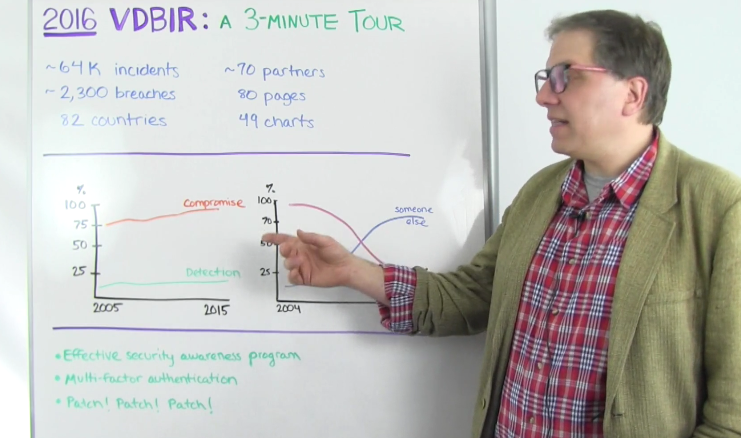
So we start our tour with what I believe to be the singular metric you should be tracking in your organization, the detection deficit. Verizon has tracked this metric for nine years, and it tells a sad, sad story. So what is the detection deficit? This chart tracks the percentage of breaches where attackers are able to accomplish their goals of pretty much getting what they want in days or less. Then it presents it with a percentage of breaches where defenders were able to stop them. Now we have a slightly modified version of this chart on our community blog, community.rapid7.com, but it tells the same basic tale. Attackers are becoming more efficient and successful, while defenders are barely keeping pace.
So why is this the most important metric? Now if you swap out 'breach' for 'components of the kill chain', track how quickly attackers reached each of those seven stages, and how quickly your defenders caught and stopped them per stage. Hopefully you'll find that it takes attackers much longer to get to each stage than it does for you to find them. But if the data shows that there are gaps in your response, this is a great stepping stone to help identify areas for improvement in your organization. Rapid7's InsightIDR, Incident Response, and Analytic Response teams are developing tools that you can use to help track these metrics. But you don't have to wait for that. You can get started right now. Just capture the right data and start looking at it.
That takes us to the next stop on our tour though, which is, "Who really has your back when it comes to detecting these breaches?" And that we can point to this chart here. In Verizon's report, the data shows that defenders are doing a less than stellar job of identifying trouble in their own backyards. And they seem to be relying more on these third parties than they should be. So this seems to track pretty well with what we just saw in the detection deficit. If you were detecting issues yourself, you would probably not need people to detect them for you, and you'd do it faster. It emphasizes the need to make your log activity data more actionable. The quicker you can detect threats, the less likely it will be someone else telling you that you've been hacked. So look back at all the incidents and breaches you've had over the past year, see where you need better instrumentation and insight, and do your best to fix that.
We end our brief walkabout with our third and final tour stop, down at the wharf, and a focus on the deadly Dridex outbreak of 2015. And you now see why I'm a data scientist, and not a tour guide on one of Boston's duck boats. So Dridex is a banking trojan that involves phishing. We are at the wharf. It also involves endpoint malware drops, C2 deployments, and credential harvesting, which is then used against web applications en masse across the internet. Verizon mentions Dridex 13 times in the report, and is an unseen, but very prominent component of at least six of the charts in Verizon's report. And even if your organization size or industry was not a prominent target, the exposed vectors that Dridex exploited are important for all organizations to heed and develop controls around. So we should be crafting and delivering modern and effective awareness programs, migrating as much as you can to your multi-factor or risk-based authentication, and finding and eradicating the vulnerabilities that your adversaries are exploiting in your environment.
We cover more interesting waypoints in our series of posts on the Verizon Data Breach Investigations Report over at the Rapid7 community blog. Head on over there to discover more areas to explore in the report, and to make sure to hit us up with any questions or comments you have. And don't forget to sign up for our webinar next week, where we cover the Verizon Data Breach Investigations Report in more detail. Thank you