*This is the first in a three-part series discussing common threats, key data sources, and how the Rapid7 portfolio can help you secure cloud environments.
As organizations continue to shift more of their infrastructure and software into the cloud, security teams need to keep pace with developers and operations to stay ahead of potential attackers. The first step in protecting cloud environments and users is visibility. Cloud logs provide the best insight into activity and potential threats, but these logs are often new territory for security teams and can be challenging to configure and contextualize into actionable data.
In this post we’ll review logging considerations for Microsoft Azure environments, as well as the new integrations and detections available in Rapid7’s cloud SIEM, InsightIDR, to support threat detection in the cloud.
Understanding Azure Logging: Categories to Know About
Azure logs are organized into three categories:
- Control/management logs, or Azure activity logs, provide information on Azure Resource Manager (ARM) activity—the homebase for Azure resource policy management. These logs are primarily administrative or audit-related activities within Azure.
- Data plane logs, or Azure diagnostic logs, which provide information about Azure resource usage. These are logs generated from day-to-day operations of Azure applications and services.
- Processed events logs, which provide information on events that have already been analyzed by Azure in some way. This includes Azure Security Center data.
Within each of these broad categories there are dozens, if not hundreds, of logs that are generated. However, in the hierarchy of log data that will be most useful and actionable in detecting attackers as early as possible in the attack chain, a few key logs stand out to prioritize, including:
- Azure Active Directory reporting logs are among the most important logs to track. They contain critical information about user sign-in activity, which is imperative to track in order to understand who is accessing your Azure environment at any given time. This would include sign-in activity for Azure applications such as Office 365, SharePoint, and OneDrive.
- Azure Monitor activity logs provide insight into Azure Resource Manager activity. Anything you do in the Azure portal (or leverage PowerShell to complete) likely goes through ARM, and those actions are sent to these activity logs. This would include things like provisioning an object, standing up a new virtual machine, changing Azure permissions, etc.
- Azure Security Center alert logs offer insight into alerts that Microsoft has generated based on events that it has processed. Relaying these alert logs into your SIEM as another source of threat detection is really important.
Logs from Office 365 (administrative and user activity) can also be collected through an Office 365 Management Activity API. While this consolidation is useful, logs relayed through this API can be delayed 3-5 days. As such, Azure AD appears to be a more timely source of Office 365 information.
As you work through understanding the logs that are relevant to monitor for your environment, there are a few important considerations:
- Turn logging on: While some of these logs are enabled by default, others may need to be explicitly configured. This will also vary based on your subscription tier. If there are logs you think you are tracking or know you want to track, it’s important to make sure logging is enabled and confirm the relevant objects are being captured in the logs.
- Centralize to Event Hubs: There are also different ways to push this data to other systems that may vary by logs. For example, exporting logs to Event Hubs is sometimes offered via an export feature, sometimes via a data export setting, and sometimes it might be a checkbox as you’re configuring the log.
- Check your subscription: Available data from Azure will vary by subscription. Access to Azure Security Center, for example, is not included in all subscriptions. While there’s some valuable information available in Security Center, if your subscription doesn’t include this option, you will not have access to this data. Also, Azure Active Directory Signin and Audit logs require P1 or P2 subscription at a minimum to start.
Once you’ve configured your logs, you’re ready to begin pushing this data into your SIEM. Event Hubs (Azure’s data streaming and event ingestion service) is a handy resource to consolidate logs to export to your SIEM. Again, these are configurable at the individual log level.
Azure Threat Detection in Rapid7’s SIEM, InsightIDR
Rapid7 SIEM ingests logs from Event Hubs to consolidate Azure data alongside the other relevant data from across your network (e.g., other cloud data, application data, or logs from on-premises systems).
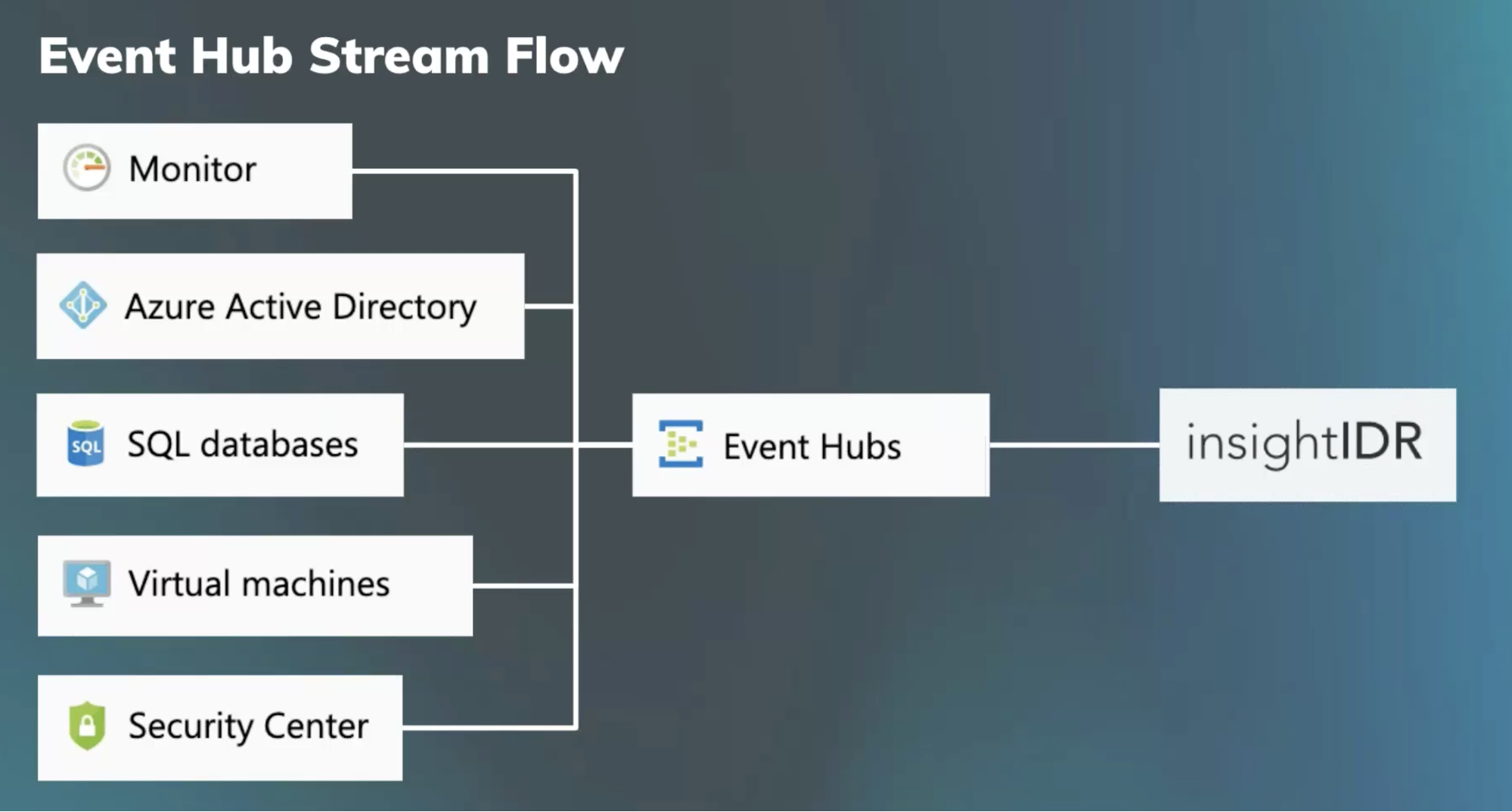
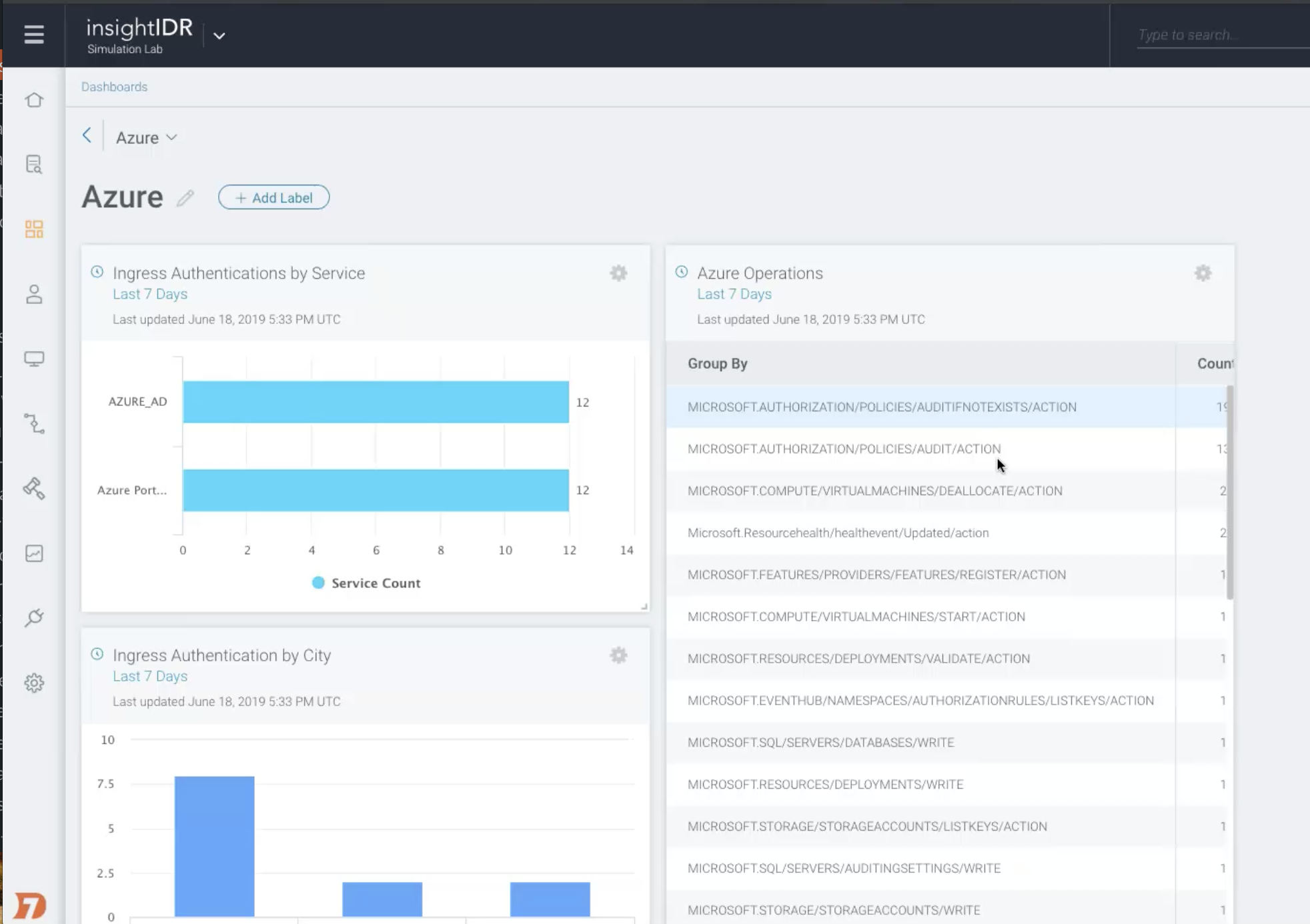
From there, InsightIDR applies User Behavior Analytics to Office 365 and Azure Active Directory data for threat detection and alerting on potential attacks based on things like suspicious Multi-Country Authentications. If your Azure subscription includes Security Center, those will come through Azure Monitor service (no additional configuration required). Also, any additional Azure data sources that can centralize into Event Hubs (like SQL database logs and virtual machine logs) can be searched, visualized, and reported on via our log search and custom rules features.
Takeaways
Centralized visibility of cloud users and anomalous account activity detections are critical for advancing security in the cloud. Stay tuned for the next post in this series, where we’ll look at key considerations in protecting AWS environments and how InsightIDR can help with Azure cloud security.
