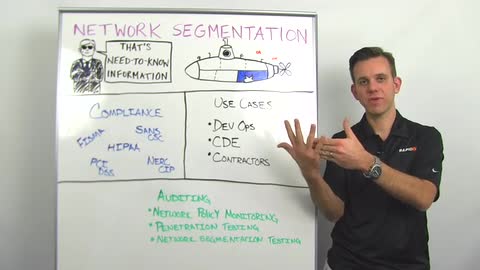
Today I'd like to talk about network segmentation. Network segmentation is when you break up a network into sub-segments for different purposes and you do that for two different reasons. First of all, you want to segment information on your network on a need-to-know basis, so that people don't have access to information, are not privy to information that they don't really need to have, security measure here.
The other reason is, let's say you have a breach in one area of the network. Through segmentation you can contain that breach and make sure that it doesn't effect other parts of the network. A good analogy here is a submarine where you have the different compartments inside the submarine to ensure that if you have a leak in one compartment, it doesn't flood the entire ship.
Network segmentation is actually a security best practice and that's the reason why it's found its way into many compliance regulations. For example, we find it in FISMA compliance, SANS Critical Security Controls, HIPAA compliance, PCI-DSS compliance and NERCSIP compliance. They're many different use cases of why you may want to segment one part of the network versus another. One example here is dev ops. You might have a certain web service that you're developing and you have your engineering department that develops that service and pushes new versions of that service online all the time. Now what you want to avoid, especially if you are running maybe an online store that processes credit card information or medical records, you want to ensure that the engineers don't have access to the production environment that actually holds sensitive data, so that's an example where you want to segment the network.
Number two is CDE, Cardholder Data Environments. Here, for example, ensuring that the person in the call center, taking certain payments or working on customer billing, can not access the credit card data containing all of the information there and you might want to segment because of that. Contractors, we learned from the Target breach that an HVAC vendor, was external to Target, had credentials to access the network to service the HVAC systems. However, when those credentials got compromised the attacker was able to not only get into the HVAC systems but actually break out of that network segment and get into the credit card, the segment holding the credit card data.
What can you do to protect yourself? First of all, setup network segmentation. It's a very good idea, you probably have a lot of the tools that you need to do that already. Once you've set that up, you should do a few things for auditing, because it's quite easy to make mistakes as you're setting up your network segments. Number one, you can do network policy monitoring. That means, for example, monitoring and alerting if anybody from engineering is accessing a network production segment, or if somebody from the call center is trying to get to the credit card data, or if one of your contractors from the HVAC center is accessing other parts of the network. Now, we have a new feature in user insight, for example, that does exactly that, alerts you went these network policies are broken.
Number two is, penetration testing. You simply hire an ethical hacker or maybe you have somebody in-house that does red teaming and you have them start in one network segment and have them break out of that segment into another segment. See whatever methods they can use to do that. Metasploit Pro can help you with that but obviously you need somebody who's skilled in the art for that.
Another area that's a little more processed driven and a little easier to do on a regular basis is network segmentation testing. This is also a feature that we have in Metasploit Pro. Where you basically set up one target server and a source server and you test out all the firewall ports in between to see what the connectivity is between two network segments, to see if that aligns with what you've spec'd out in your security policy.
All right, that's it for today for network segmentation and I'll hope to see you next week.