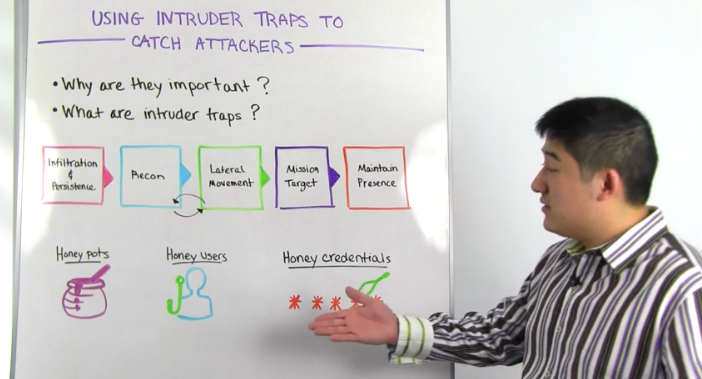
So for starters, why do you need intruder traps? Let's reference the attack chain, a graphical depiction of the steps required to breach a company. For every attack, whether it's the exploitation of a vulnerability, malware or the use of stolen credentials, attackers must follow this general flow. An attacker typically gains foothold on an initial machine, performs reconnaissance to find next targets, and then laterally moves to his or her final objective. If you can find and stop the attack earlier in the chain, you can kick intruders out before they reach your critical assets, whether it be proprietary specs, financials or customer data. The challenge is that detecting earlier in the attack chain is very hard to do when simply analyzing your log data.
You may already have detections in place if there's unauthorized access to your critical assets, but that means the attacker is already at mission target. With intruder traps you can detect attackers in the reconnaissance and lateral movement stages, and give your team more time to respond. Let's take a look at three example traps that you can look to deploy in your environment. The first is the well-known honey pot. So honey pot is typically a virtual machine on your network tasked with one job, determining if someone is scanning the network. Network scanning is a very common step during attacker reconnaissance, and tools, such as end map, are staples in every penetration tester's tool kit.
As part of Rapid7 research, we've set up a number of honey pots publicly accessible on the internet that attackers try to log on to every day. Those thousands of opportunistic, unauthorized authentications provide significant insight in to the passwords attackers are using, and the frequency and tendencies in their methods. So if this piqued your interest, certainly check out our report on these findings, The Attackers Dictionary, and the link is available below.
The second trap you can consider is a honey user. So this is a dummy account that you create an active directory. So you can name it something attractive like Patch Admin. And so if an attacker enumerates your active directory and attempts to authenticate to Patch Admin, set up an automatic alert. So this can catch unauthorized lateral movement, and is a telltale sign that someone is up to not good. Ideally this can be paired with local visibility on to your endpoint authentications so you know what user attempted to log in as the honey user. That user is likely compromised or could be an insider threat.
Finally, we have a cool new trap to share with you here at Rapid7 called Honey Credentials. When we log on to an endpoint, that password we use is stored locally on the machine in the form of a password hash. That's why you can still log on to your laptop even if you're not connected to the internet. If an attacker has control of your endpoint, he or she can directly extract that hash to attempt authentication elsewhere or by using tools like Mimikatz or password cracking, derive the clear text password from the hash itself.
On a more dangerous level, if IT has logged on to your laptop previously that password is also hashed and available for misuse. And so this credential is typically the domain admin password, the master key that allows authentication to any machine on the entire corporate network. So our approach to combating this is through our continuous endpoint agent which monitors key pieces of information on those endpoints and alerts on anomalous lateral movement. On top of that we inject fake credentials on to each of those endpoints so that hash or credential doesn't provide access to any system, so it's very safe to use. However, if anyone attempts to use that hash on your network, your team is automatically alerted.
Intruder traps are an innovative way to reliably detect malicious behavior on your network. If you're interested in monitoring your ecosystem without it becoming a second full-time job, check out our full detection and investigation solution inside IDR. In the meantime, are you using any trickery to find bad activity on your network? Let us know, we'd love to learn more. That's it for this week. Looking forward to seeing you at the next Whiteboard Wednesday.