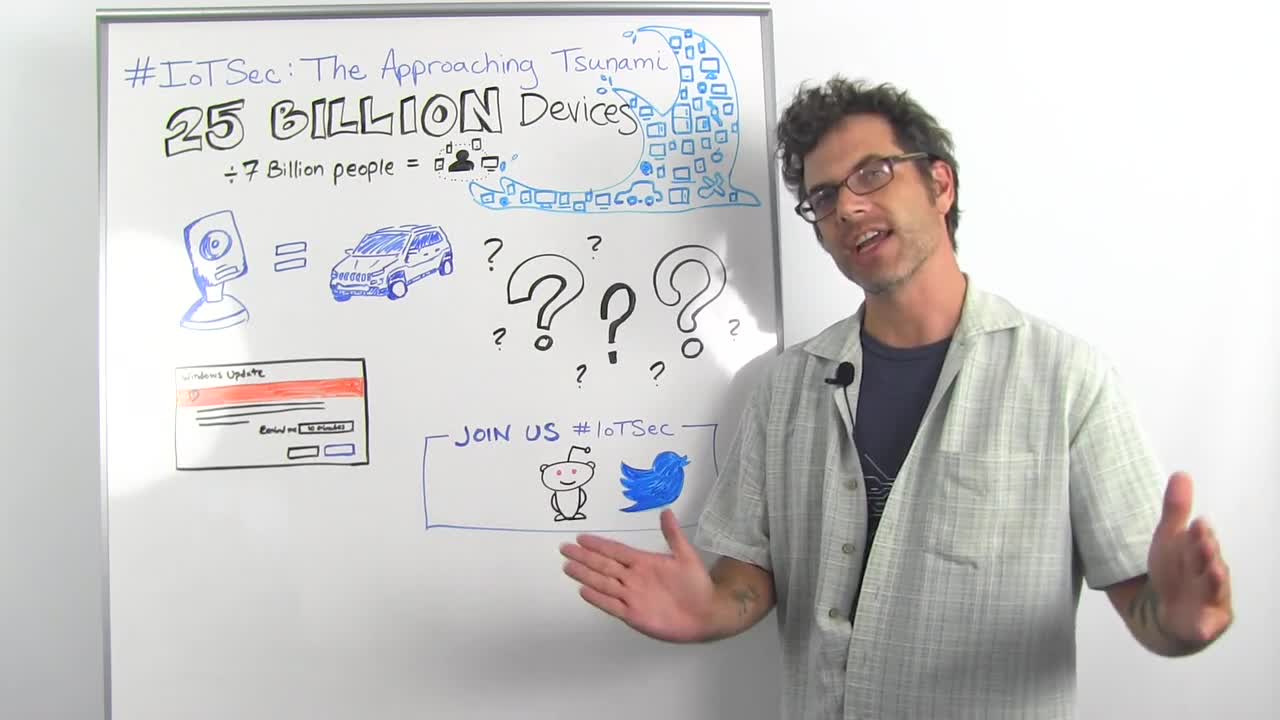
So this is all under the category of #IoTsec, and we're going to talk about the coming tsunami of IoT stuff. The Internet is expected to be host to about 25 billion of these devices by 2020, which is only five years from now from this recording, which is weird for me. That comes out to maybe three and a half to four devices for every human on Earth. We're no longer the dominant species. The dominant species are tiny computers that look like other things.
And so what we did was take a look at a pile of these video baby monitors. They look like this, and they have different form factors and all that. But you'll notice they don't look like computers, and they also don't look like cars. But they have lots of things in common with both.
But the deal is, is that with the baby monitors, we found that it would be informative to take a look at that segment, in particular, to get a sense of where IoT, Internet of Things, security is at, right now. And what we came out with was a pile of vulnerabilities that you saw, some not-so-great practices. And we found that there was a lot of question marks around, how are these built?
There's a lot of unknowns, like the supply chain that leads up to these devices, so you end up with a bunch of different components. You might have different chips, like System on a Chips. You have different operating systems that all basically boil down to Linux Kernels, sometimes VxWorks, and other things. And you have a lot of cloud services that the actual vendor of this device doesn't really have a whole lot of control over. We found that a lot too.
And this is exactly the same situation as you have in every other IoT thing. You see this in HVAC systems, you see it in thermostats, you see it in refrigerators that are ratting out your Google and Facebook credentials, for some reason. You see it in cars, you see it in airplanes. You see it in basically any hunk of electronics that has grafted onto it a real computer. It may not have a keyboard and monitor, but it is, in fact, a real computer with a CPU. It's got a network stack, it's got a bunch of cloud-backed services, and they are everywhere. They are surrounding us.
We're not there, yet. Don't get me wrong. We're like seven billion, six billion, right now, devices on the Internet that are not "computer" computers. But this is just growing, and it's growing exponentially. Who knows where it's going to be in 2025, say? Is it going to be 50 million? Is it going to be 100 million? Who knows?
The other big question is, how do you patch these things when they're out in the field? With the cloud-based services, you have a straight shot there, and that's good. You have one spot to patch. But when you have devices that have on-board vulnerabilities,... And these might be vulnerabilities that might be two or three or five years old by the time they get into your hands because it's just the way the supply chain works.
There's no happy Windows update, right. There's no automatic reminder. It's like, "Hey, you've got this update." I'm going to go check. In my mind, that's a massive problem. We've found that people just don't patch, unless you turn on some automatic patching mechanism. And that patching mechanism itself has to be safe and secure and reliable and all that.
So that's the state where we're at now, is where we have this giant pile of devices that no one super knows how they're made, and we don't know how to patch them out when they're out in the field. And that's a bummer, and so we're going to bum each other out on Reddit at a IMA Question/Answer with me and Mark Stanislav. Again, he did almost all of this research. I did very little on this. And we're going to be answering questions on Twitter on the #IoTsec.