Vulnerable network access points are a potential gold mine for threat actors who, once inside, can exploit them persistently. Many cybercriminals are not only interested in obtaining personal information but also seek corporate information that could be sold to the highest bidder.
Infiltrating corporate networks
To infiltrate corporate networks, threat actors typically use several techniques, including:
Social engineering and phishing attacks
Threat actors collect email addresses, phone numbers, and information shared on social media platforms to target key people within an organization using phishing campaigns to collect credentials. Moreover, many threat actors managed to find the details of potential victims via leaked databases posted on dark web forums.
Malware infection and remote access
Another technique used by threat actors to gain access to corporate networks is malware infection. This technique consists of spreading malware, such as trojans, through a network of botnets to infect thousands of computers around the world.
Once infected, a computer can be remotely controlled to gain full access to the company network that it is connected to. It is not rare to find threat actors with botnets on hacking forums looking for partnerships to target companies.
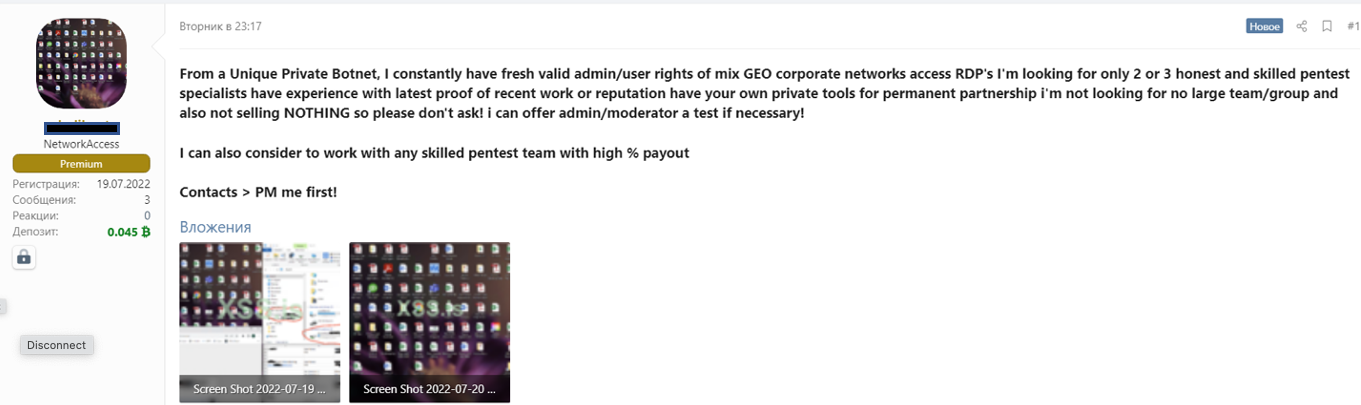
Network and system vulnerabilities
Some threat actors will prefer to take advantage of vulnerabilities within networks or systems rather than developing offensive cyber tools or using social engineering techniques. The vulnerabilities exploited are usually related to:
- Outdated or unpatched software that exposes systems and networks
- Misconfigured operating systems or firewalls allowing default policies to be enabled
- Ports that are open by default on servers
- Poor network segmentation with unsecured interconnections
Selling network access on underground forums and markets
Since gaining access to corporate networks can take a lot of effort, some cybercriminals prefer to simply buy access to networks that have already been compromised or information that was extracted from them. As a result, it has become common for cybercriminals to sell access to corporate networks on cybercrime forms.
Usually, the types of access that are sold on underground hacking forums are SSH, cPanels, RDP, RCE, SH, Citrix, SMTP, and FTP. The price of network access is usually based on a few criteria, such as the size and revenue of the company, as well as the number of devices connected to the network. It usually goes from a few hundred dollars to a couple thousand dollars. Companies in all industries and sectors have been impacted.
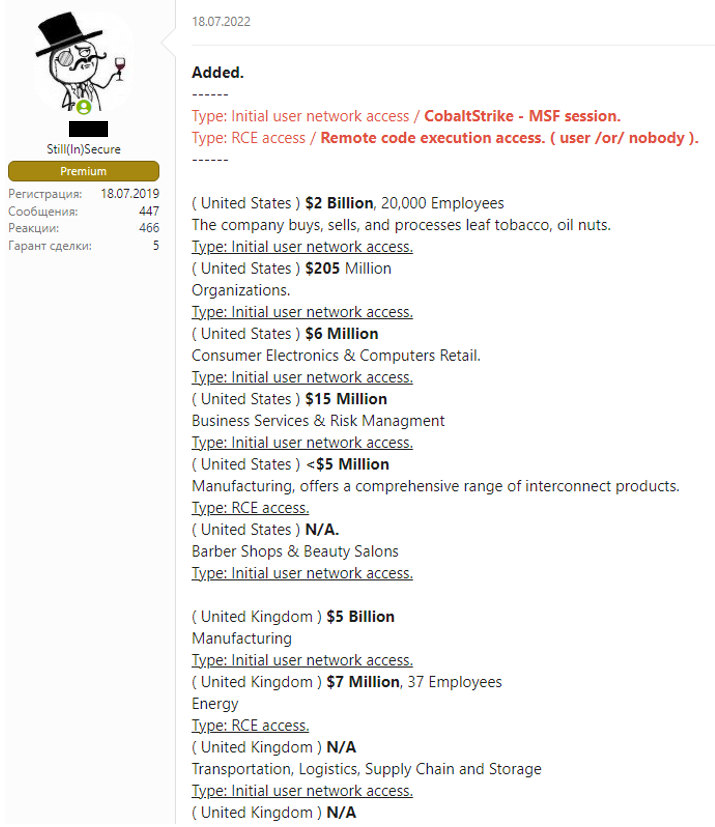
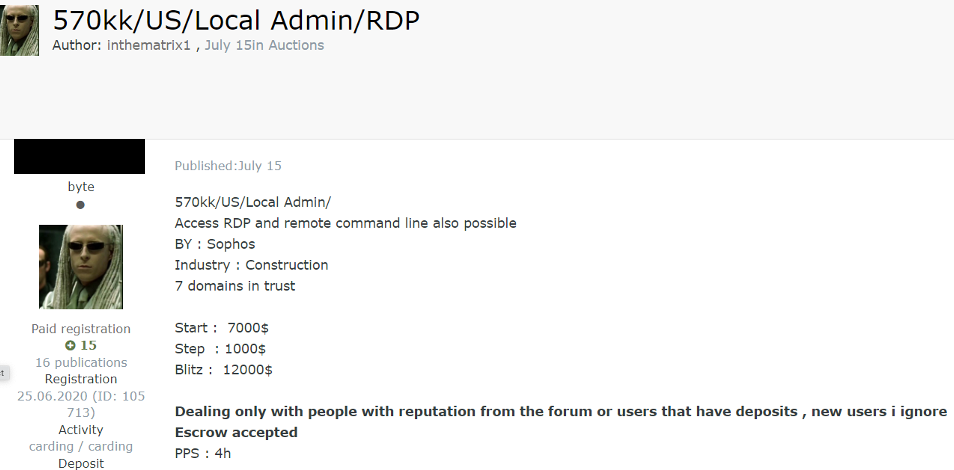
For these reasons, it is increasingly important for organizations to have visibility into external threats. Threat intelligence solutions can deliver 360-degree visibility of what is happening on forums, markets, encrypted messaging applications, and other deep and darknet platforms where many cybercriminals operate tirelessly.
In order to protect your internal assets, ensure the following measures exist within the company and are implemented correctly.
- Keep all systems and network updated.
- Implement a network and systems access control solution.
- Implement a two-factor authentication solution.
- Use an encrypted VPN.
- Perform network segmentation with security interfaces between networks.
- Perform periodic internal security audit.
- Use a threat intelligence solution to keep updated on external threats.
Additional reading:
- 360-Degree XDR and Attack Surface Coverage With Rapid7
- To Maze and Beyond: How the Ransomware Double Extortion Space Has Evolved
- ISO 27002 Emphasizes Need For Threat Intelligence
- For Finserv Ransomware Attacks, Obtaining Customer Data Is the Focus
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe