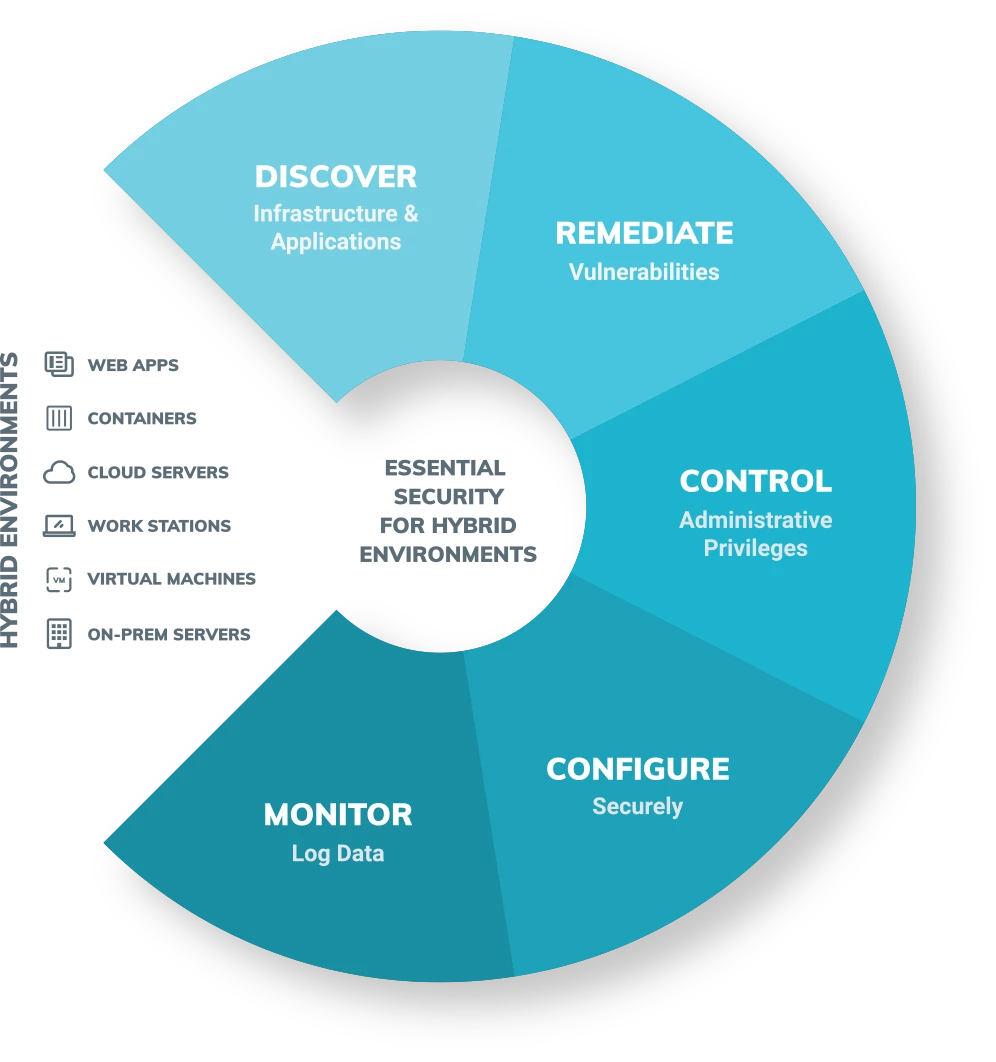
New technologies, such as containers and serverless functions, have left security teams with a new landscape that combines the best of cloud and on-prem. While this may seem like a daunting environment to secure, you’ll be off to a great start if you stick to the fundamentals.
We’ve outlined five fundamentals for securing a hybrid environment that align with the “Basic” category of CIS Critical Security Controls.
CIS Top 20 Critical Security Controls
Prioritize your security program for effectiveness against real world threats
Learn MoreSecuring your AWS environment?
See how our vulnerability management and automation integrations can help.
Learn more1. Discover infrastructure and applications
Security fundamentals often start with taking inventory of everything that needs protecting. When this includes ephemeral assets that quickly disappear, security solutions that dynamically discover and assess assets as they come online can help manage risk when keeping inventory isn’t as straightforward.
Read about more efficient and effective ways to remediate vulnerabilities:
- Discover Docker hosts, images, and running containers
- Identify web apps
- Identify VMs, network devices, and endpoints
- Automate actions upon discovery
2. Remediate vulnerabilities
The scope of vulnerability management grows in a hybrid world. On-premises assets are now just one component of your environment as cloud infrastructure and applications introduce potential vulnerabilities in things like container images and software packages. Approaching on-premises and cloud vulnerability management separately can make it difficult to prioritize vulnerabilities, so teams should consider solutions that address the hybrid environment as a whole.
Read more about how you can remediate vulnerabilities across cloud and on-prem:
- Identify vulnerable software packages
- Find vulnerabilities created by insecure code design
- Prioritize vulnerabilities across cloud and on-prem
- Automate alerts and stages of remediation
3. Control administrative privileges
With phishing attempts among the most common attack types, properly managing administrative privileges has always been important. Because admin privileges for cloud infrastructure are often shared across DevOps teams, managing those privileges becomes even trickier for the security team. For this reason, monitoring user behavior for indicators of stolen credentials is vital for hybrid environments.
Read more about how to control administrative privileges:
- Detect attacks targeting employee credentials
- Detect attacker tactics and techniques
- Protect web apps from account takeover
- Track access across cloud and on-prem
4. Configure securely
Given its degree of configurability, misconfigured cloud infrastructure is now a primary attack vector. When securing hybrid environments, assessing cloud configuration cannot be overlooked.
Read more about configuring securely across your stack:
- Assess cloud environments for misconfigurations
- Identify misconfigurations across web apps
- Monitor servers and workstations for misconfigurations
- Automate configuration fixes
5. Monitor
Collecting log data can provide a strong basis for building a security program. But cloud assets, especially ephemeral ones, can make log collection challenging. This is simplified by approaching log management holistically and seeking to centralize logs from on-premises and cloud in a unified view.
Read more about how you can collect and consolidate logs, even from your cloud assets:
- Collect logs from cloud, containers, and web apps
- Collect logs from servers and workstations
- Centralize cloud and on-prem logs in a unified view
- Automate actions based on specific log events or trends
Reduce risk across your entire connected environment
Get started with Rapid7 today.