We're excited to announce that the AD CS Workflows MetaModule has officially moved from early access to general availability in Metasploit Pro! This powerful new feature represents a significant advancement in assessing and exploiting Active Directory Certificate Services (AD CS) misconfigurations, providing security professionals with an automated, comprehensive approach to identifying and leveraging six common AD CS vulnerabilities.
What is the AD CS Workflows MetaModule?
Active Directory Certificate Services is Microsoft's Public Key Infrastructure (PKI) solution within Active Directory environments. While AD CS provides essential cryptographic services, it's also frequently misconfigured, creating opportunities for privilege escalation and lateral movement that traditional security assessments often miss.
The AD CS Workflows MetaModule changes that by providing a sophisticated, step-by-step automated workflow that requires minimal configuration. With nothing more than a domain name and credentials, it will begin the process where by it:
- Discovers and analyzes AD CS infrastructure and certificate templates
- Identifies common misconfigurations across your AD CS deployment
- Exploits vulnerabilities to demonstrate real-world attack paths
- Generates comprehensive reports with detailed remediation guidance
Why AD CS Security Matters
- AD CS misconfigurations represent a significant but often overlooked attack vector in enterprise environments
- While traditional Active Directory attacks focus on compromising user accounts and exploiting group memberships, AD CS attacks target the certificate infrastructure itself to gain elevated privileges
- These attacks can be challenging to detect because they often appear as legitimate certificate issuance to standard monitoring systems.
- Traditional security tools are primarily designed to identify suspicious user behavior and failed authentication attempts, but may not flag certificate-based privilege escalation as anomalous activity
- Certificates can provide longer-term access compared to other credential types
- While compromised passwords can be reset and Kerberos tickets have defined expiration periods, certificates may remain valid for extended periods
- Many organizations have limited visibility into their AD CS configurations, and effective remediation often requires PKI expertise that may not be readily available within IT teams
Key Features and Capabilities
Intelligent Multi-Phase Assessment
The MetaModule follows a systematic five-step process:
- Environment Discovery: Connects to domain controllers and gathers essential AD CS infrastructure information
- Template Analysis: Identifies all certificate templates and authorities, analyzing each for exploitable misconfigurations
- Exploitation: Attempts to leverage discovered misconfigurations to issue certificates with elevated privileges
- Post-Exploitation: Uses issued certificates to perform configurable actions like obtaining Kerberos tickets or establishing LDAP sessions
- Comprehensive Reporting: Generates detailed reports with findings and remediation guidance
Flexible Configuration Options
The MetaModule provides extensive configuration flexibility:
- Target Specification: Work with domain FQDNs or specific domain controllers and certificate authorities
- Credential Integration: Use existing project credentials or specify new ones, including pass-the-hash capabilities
- Attack Selection: Enable or disable specific misconfiguration classes based on your assessment needs
- Post-Exploitation Actions: Choose between Kerberos Ticket-Granting-Ticket (TGT) acquisition or LDAP session establishment
Real-World Attack Simulation
The AD CS Workflows MetaModule provides practical demonstration of identified vulnerabilities by attempting actual exploitation rather than only theoretical assessment. When a misconfiguration is detected, the MetaModule attempts to issue certificates that demonstrate the level of access an attacker could obtain.
The post-exploitation capabilities show how issued certificates can be used for authentication. Depending on configuration, the MetaModule can obtain Kerberos TGTs for use with various services, or establish authenticated LDAP sessions that demonstrate administrative access levels. This approach helps clarify the practical impact of identified misconfigurations and provides concrete examples of the privileges that could be gained through exploitation.
How to Use the AD CS Workflows MetaModule
Getting started with the AD CS Workflows MetaModule is straightforward:
Prerequisites
- Metasploit Pro version 4.22.8-2025080401 or later
- Domain FQDN (e.g., corp.target.lan)
- Valid domain credentials (elevated privileges not required or recommended)
Access and Configuration
- Access: Navigate to Modules > MetaModules from the Project tab and launch the AD CS Workflows MetaModule
- Configure Scan Settings
- Enter your target AD domain's FQDN
- Optionally specify particular domain controllers or certificate authorities
- Set Credentials
- Use existing project credentials or enter new ones
- Optionally utilize pass-the-hash for authentication with NTLM hashes
- Select Attack Methods
- Choose which misconfigurations to exploit (all enabled by default)
- Configure post-exploitation actions based on your objectives
- Customize Reporting
- Select which report sections to include
- Generate comprehensive documentation of findings
Understanding Results
The MetaModule provides rich feedback through multiple interfaces:
- Real-time Statistics: View discovered certificate authorities, templates, and exploitation attempts as they happen
- Task Logging: Monitor detailed console output to understand current operations
- Comprehensive Reports: Get detailed findings with remediation guidance organized into logical sections
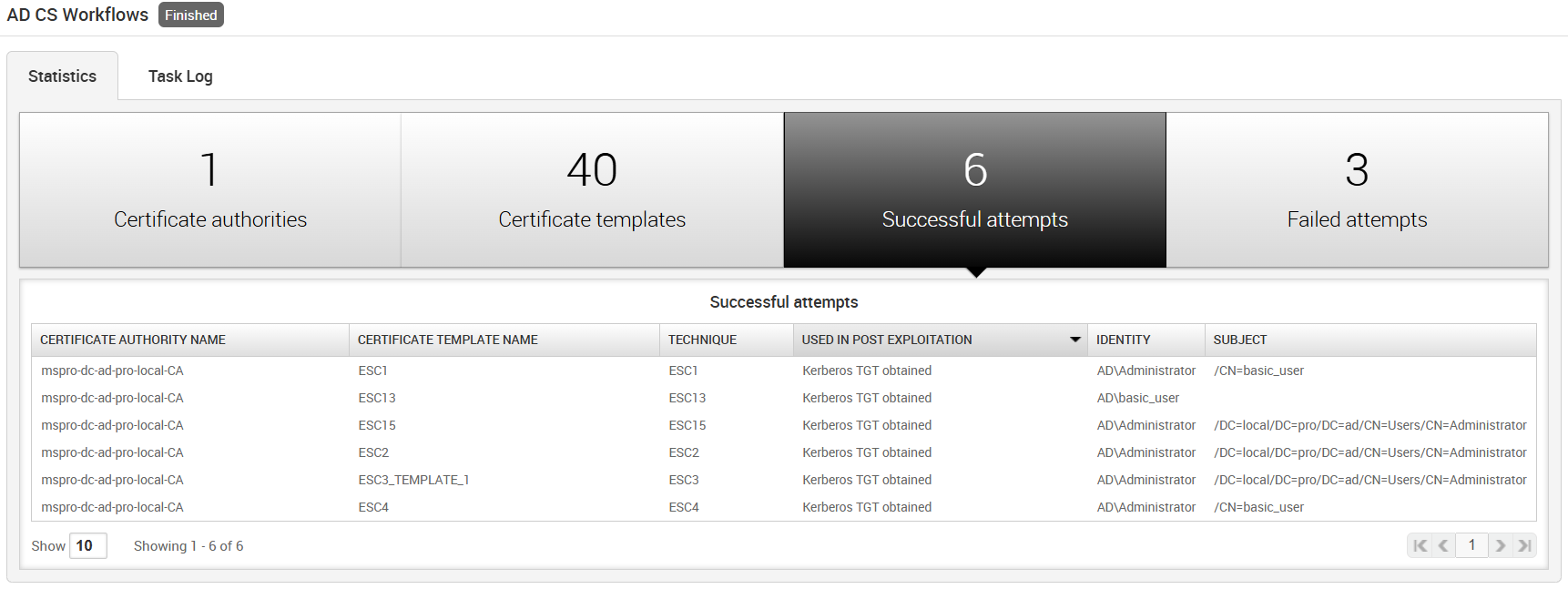
Statistics on which exploit attempts were successful.
What Makes This Feature Special
Actionable Intelligence
The AD CS Workflows MetaModule provides proof-of-concept exploitation to demonstrate identified vulnerabilities, along with detailed remediation steps for each misconfiguration. The generated reports include additional hardening recommendations and references to relevant research and documentation, providing guidance for both immediate fixes and broader security improvements.
Seamless Integration
Building this capability into Metasploit Pro allows for integration with existing security testing workflows. Certificates issued during assessments are stored in project credentials for use with other Metasploit modules. Sessions established during post-exploitation can be used with additional post-exploitation modules, and results integrate with existing reporting and analysis features.
Getting Started
The AD CS Workflows MetaModule is now available by default in Metasploit Pro version 4.22.8-2025080401 and later. This represents our commitment to making advanced security assessment capabilities accessible to all Metasploit Pro users.
Whether you're conducting penetration tests, vulnerability assessments, or security audits, the AD CS Workflows MetaModule provides the specialized capabilities needed to assess AD CS security posture and demonstrate real-world attack scenarios.
Learn More
Ready to enhance your Active Directory security assessments? The AD CS Workflows MetaModule is available now in Metasploit Pro. For detailed configuration instructions and comprehensive feature documentation, visit our AD CS Workflows MetaModule documentation.
