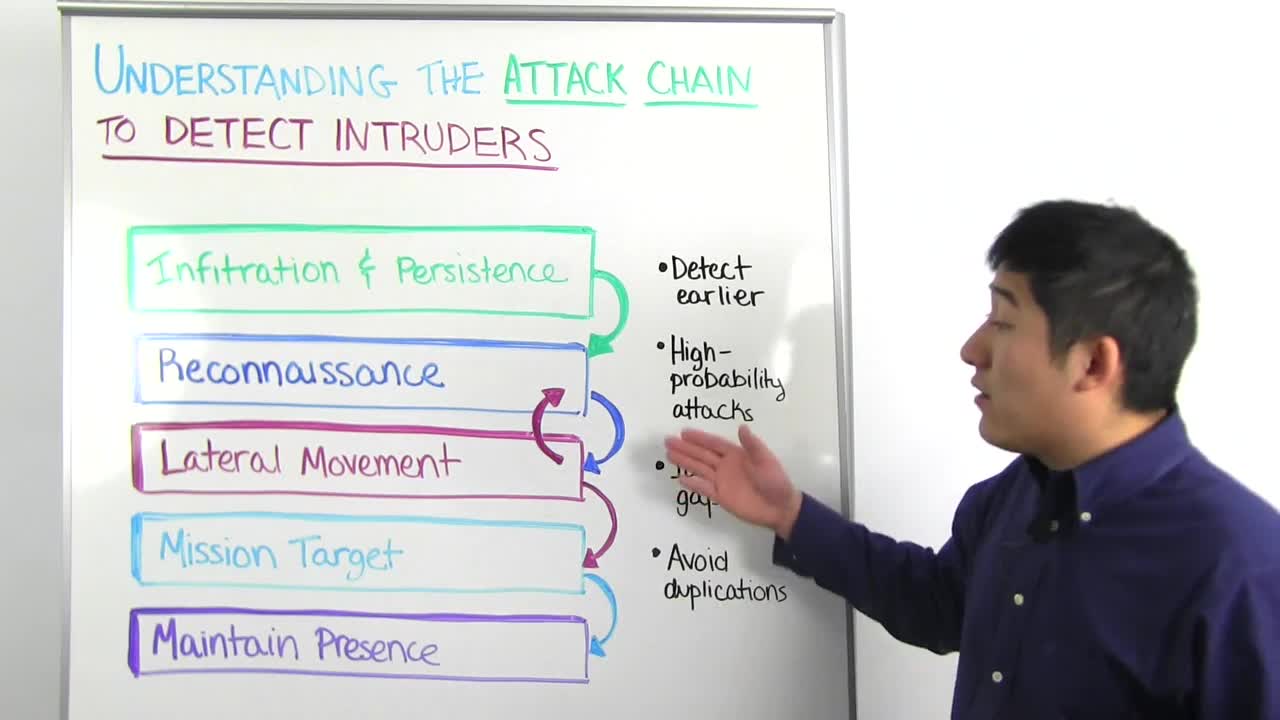
For any and every breach, intruders must take one or more of these steps during their attack. This includes credential based attacks where attackers steal usernames and passwords and use them to impersonate as company users, malware, and vulnerability exploits. Let's delve a bit into each step.
During infiltration and persistence, attackers work to get an initial foothold on the network. This is accomplished through phishing attacks, using third party leaked credentials, Adobe or Ashley Madison come to mind, or malware such as keyloggers or RAM scrapers. Once on the network intruders will deploy backdoors so they have continued access to the compromised asset.
After compromising their first target. they will move to reconnaissance and plan their next targets. This can be done through network scans using tools like Nmap, Active Directory enumeration, and other built-in Windows tools. The goal here is to identify vulnerable machines and attempt lateral movement moving from one endpoint to another.
During lateral movement, the attacker uses compromised credentials to access other machines. The objective here is to obtain a domain administrator credential which can then be used to sign on any machine on the network. In order to do this, they may use a stolen credential and try it on every machine on your network. If it succeeds on any of these endpoints the attacker will log in, scrape the password hashes or even the clear text credentials off of the machine, pass the hash to another endpoint, perform reconnaissance, rinse and repeat.
Mission target is your data with significant monetary value. This could be financials, credit card data, protected health information, your proprietary secret sauce. Once accessed the next step is to exfiltrate the data, often done through a Cloud service or FTP set up by the attacker.
The final step is maintaining presence, deploying backdoors across the network so even if Patient Zero the initial compromised asset is properly remediated there are still ways the attacker can enter again.
The Ponemon Institute reports the average length of a breach in financial services is 98 days and 197 days for retail. Attackers are consistently overstaying their welcome. If you can detect, investigate and remediate an attack earlier in the chain, you can stop the intruder before data theft is lost.
Here are four Rapid7 best practices to help with your security planning. Detect earlier in the attack chain. While it's important to identify when there's unauthorized access to your critical assets, it isn't ideal because if they're attackers they're already at mission target. Prioritize detecting initial infiltration and reconnaissance.
Focus on high probability attacks. According to the Verizon data breach investigation's report, the top three vectors behind breaches are compromised credentials, malware, and phishing. This leads into identifying gaps in your security program. Do you have the people, process and technology in place to detect earlier in the chain? For example, many of us have detection in place for malware, but it's also important to detect compromised credentials and phishing.
Finally, evaluate the reasons behind your security initiatives. By avoiding duplications and prioritizing based on the attack chain, you can avoid overspending and applying a scattershot approach that leaves notable gaps.
If you'd like to learn more about the attack chain, we have an on-demand webcast that delves further into each step. We also show our user behavior analytics solution, InsightIDR, which helps detect stealthy attacks like compromised credentials and lateral movement, accelerates incident investigations, and exposes risky user behavior from endpoint to Cloud. From the Metasploit project and Rapid7 global services, we've applied our knowledge of the attacker to help you detect earlier in the attack chain without the burden of digging through logs, parsing through false positives and tracing your users across assets, IPs, and services. For more on InsightIDR, check out our product page for a five-minute demo video.
That's it for this week's Whiteboard Wednesday. Looking forward to seeing you again soon