocol — which has already received fixes for a significant number of critical RCEs in recent months. Exploitation of each of the Layer 2 Tunneling Protocol critical RCEs this month — CVE-2023-41765 CVE-2023-41767 CVE-2023-41768 CVE-2023-41769 CVE-2023-41770 CVE-2023-41771 CVE-2023-41773 CVE-2023-41774 and CVE-2023-38166 — is via a specially crafted protocol message to a Routing and Remote Access Service (RRAS) server.
If there is a silver lining here, it’s that the acknowledgements for almost all of these vulnerabilities cite Microsoft’s Network Security and Containers (NSC) team; a reasonable inference is that Microsoft is directing significant resources towards security research and patching in this area. Since CVEs are typically assigned sequentially, and there are gaps in the sequence, another reasonable inference here is that other similar as-yet-unpublished vulnerabilities have probably been identified and reported to MSRC.
Windows MSMQ: critical RCEs
CVE-2023-35349 describes an RCE vulnerability in the Message Queueing Service. Microsoft does not describe the attack vector, but other similar vulnerabilities require that the attacker send specially crafted malicious MSMQ packet to a MSMQ server. One mitigating factor: the Microsoft Message Queueing Service must be enabled and listening on port 1801 for an asset to be vulnerable, and the Message Queueing Service is not installed by default. As Rapid7 has noted previously, however, a number of applications – including Microsoft Exchange – may quietly introduce MSMQ as part of their own installation routine.
Another MSMQ RCE vulnerability also receives a patch this month: CVE-2023-36697 has a lower CVSS score than its sibling, both because valid domain credentials are required, and because exploitation requires that a user on the target machine connects to a malicious server. Alternatively, Microsoft suggests that an attacker could compromise a legitimate MSMQ server host and make it run as a malicious server to exploit this vulnerability, although it’s not immediately clear how the attacker could do that without already having significant control over the MSMQ host.
Microsoft vTPM: container escape
The final constituent of this month’s dozen patched critical RCE vulnerabilities is rather more exotic: CVE-2023-36718 describes a vulnerability in the Microsoft Virtual Trusted Platform Module (vTPM), which is a TPM 2.0-compliant virtualized version of a hardware TPM offered as a feature of Azure confidential VMs. Successful exploitation could lead to a container escape. The attacker would first need to access the vulnerable VM, and the advisory notes that exploitation is possible when authenticated as a guest mode user. On the bright side, Microsoft evaluates attack complexity as High, since successful exploitation of this vulnerability would rely upon complex memory shaping techniques to attempt an attack.
Exchange (as is tradition): RCE
Exchange administrators should note the existence of CVE-2023-36778, a same-network RCE vulnerability in all current versions of Exchange Server. Successful exploitation requires that the attacker be on the same network as the Exchange Server host, and use valid credentials for an Exchange user in a PowerShell remoting session. By default, PowerShell Remoting only allows connections from members of the Administrators group, and the relevant Windows Firewall rule for connections via public networks rejects connections from outside the same subnet. Defenders may wish to review these rules to ensure that they have not been loosened beyond the default.
Office: LPE
Microsoft Office receives a patch for CVE-2023-36569, a local privilege escalation (LPE) vulnerability. Successful exploitation could lead to SYSTEM privileges, but Microsoft states that the Preview Pane is not a vector. The advisory doesn’t provide much more information; patches are available for Office 2019, 2021, and Apps for Enterprise. Office 2016 is not listed, which might signify that it isn’t vulnerable, or could mean that patches will be provided later.
Server 2012 & Server 2012 R2: end of support, unless you pay for ESU
Today is the final Patch Tuesday for Windows Server 2012, and Windows Server 2012 R2. The only way to receive security updates for these versions of Windows from now on is to subscribe to Microsoft’s last-resort Extended Security Update (ESU) program. In all cases, both Microsoft and Rapid7 recommend upgrading to a newer version of Windows as soon as possible.
Windows 11 21H2: end of support, mostly
Windows 11 21H2 Home, Pro, Pro Education, Pro for Workstations, and SE also move past the end of support. No ESU program is available for Windows 11 client OS, so Windows 11 21H2 assets for the editions listed above are insecure-by-default from now on. However, Windows 11 21H2 Enterprise and Education remain in general support until 2024-10-08. If you find this confusing, you are not alone.
Summary Charts
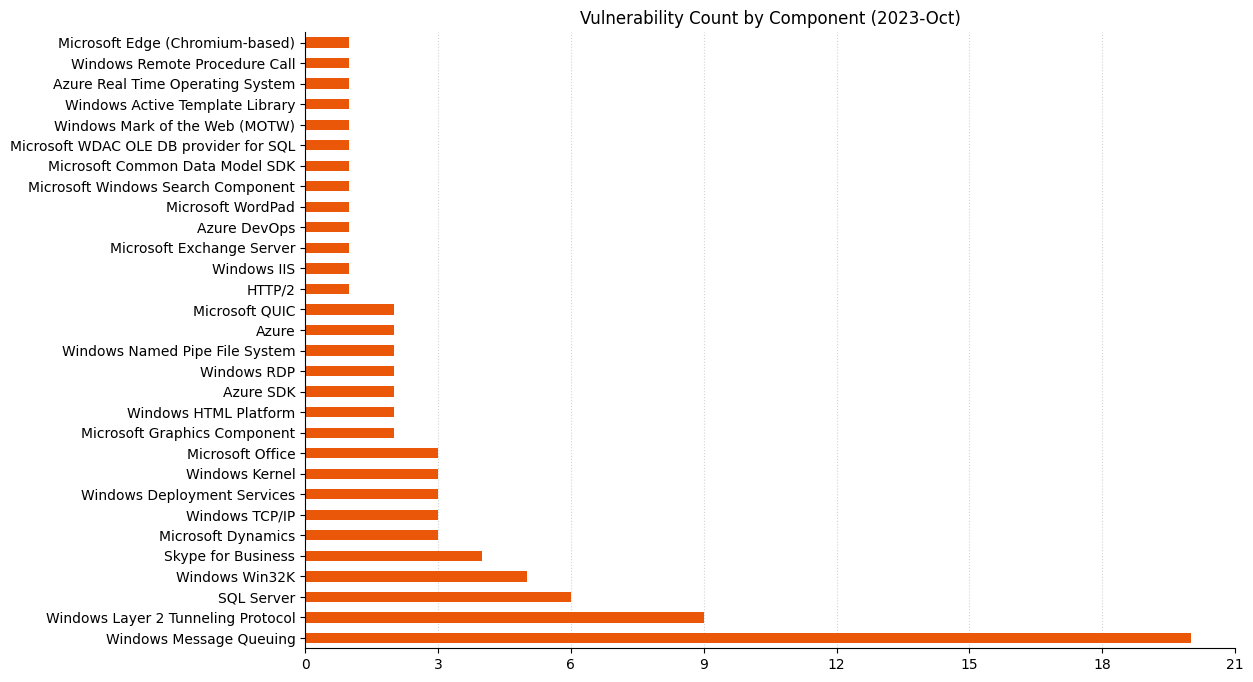
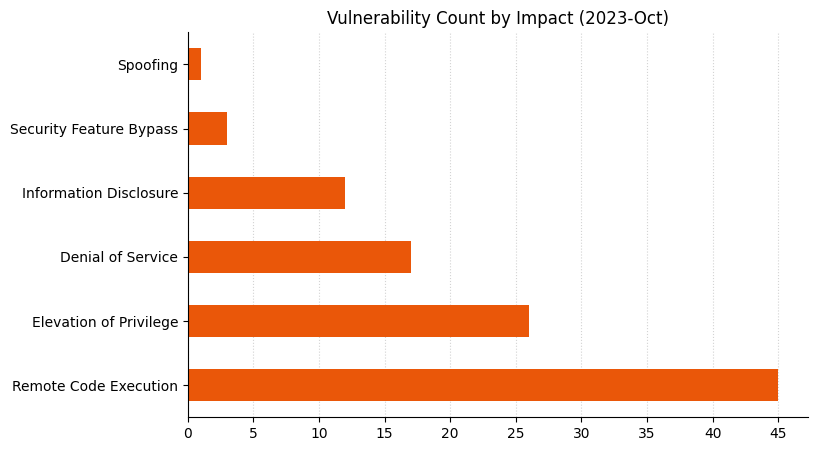
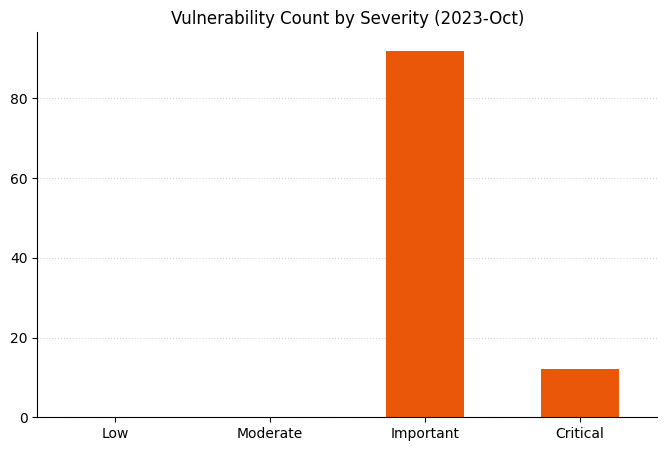
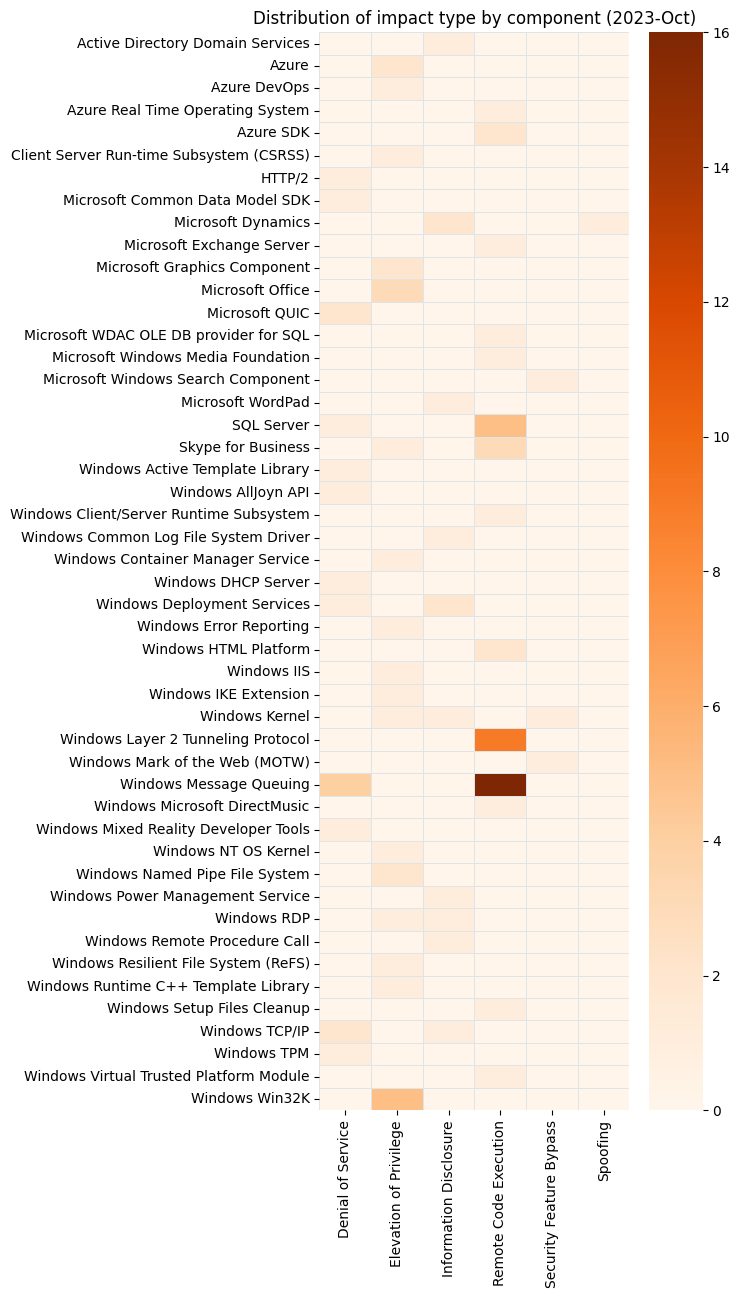
Summary Table
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36415 | Azure Identity SDK Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-36414 | Azure Identity SDK Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-36419 | Azure HDInsight Apache Oozie Workflow Scheduler Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-36418 | Azure RTOS GUIX Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36737 | Azure Network Watcher VM Agent Elevation of Privilege Vulnerability | No | No | 7.8 |
Azure Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36561 | Azure DevOps Server Elevation of Privilege Vulnerability | No | No | 7.3 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-5346 | Chromium: CVE-2023-5346 Type Confusion in V8 | No | No | N/A |
ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36790 | Windows RDP Encoder Mirror Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
Exchange Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36778 | Microsoft Exchange Server Remote Code Execution Vulnerability | No | No | 8 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36433 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-36429 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-36566 | Microsoft Common Data Model SDK Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-36416 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 6.1 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36569 | Microsoft Office Elevation of Privilege Vulnerability | No | No | 8.4 |
| CVE-2023-36789 | Skype for Business Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-36786 | Skype for Business Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-36780 | Skype for Business Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-36565 | Microsoft Office Graphics Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36568 | Microsoft Office Click-To-Run Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-41763 | Skype for Business Elevation of Privilege Vulnerability | Yes | Yes | 5.3 |
SQL Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36417 | Microsoft SQL ODBC Driver Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36730 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36785 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36420 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36728 | Microsoft SQL Server Denial of Service Vulnerability | No | No | 5.5 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36704 | Windows Setup Files Cleanup Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36711 | Windows Runtime C++ Template Library Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36725 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36723 | Windows Container Manager Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-41772 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36557 | PrintHTML API Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36729 | Named Pipe File System Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36718 | Microsoft Virtual Trusted Platform Module Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36701 | Microsoft Resilient File System (ReFS) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36603 | Windows TCP/IP Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36720 | Windows Mixed Reality Developer Tools Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36709 | Microsoft AllJoyn API Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36605 | Windows Named Pipe Filesystem Elevation of Privilege Vulnerability | No | No | 7.4 |
| CVE-2023-36902 | Windows Runtime Remote Code Execution Vulnerability | No | No | 7 |
| CVE-2023-38159 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36721 | Windows Error Reporting Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36717 | Windows Virtual Trusted Platform Module Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-36707 | Windows Deployment Services Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-36596 | Remote Procedure Call Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-36576 | Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-36698 | Windows Kernel Security Feature Bypass Vulnerability | No | No | 3.6 |
Windows Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-38171 | Microsoft QUIC Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36435 | Microsoft QUIC Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-44487 | MITRE: CVE-2023-44487 HTTP/2 Rapid Reset Attack | Yes | No | N/A |
Windows ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36434 | Windows IIS Server Elevation of Privilege Vulnerability | No | No | 9.8 |
| CVE-2023-35349 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-36577 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-41765 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-41767 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-41768 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-41769 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-41770 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-41771 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-41773 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-41774 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-38166 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-36710 | Windows Media Foundation Core Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36436 | Windows MSHTML Platform Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36712 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36726 | Windows Internet Key Exchange (IKE) Extension Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36594 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-41766 | Windows Client Server Run-time Subsystem (CSRSS) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36732 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36731 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36743 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36598 | Microsoft WDAC ODBC Driver Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36593 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36702 | Microsoft DirectMusic Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-36438 | Windows TCP/IP Information Disclosure Vulnerability | No | No | 7.5 |
| CVE-2023-36602 | Windows TCP/IP Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36567 | Windows Deployment Services Information Disclosure Vulnerability | No | No | 7.5 |
| CVE-2023-36606 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36581 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36579 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36431 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36703 | DHCP Server Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36585 | Active Template Library Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-36592 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36591 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36590 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36589 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36583 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36582 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36578 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36575 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36574 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36573 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36572 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36571 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36570 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.3 |
| CVE-2023-36776 | Win32k Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-36697 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2023-36564 | Windows Search Security Feature Bypass Vulnerability | No | No | 6.5 |
| CVE-2023-29348 | Windows Remote Desktop Gateway (RD Gateway) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-36706 | Windows Deployment Services Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-36563 | Microsoft WordPad Information Disclosure Vulnerability | Yes | Yes | 6.5 |
| CVE-2023-36724 | Windows Power Management Service Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-36713 | Windows Common Log File System Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-36584 | Windows Mark of the Web Security Feature Bypass Vulnerability | No | No | 5.4 |
| CVE-2023-36722 | Active Directory Domain Services Information Disclosure Vulnerability | No | No | 4.4 |
Updates
- 2023-10-11: added detail about CVE-2023-36563 vulnerability location.
- 2023-10-11: expanded discussion of CVE-2023-44487 mechanism and risk.

