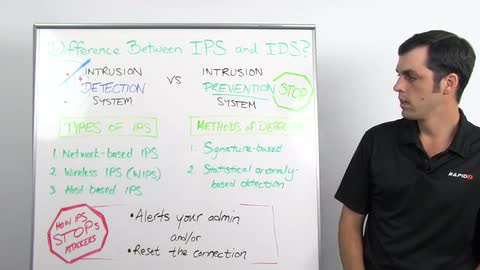
An IDS is an Intrusion Detection System. It's going to work to monitor the systems in a network traffic in your network and alert you based on suspicious activity. Now, an Intrusion Prevention System is going to do all the things that an IDS does, but when it spots that malicious behavior, it's also going to work to block that traffic in an automated fashion.
Both these systems work on the principle of deep packet inspection. A couple of different kinds of IPS, we have network based IPS. We have wireless IPS also called WIPS, and we have host based IPS also known as HIPS. A network based IPS will monitor your entire network for suspicious behavior by analyzing protocol activity. Wireless IPS, WIPS, is going to work by analyzing your wireless networking protocols and then HIPS based IPS is a client based software and that's going to work to monitor that single host for any suspicious activity.
Your IPS is going to look for malicious behavior in two different ways. We have signature based detection, and that's going to be based off a dictionary of uniquely identifiable patterns also known as signatures. Then we've also got statistical anomaly based detection and what that's going to do is it's going to refer to an established baseline of normal behavior and if it sees something out of whack, it's going to look to drop that behavior in a number of ways.
Now, your IDS is going to alert your admin when it finds this behavior and you can set your IPS to do this as well but it can also go a step further where it can drop the malicious behavior either by resetting the connection, dropping the packet or finding that source IP and blocking that from sending any more inbound traffic.
For any information on Nexpose's integration with Sourcefire, you can visit rapid7.com.
Thanks for tuning in for this week's Whiteboard Wednesday, and we'll see you next week.