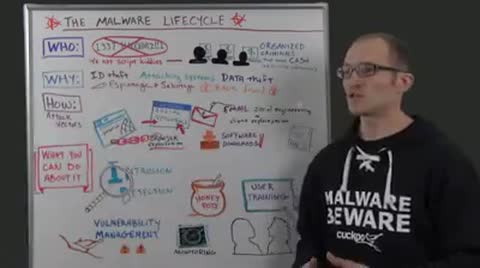
So historically, people have been just developing malware and attacking systems for showing their skills and for basically providing proof of concepts of certain techniques that they invented. But nowadays almost everything is financially motivated. So there are organized criminals behind it that have paid developers for putting these things together, and they come at your systems with a lot of resources.
So what is it they are actually after? So if they have infected your system, what kind of data do they steal? It could be, for example, just your name and your address, your personal data. So it would be a matter of identity theft, where they would use your name for registering some accounts and whatnot.
Another thing is they want to steal your data and your documents. It could be, for example, confidential documents from your work on your office computer, but it could also be personal pictures and stuff like that, that they could use in some way. So this leads to espionage cases and sabotage cases, where they are actually trying to steal ideas basically, intellectual property, and trying to manipulate, for example, some kind of device or manipulate your processes.
So one of the most important things in the last malware samples, malware families that we've seen is banking fraud. So they try to steal your bank account information, your credit card number, in order to just directly get money out of it.
There are different ways they actually can attack your systems and they can come into your systems, and this is also changing. So historically, it would be mostly computer worms that attack certain vulnerability and automatically spread to your system. This is not so prevalent nowadays. It's mostly nowadays about web browsers getting exploited. So if you visit a website and you have a browser that is maybe not up to date, or there's a vulnerability that has not been patched yet, then it can lead to automatically infecting your PC through some kind of exploit.
But it could also be that you are on a social network, and some friend sends you a link, "Hey, download this cool game." You just execute it because you think it's legit. Often cases, there is a lot of social engineering involved in these kind of attacks. So it could be a legit game, and it actually runs, but in parallel it's doing some malicious activity in the background.
Other things could be if you're maybe on your phone or also on the PC, if you just download something from a software market, and it somehow has some malicious activity also inside of it. So it could be a Trojan that grants access to criminals to your PC, but it also could do the things that mentioned before.
This looks really grim, and there's a lot of bad stuff out there and a lot of different malware samples. It's a huge amount of malware samples each day that we see, and there's actually something you can do about it. There are a lot of good guys that try to solve these problems and try to detect when some vulnerabilities are used or try to detect certain things on the network.
There are both open tools and also companies that can help you figure out where your priorities should be to solve these kinds of issues. You could, for example, leverage intrusion detection systems to see if your network is attacked or your computer is attacked. But you could also employ tools like honey pots, for example, which sit on your network, and they look vulnerable to malware, and so malware tries to infect them, but in reality, they just notify you that something's going wrong on your network, and then you can fix the problem.
A big thing, as I said, is social engineering aspect in the whole malware life cycle. That is pretty hard to solve, but if you employ the right user education and the right awareness training for your users and your company, or for maybe even friends, then this problem can get less and less big. It can be solved quite easily with educating your users.
Another thing to look out for is vulnerability management. You want to know what kind of problems you have on your systems. You want to know which attacks they are vulnerable to and maybe also what attack vectors are most important to your company or to your personal way of dealing with computers. This is one thing, for example, that Rapid7 is devoted to.
Another thing is, when you come across a malware sample and you want to know what it actually does, maybe what kind of files does it access, which kind of host it talks to, then you can employ tools like a malware analysis sandbox, which one example of it would be Cuckoo Sandbox, which is an open source tool that you can just download from the Web and use it to find out what a malware sample does. If you're interested in that kind of stuff, you should definitely contact us, and we will try to help you out with figuring out what to do.
So thank you for joining for this Whiteboard Wednesday, and talk to you soon.