Why worry about unauthorized DNS servers?
DNS remains a vital part of computer networking. The foundation of DNS was laid in 1983 by Paul Mockapetris, then at the University of Southern California, in the days of ARPAnet, the U.S. Defense Department research project that linked computers at a small number of universities and research institutions ultimately led to the internet. The system is designed to work like a telephone company’s 411 service: given a name, it looks up the numbers that will lead to the bearer of that name.
DNS was never designed as a very secure protocol, and it is a popular target for attackers. There are two ways DNS can be hacked: by using protocol attacks (attacks based on how DNS is actually working) or by using server attacks (attacks based on the bugs or flaws of the programs or machines running DNS services).
One of the more infamous protocol attacks was the DNSChanger malware. It typically worked by changing DNS server settings on infected computers, allowing attackers to route internet traffic through malicious servers and intercept sensitive information. There was also a similar variant targeting Apple Mac computers dubbed OSX/MaMi, an unsigned Mach-O 64-bit executable.
In both of these cases, the attackers changed your DNS server from 8.8.8.8 (Google), for example, to one of their own DNS servers. Most of your DNS queries will be handled correctly, and you will get correct IP addresses. However, for certain sites (like banking), the attackers would direct you to a mocked-up website that looks like a valid banking one. Your login details would be captured once you start to interact with the site and are then used to steal your money.
Detecting unauthorized DNS server use
A network traffic analysis solution should include both a DNS traffic decoder and a number of alerting features that you can use to track down unauthorized DNS server use. The image below shows an example of a DNS traffic decoder. Here, we can see how a solution can build up an inventory of all DNS servers and client queries to them:
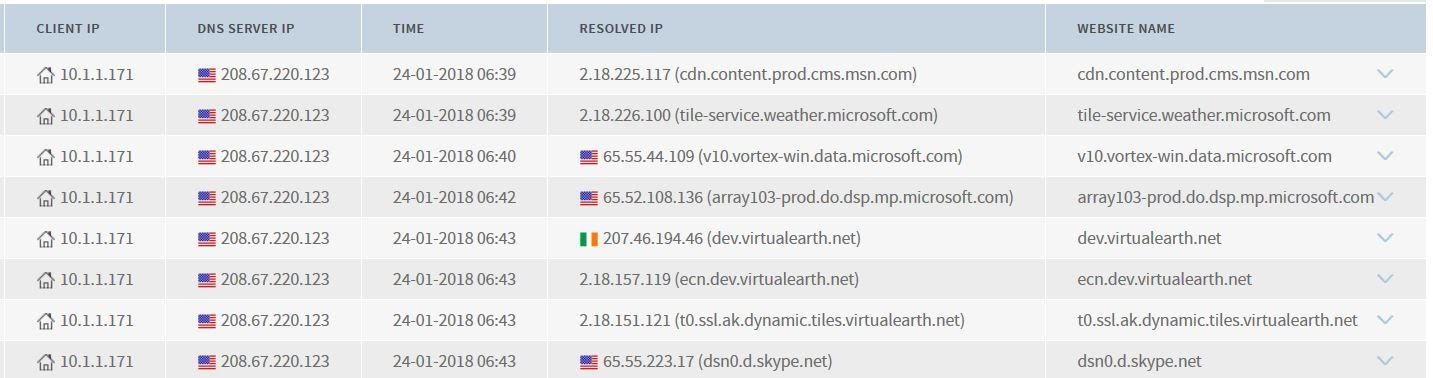
Having a DNS audit trail like this will also give you the data you need to investigate other DNS issues, such as cache poisoning.
How to generate alerts if a device uses an unauthorized DNS server
A network traffic tool can include a customizable alerting engine where you define whitelists of valid servers and get alerts if users try to access others. For the purposes of this example, assume we created a DNS whitelist containing these servers:
- 192.168.127.22 (hosted internally on network)
- 8.8.8.8 (google1)
- 8.8.4.4 (google2)
You’d then use the alerts configuration option to create a DNS alerting rule that will trigger if queries to other servers are detected. Once the unauthorized DNS server alert is triggered, a NTA tool will capture certain DNS metadata, like source and destination IP addresses, country where DNS server is registered, and the domain names that were queried.
These alerts can also be exported as SYSLOG so that they can be processed by a blocking device such as a firewall or Network Access Control (NAC) system.
How to monitor DNS traffic
One of the best ways to monitor DNS traffic is to port mirror traffic going to and from your local DNS servers and all internet traffic. Monitoring internet traffic is crucial so that you can pick up on devices using external DNS servers, so it is really easy to monitor network traffic on your network. Most managed switches support SPAN or mirror ports. If you have a switch that does not have any traffic monitoring options there are many alternatives for SPAN ports. The video below shows the steps needed to monitor internet traffic and you should extend this to also monitor local DNS servers.