If your company processes credit card transactions, you must be compliant with the Payment Card Industry Data Security Standard, or PCI DSS. Any entity that stores, processes, or transmits cardholder data must abide by these requirements, which provide best practices for securing your cardholder data environment (CDE).
Rapid7 InsightVM, InsightAppSec, and Metasploit have been designed to directly help your team meet PCI DSS, as well as comply with many other compliance standards. Rapid7 InsightIDR, our cloud SIEM, was created by security responders to help you detect common and targeted cyber-threats while meeting multiple PCI requirements. This includes the centralized log management mandated in Requirement 10: Tracking and monitoring all access to network resources and cardholder data.
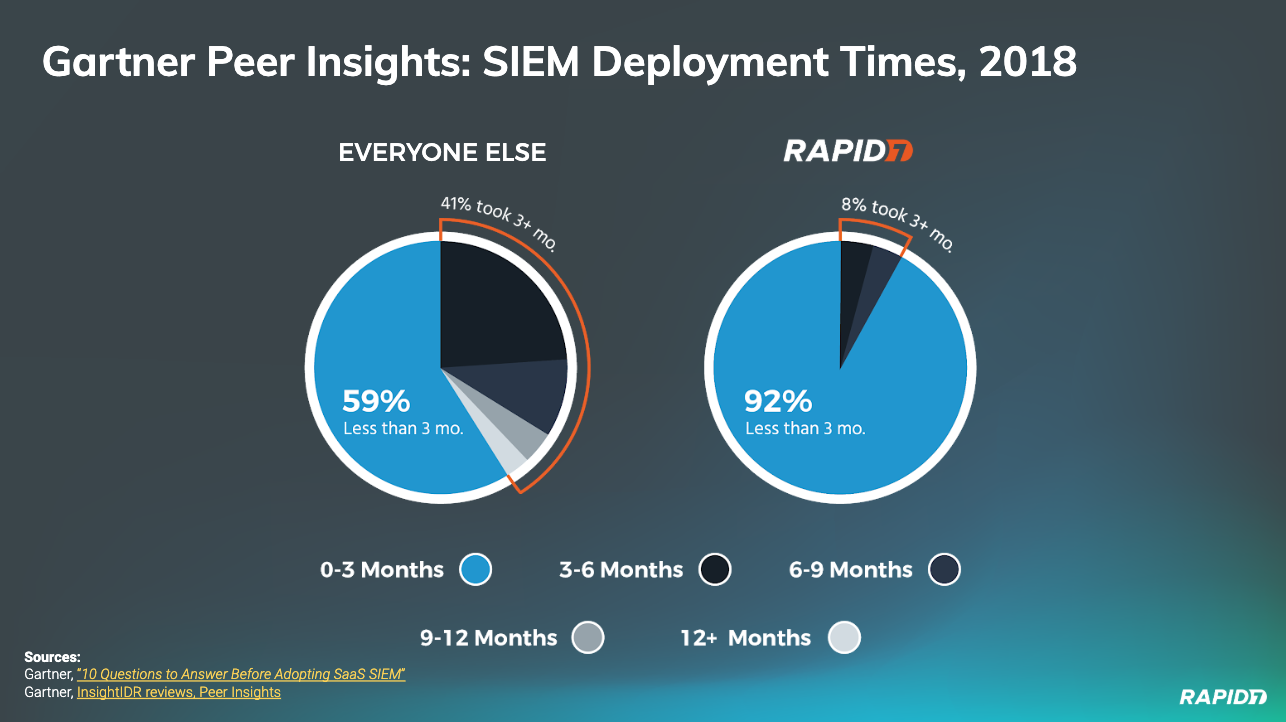
Unlike most SIEMs, which only collect data for reporting and “look-back-in-time” investigations, InsightIDR keeps you compliance-ready while providing your team modern threat detection and response capabilities. Backed by Rapid7 SOC detections, community threat intel sharing, and future-ready data collection, InsightIDR breaks the traditional mold of legacy SIEM while boasting the fastest deployment times in the industry.
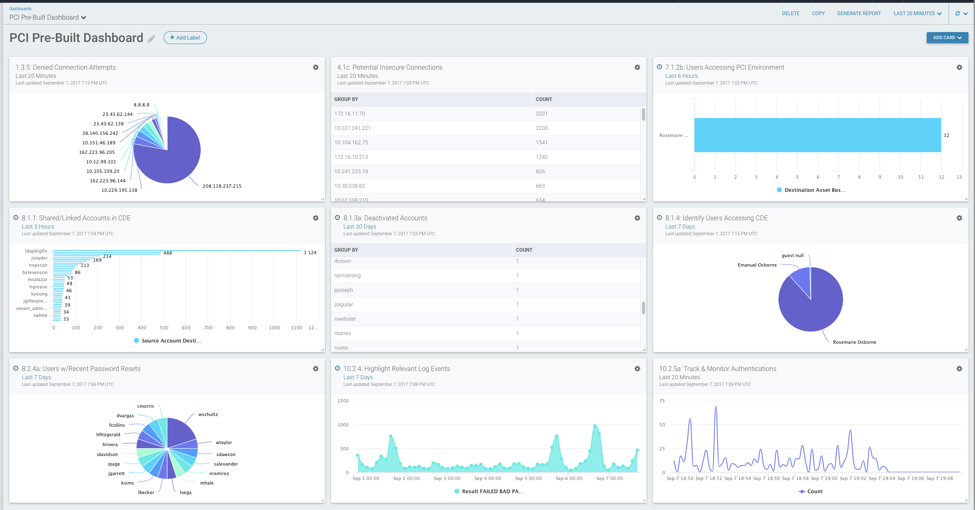
Here are a few of the PCI requirements that InsightIDR can help security teams manage, ranging from monitoring access to your CDE and exposing risky user behavior, to fast and comprehensive incident investigations across your modern network.
Here’s a specific breakdown by PCI DSS 3.2.1 requirement:
PCI DSS Requirements 3.2.1 Review
| Requirement No. | Compliance Requirement | How InsightIDR Helps Support |
|---|---|---|
| 3.5 | Protect cardholder data: Document and implement procedures to protect keys used to secure stored cardholder data against disclosure and misuse. | The included Insight Agent with InsightIDR helps you detect and respond to attacks across Windows, Mac, and Linux assets. InsightIDR supports file integrity monitoring and can be used to monitor key and credential files on critical assets. |
| 6.4.1 | Develop and maintain secure systems and applications: Separate development/test environments from production environments and enforce the separation with access controls. | InsightIDR helps validate that your access control policies are being properly enforced. You can monitor multiple separated environments, define specific zones, and be alerted if access policies are violated. For example, you could set a policy that no users in the “developers” group should access the network zone “PCI Production,” and you’ll be notified of any violations.InsightIDR helps validate that your access control policies are being properly enforced. You can monitor multiple separated environments, define specific zones, and be alerted if access policies are violated. For example, you could set a policy that no users in the “developers” group should access the network zone “PCI Production,” and you’ll be notified of any violations. |
| 7.1, 7.3 | Implement strong access control measures: Limit access to system components and cardholder data to only those individuals whose jobs require such access. | After flagging systems in your CDE as restricted assets, InsightIDR will alert you on any change in behavior. This includes suspicious authentications, users with unexpected privilege escalations, and even approved users remotely accessing the CDE from a new source asset. This detects unauthorized access, risky behavior, and enforces policies set by your security team. |
| 8.1, 8.2.4, 8.5 | Identify and authenticate access to system components: Ensure proper user identification management for non-consumer users and administrators. Change user passwords / passphrases at least once every 90 days. Do not use group, shared, or generic IDs, passwords, or other authentication methods. | InsightIDR exposes risky user behavior, including shared accounts, unknown administrators, and non-expiring passwords. This visibility into user behavior across your network helps enforce your set security policies. In addition, InsightIDR alerts on password brute forcing, pass-the-hash, and other credential-based attacks by running behavior analytics on event logs and through included deception technology, which includes honeypots, honey users, and honey credentials. |
| 10.1, 10.2, 10.3, 10.5, 10.6, 10.7 | Track and monitor access to network resources and cardholder data: Implement automated audit trails. Record audit entries; secure the audit trail. Use file-integrity monitoring (10.5.5). Review logs of all critical system components. Review logs of all components that perform security functions. Retain audit trail for at least one year, with three months readily accessible for analysis. | InsightIDR comes with cloud-native data collection, a powerful search, and pre-built compliance dashboards to help you solve Requirement 10 and give you visibility across your modern network. With your standard InsightIDR subscription, all ingested logs are stored for one year (three months fully accessible in “hot storage” and nine months in “cold storage”). With our Managed Detection and Response service offering, your logs are retained for audit, compliance, and search for 365 days in hot storage. As a cloud SIEM, data retention across InsightIDR and MDR can be tailored to exactly meet your business and compliance needs. |
| 11.4, 11.5 | Test security systems and processes: Use intrusion detection and/or prevention techniques to detect and/or prevent intrusions into the network. Deploy a change-detection mechanism to alert personnel to unauthorized modification of critical files. | InsightIDR helps you detect phishing, malware, and the use of stolen credentials, the three most common attacker behaviors behind breaches. InsightIDR also comes with threat intelligence management and fully integrates with your existing firewalls and Intrusion Detection/Prevention Systems (IDS/IPS). Logs from IDS/IPS systems are made fully searchable for investigations and audit. InsightIDR comes with file integrity monitoring, which can be used to detect modifications to critical system files, configurations, and content. |
| 12.5.2, 12.10 | Maintain an information security policy: Monitor and analyze security alerts and information, and distribute to appropriate personnel. Implement an incident response plan. Be prepared to respond immediately to a system breach. | InsightIDR comes with case management and incident investigation capabilities, including log search, endpoint interrogation, and easy access to user behavior data. Alerts from your existing network and security tools can be fed into InsightIDR and then distributed to teams via email, ticketing systems, or chat tools like Slack. InsightIDR is built for modern threat detection and response and assists from initial detection to containment. Built-in automation in InsightIDR helps teams quarantine potentially compromised users immediately and initiate response plans within seconds of detecting threats. |