On October 20, 2009 -- five years ago today -- Rapid7 acquired Metasploit. At the time, there was skepticism about the deal, and what it would mean for Metasploit and the open source community. The skepticism was, of course, fair. If Rapid7 was going to fund (and therefore, control) the development of the Metasploit Framework, why would anyone contribute to it any more? Why give away work product for free when Rapid7 is just going to turn around and sell it?
Today, Metasploit is still actively maintained by both paid Rapid7 software engineers and a small army of volunteer, open source contributors from around the world. In 2009, there were a grand total of 17 people who committed to Metasploit. This year alone, we've seen about 150 people contribute something to Metasploit. In fact, of the 400 or so contributors over the entire life of Metasploit, nearly half of them have committed something in the last 12 months. Check out the GitHub contributor graph, noting the pre- and post-acquisition volumes:
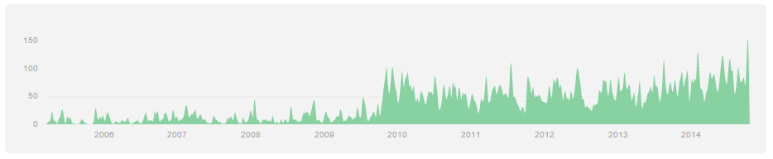
That couldn't have happened without not only Rapid7's support, but your support. Why do you, the open source contributor, do this? Well, that leads to the other fear at the time: once Metasploit came under the control of The Man, developed by Full Time Employees, who are Paid With Money, surely the next logical step was to turn Metasploit closed source -- or worse, crippleware, used only as a shingle to sell some weaksauce Metasploit Professional product that Real Hackers wouldn't ever use anyway.
That didn't happen either. When I started at Rapid7, shortly after the acquisition, I was hired to work on the proprietary side of Metasploit development, tasked with building out the first commercial Metasploit offering, Metasploit Express. When I started, I was just as worried that Metasploit's open development would dry up, the contributors would flee, and the massive open source user base would find something else to develop and deliver their exploits with.

Nope. It became obvious that Rapid7, from the top down, was and remains fully committed to the open source nature of Metasploit. In fact, it would be product suicide not to. Without the constant firehose of input from researchers, hackers, hobbyists, and IT pros from around the world, there would be no way Metasploit could stay relevant. We're committed to making Metasploit Framework better than ever, with more exploits, more features, and increasing coverage for all sorts of targets, from IoT devices to mainframes.
Today, tons and tons of people still use and still contribute to the Metasploit Framework. They use it for free, and they contribute for free, and that seems to be working out pretty well for both Rapid7 and the Internet at large. Obviously, Metasploit Pro brings a lot of extras to the table that are pretty valuable for the professional penetration tester and red-teamer. However, it's the open source core of Metasploit that has become the lingua franca for writing and expressing reliable and repeatable exploit code for the good of the Internet.
My own five year anniversary at Rapid7 is coming up here in just a couple months, and I feel like I've spent my working and playing time productively to help make the Internet -- and therefore, the world -- a better place. I know I'm lucky to be in that position. My job depends on all of you who use and make Metasploit what it is. So, thanks a lot for keeping me employed, and for keeping important security software open and free. This project wouldn't have gone anywhere without you.
